SSL (TLS) certificates are a critical part of modern infrastructure, so administrators must ensure they do not expire and are renewed on time. This article shows you how to use Zabbix to monitor your websites for expiring SSL certificates.
In previous versions of Zabbix, to monitor the expiration of SSL certificates, you had to use console scripts that passed values to Zabbix via the UserParameter. Zabbix Agent 2 allows you to check the information on the certificate using the built-in WebCertificate plugin. This article will look at both ways of monitoring SSL certificate expiration in Zabbix.
Check SSL Certificate Expiration Using WebCertificate Plugin on Zabbix
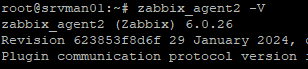
Zabbix Agent 2 includes a built-in WebCertificate plugin that allows you to check website certificate information. Check that this version of the agent is installed on the host:
$ zabbix_agent2 -V
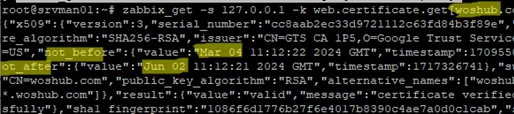
You can use the WebCertificate plugin to get information about the site’s certificate directly from the console using the zabbix-get command:
$ zabbix_get -s 127.0.0.1 -k web.certificate.get[woshub.com,443]
The command should return a JSON object that contains the attributes of the certificate for the specified Web site.
A built-in template “Website certificate by Zabbix agent 2” is available in Zabbix. Use it to check the TLS/SSL certificate expiration date.
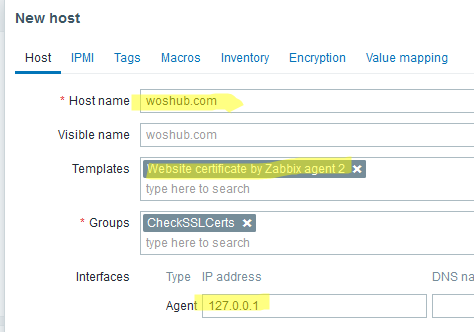
- Go to Configuration -> Hosts and add a new host with the website name;
- Create a new host group or select an existing one;
- Assign the template Website certificate by Zabbix agent 2;
- Specify the IP address or name of the Zabbix agent in the Interface section (in our example,
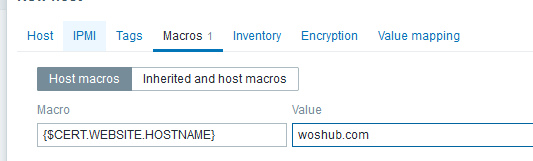
127.0.0.1); - Then go to the Macros tab and click Inherited and host macros;
- In the
{$CERT.WEBSITE.HOSTNAME}macro, specify the DNS name of the Web site whose certificate you want to check; - By default, a warning that an SSL Certificate is about to expire will be displayed 7 days before the expiration date. You can increase this value with a macro
{$CERT.EXPIRY.WARN}; - If the website uses a TLS/SSL port other than 443, you can specify it using a macro
{$CERT.WEBSITE.PORT}; - Save settings.
Zabbix now warns you when a site’s certificate is about to expire.
Monitor HTTPS Certificate Expiry with Script in Zabbix
You can use external scripts to retrieve certificate expiry information in previous versions of Zabbix. The openssl command line tool allows you to extract website certificate information.
Create a bash script file /usr/lib/zabbix/externalscripts/sslcert_expiration.sh with the following code::
#!/bin/bash
data=`echo | openssl s_client -servername $1 -connect $1:${2:-443} 2>/dev/null | openssl x509 -noout -enddate | sed -e 's#notAfter=##'`
ssldate=`date -d "${data}" '+%s'`
nowdate=`date '+%s'`
diff="$((${ssldate}-${nowdate}))"
echo $((${diff}/24/3600))
Allow the script to run:
$ sudo chmod +x /usr/lib/zabbix/externalscripts/sslcert_expiration.sh
This script returns the number of days left until the certificate expires. Check that the script works correctly.
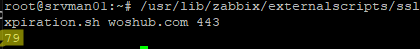
$ /usr/lib/zabbix/externalscripts/sslcert_expiration.sh woshub.com 443
The script returned that the site’s certificate is valid for the next 79 days.
