Random hardware addressing feature in Windows 10 and 11 enhances privacy and security by generating a unique, randomized MAC address for each Wi-Fi network connection. This feature’s main purpose is to increase user privacy and anonymity by reducing the ability to track devices and collect user behavior data on public Wi-Fi networks. When enabled, a unique, randomly generated MAC address is used to connect to each Wi-Fi network instead of the physical hardware MAC address of the wireless adapter.
In Windows, you can enable or disable MAC address randomization either for a specific Wi-Fi network or for all wireless networks.
- Go to Settings -> Network & Internet -> Wi-Fi
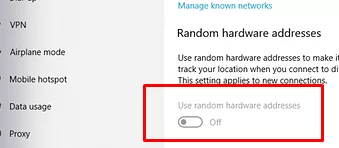
- Enable or disable MAC address randomization by pressing the Use random hardware addresses toggle.
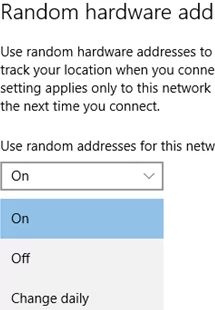
On my Windows 10 laptop, there is an option to generate a new, unique MAC address every day.
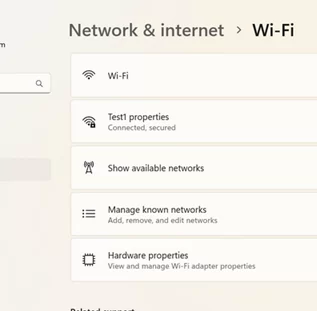
This option is also available in the settings for each saved Wi-Fi profile. Press Manage known networks -> select the saved WLAN network (profile) and enable/disable the Use random hardware addresses switch.
This is usually caused by:
- Not all Wi-Fi adapters support MAC address spoofing.
- This feature is not supported by the installed wireless driver. Try to download and install the latest driver version for your Wi-Fi adapter.
Using random MAC addresses usually only makes sense for public Wi-Fi networks. However, this feature may cause problems when used in corporate or small office/home office (SOHO) wireless networks.
- If the DHCP server has reserved an IP address for your device’s MAC address, using a random MAC address will prevent you from obtaining that static IP address.
- If a Captive Portal is used for Wi-Fi device authorization, you may face different connection issues.
- Filtering access by MAC address on the network will not work properly.
- It’s harder for administrators to track devices with random MAC addresses on the network
- Some software licenses may be tied to a computer’s physical MAC address.
For devices on a corporate network, administrators usually disable the random hardware address feature. The built-in Windows Group Policy templates don’t provide an option that allows disabling the use of random hardware (MAC) addresses. However, it can be disabled through the registry.
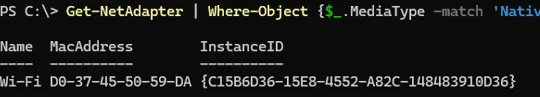
Get the ID and MAC address of your Wi-Fi adapter:
Get-NetAdapter | Where-Object {$_.MediaType -match 'Native 802.11'}| select Name, MacAddress,InstanceID
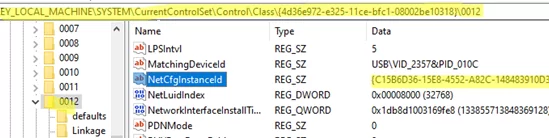
Open the registry editor and navigate to HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Class\{4D36E972-E325-11CE-BFC1-08002BE10318}. Search the subkeys for your WIFI_InstanceID (contained in the NetCfgInstanceId value).
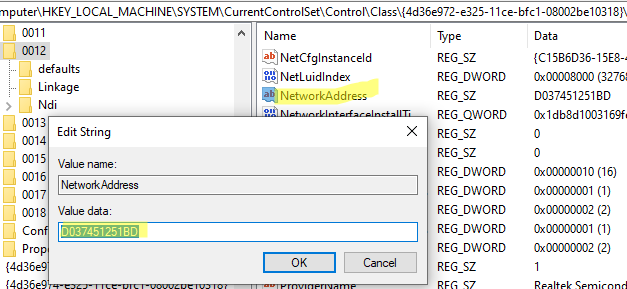
Create a REG_SZ parameter named NetworkAddress in this registry key. Specify the actual MAC address of your Wi-Fi adapter in the value of this parameter. In my example, the MAC address of the wireless adapter is D0:37:45:12:51:BD. However, when adding it to the registry, it must be entered without hyphens or spaces.
Restart the computer and check that the option to use a random MAC address in the Control Panel is now grayed out (inactive).
To automatically disable this option, you can use the following PowerShell script:
$WiFi = Get-NetAdapter | Where-Object {$_.MediaType -match 'Native 802.11'}
$RegPath = "HKLM:\SYSTEM\CurrentControlSet\Control\Class\{4D36E972-E325-11CE-BFC1-08002BE10318}"
$MacAddress = $WiFi.MacAddress -replace "[:\-]", ""
$subKeys = Get-ChildItem -Path $RegPath
foreach ($subKey in $subKeys) {
$props = Get-ItemProperty -Path $subKey.PSPath -ErrorAction SilentlyContinue
if ($props -and $props.DriverDesc -eq $WiFi.InterfaceDescription) {
New-ItemProperty -Path $subKey.PSPath -Name "NetworkAddress" -Value $MacAddress -PropertyType String -Force
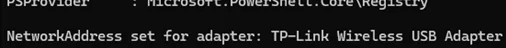
Write-Host "NetworkAddress set for adapter: $($WiFi.InterfaceDescription)"
break
}
}
This PowerShell script can be run on users’ computers via a Group Policy, SCCM, or other automation tools.
hide:ms-settings:network-wifi option).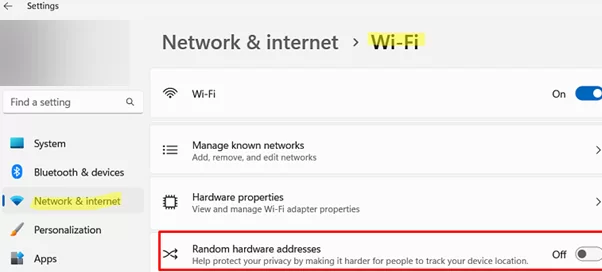
1 comment
Hallo User und pc friends,
Also ich habe mal nachgeschaut, nach dieser Funktion an / aus ( zufällige Hardwareadresse ).
Und bei mir kann ich das einfach an.- und ausschalten.
Und gelernt habe ich dabei, daß wenn etwas wichtig ist, wird es in der PowerShell, grade was Verbindungstechnik angeht, ziemlich
aufwendig und unübersichtlich.
Deshalb “danke” für diese einfache anwendbare Lösung.
MfG