Checking a downloaded file’s hash (checksum) allows verifying its integrity and ensuring that the file contents have not been modified. Administrators commonly use MD5/SHA256 checksum verification for downloaded OS distros and software installation images.
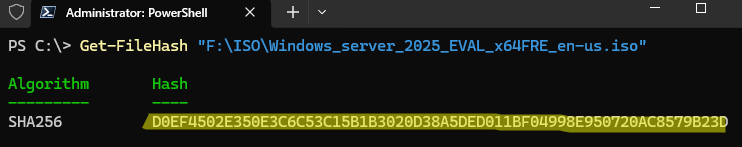
To verify a file’s hash in Windows, use the built-in Get-FileHash PowerShell cmdlet or the certutil command.
Get-FileHash "F:\ISO\Windows_server_2025_EVAL_x64FRE_en-us.iso"
After some time, the cmdlet returns the file’s checksum using the SHA-256 algorithm (by default). Calculating the hash sum can take some time depending on the file size. The -Algorithm attribute allows to switch to a different checksum algorithm.
- SHA1
- SHA256 (default) – the most popular hash algorithm with the lowest probability of collision (when two different files have the same checksum)
- SHA384
- SHA512
- MD5 – the fastest but outdated hashing algorithm
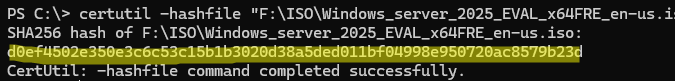
Similarly, you can get the file’s hash using certutil.exe:
certutil -hashfile "F:\ISO\Windows_server_2025_EVAL_x64FRE_en-us.iso" SHA256
Where to get the original Microsoft/Windows ISO image checksums?
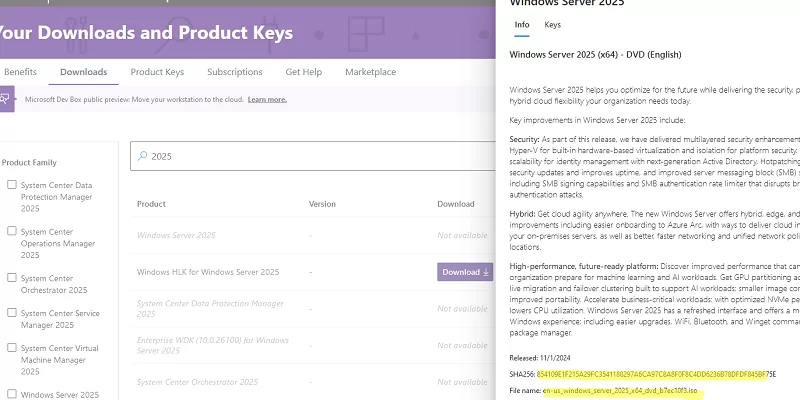
If you have a Microsoft account, you can find the Windows image ISO checksums at https://my.visualstudio.com/Downloads. It doesn’t require an active MSDN subscription. Image checksum information is available on the Product info tab.
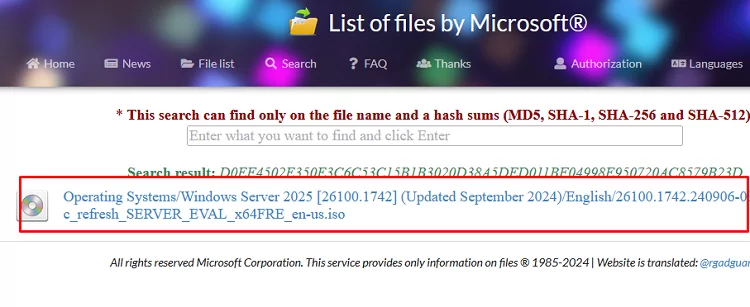
The following third-party online database also contains a list of all of Microsoft’s original images and their hashes https://files.rg-adguard.net/search. In contrast to the Microsoft site, this website allows to search for ISO images by their hash values. Search the resulting hash to make sure that you have downloaded the original ISO image file.
To automate the process of checking the hash sum of the downloaded image against the original value, use the following PowerShell one-liner:
((get-filehash .\Windows_server_2025_EVAL_x64FRE_en-us.iso).hash) -eq "D0EF4502E350E3C6C53C15B1B3020D38A5DED011BF04998E950720AC8579B23D"
The command returns True if the file checksum matches the reference value.