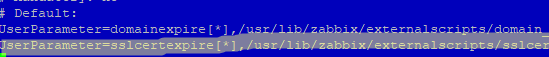
Now you must allow the Zabbix Agent to run this custom bash script using the UserParameter parameter.
$ sudo mcedit /etc/zabbix/zabbix_agent2.conf
Add:
UserParameter=sslcertexpire[*],/usr/lib/zabbix/externalscripts/sslcert_expiration.sh $1 $2
Restart the agent:
$ sudo service zabbix-agent2 restart
Check that the Zabbix agent can receive data via the new parameter. You can use the zabbix-get command to test the agent’s response:
$ zabbix_get -s 127.0.0.1 -p 10050 -k sslcertexpire[woshub.com,443]
Now add a new template CheckSSLCertExpiration to monitor the expiration of HTTPS certificates in Zabbix.
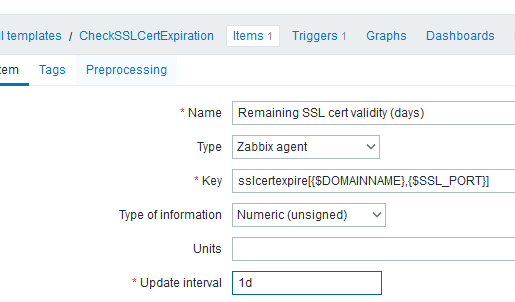
In the Items tab, add a parameter
- Name: Remaining SSL cert validity
{$DOMAINNAME} - Type: Zabbix Agent
- Key:
sslcertexpire[{$DOMAINNAME},{$SSL_PORT}] - Type of information: Numeric (unsigned)
- Update Interval: 1d
- History: 90d
- Trenfd: 365d
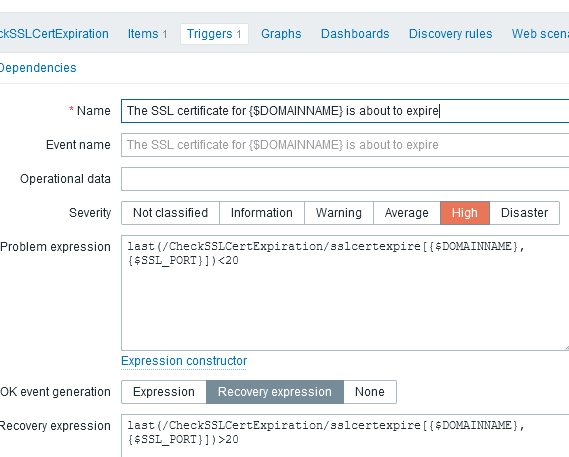
Then add a new trigger:
- Name: The SSL certificate for
{$DOMAINNAME}is about to expire - Expression:
last(/CheckSSLCertExpiration/sslcertexpire[{$DOMAINNAME},{$SSL_PORT}])<20 - Severity: High
This trigger will generate an alert if there are less than 20 days left before the SSL certificate expires.
You can add a recovery trigger parameter:
Recovery expression: last(/CheckSSLCertExpiration/sslcertexpire[{$DOMAINNAME},{$SSL_PORT}])>20
Now add a new host to Zabbix for your site with an Agent interface type.
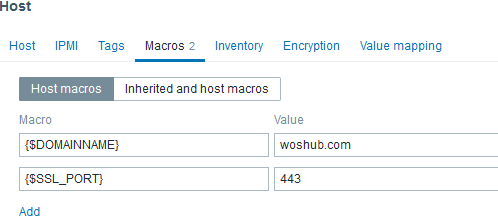
In the Macros tab, add two parameters: the name of the server and the port on which you want to check the SSL certificate:
- Macro:
{$DOMAINNAME} - Value:
woshub.com
and
- Macro:
{$SSL_PORT} - Value:
443
Assign the previously created CheckSSLCertExpiration template to the host.
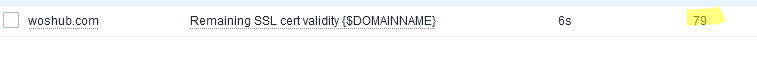
Now check the Latest Data. Zabbix shows that the site’s SSL certificate will expire in 79 days.
To notify the administrator that the SSL Certificate needs to be renewed soon, you can enable email or messenger notifications.