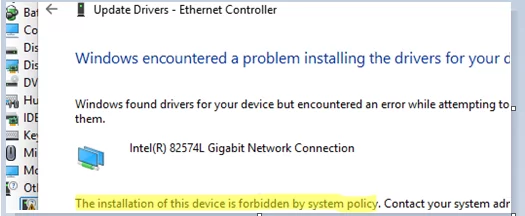
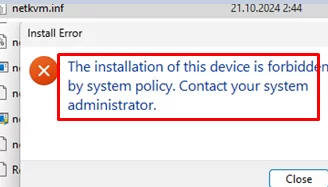
The installer may return the following error when installing the driver manually from an INF file or via an MSI/EXE package:
Windows found driver for your device bat encountered an error then attempting to install them. The installation of this device is forbidden by system policy. Contact your administrator.
This error may occur during the installation of various types of drivers, including network adapters, USB devices, printers, etc.
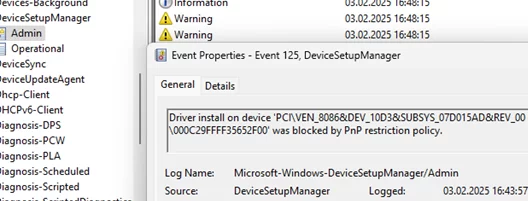
In this case, warnings with code 125 will appear in the Event Viewer under the Application and Services Logs > Microsoft > Windows > DeviceSetupManager > Admin. These warnings will include the device identifier in the VEN_ID & DEV_ID format and the following message:
Driver install on device PCI\VEN_8086&DEV_10D3&SUBSYS_07D015AD&REV_00\000C29FFFF35652F00 was blocked by PnP restriction policy.
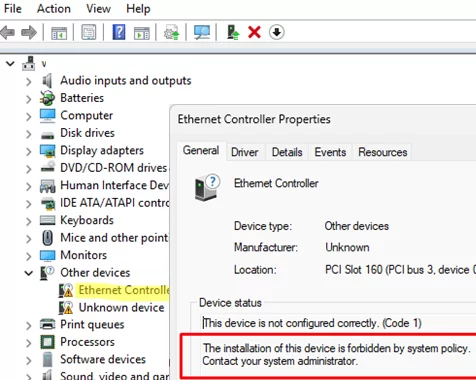
In this case, devices detected via Plug and Play (PnP) will appear in Device Manager with a yellow exclamation point and the error code:
The device is not configured correctly. (Code 1) The installation of this device is forbidden by system policy.
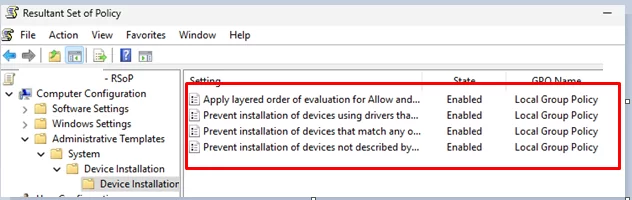
To identify active restrictive policies on a computer, generate and review the Resultant Set of Policy (RSoP) report by running the rsop.msc command.
Go to Computer Configuration -> Administrative Templates -> System -> Device Installation. In my example, several policy options have been enabled to restrict driver installation. The Local Group Policy label in GPO Name indicates that these settings were enabled using the local GPO editor.
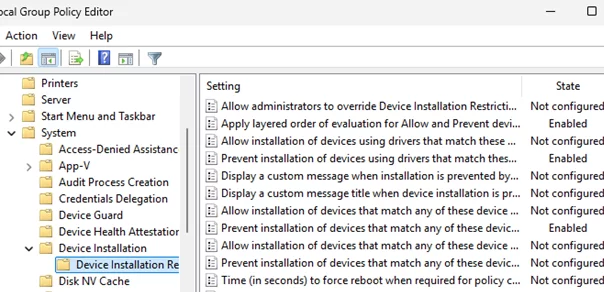
Open the gpedit.msc snap-in and navigate to the specified GPO section. Disable all restrictive policies by setting their values to Not set. For example:
- Prevent installation of devices that match any of these device instance IDs – deny driver installation for specific devices based on their VEN and DEV identifiers (Learn how to identify an unknown device by its VED/DEV ID)
- Prevent installation of devices that match any of these device IDs
- Prevent installation of devices using drivers that match these device setup classes – deny installation for entire classes of devices by their GUID (e.g., network adapters, video cards, audio cards, scanners, etc.)
- Prevent installation of removable devices – deny the installation of drivers for removable devices (usually USB).
- Prevent installation of devices not described by other policy settings – installation of any drivers not described in the Allow policies is prohibited.
After disabling the restrictive policies, run the gpupdate /force command to update the GPO settings. After this, you will be able to install the drivers.
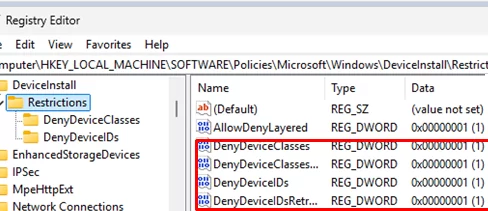
If the above settings have not been configured through Group Policy and the option to deny driver installation is active in Windows, check if the restrictive settings have been enabled directly through the registry. Run the regedit.exe and go to HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\DeviceInstall\Restrictions.
If device installation restrictions are enabled on the computer, this registry key will contain parameters with names like DenyUnspecified, DenyDeviceClasses, DenyDeviceIDs, and so on. To disable the restrictions, either change the parameter value from 1 to 0, or delete it completely. In such cases, the DenyDeviceClasses and DenyDeviceIDs registry subkeys may contain a list of specific device class GUIDs or hardware IDs that are blocked from installation.
To remove all device installation restrictions, you can delete the Restrictions registry key entirely.