My task is to create multiple internal IP subnets and configure routing between them on my standalone Hyper-V stand. By default, Hyper-V doesn’t route traffic between networks on virtual switches. So to solve a task like this, you need to create a virtual machine with two network interfaces on different Hyper-V switches (in different networks) and configure routing between the interfaces using guest OS software (it may be either a VM running Windows Server with the RRAS role or a Linux host with a specific routing table). This method is not very convenient, because you have to run a separate VM for routing purposes only, and when adding a new IP subnet, you will have to reconfigure the routing table on your additional VM. However, I managed to figure out how to configure a Hyper-V host so that it could work as a router between different virtual switches/networks/IP subnets.
So, I have 2 virtual machines created in different internal networks on a Hyper-V host with the following IP addresses:
- mun-dc01:
192.168.13.11/24(gateway 192.168.13.1) - hh-dc02:
192.168.113.11/24(gateway 192.168.113.1)
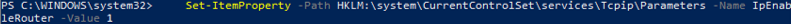
To allow routing on Windows Server, you must enable a special registry parameter — IPEnableRouter (it was discussed in the article on how to configure port forwarding in Windows).
Open PowerShell as an administrator on the Hyper-V host, edit the registry, and restart your host:
Set-ItemProperty -Path HKLM:\system\CurrentControlSet\services\Tcpip\Parameters -Name IpEnableRouter -Value 1
Restart-computer
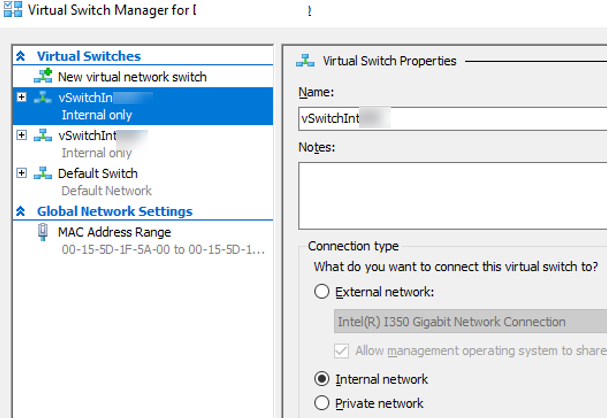
In the next step, create two new Hyper-V internal virtual switches. You can create them either in Hyper-V Manager or with PowerShell:
New-VMSwitch -Name vSwitchIntMUN -SwitchType Internal
New-VMSwitch -Name vSwitchIntHH -SwitchType Internal
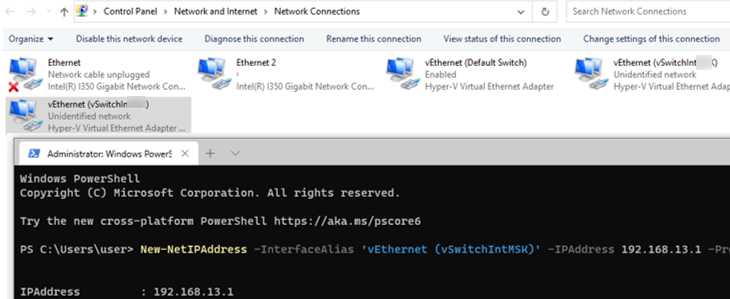
Then open Control Panel -> Network and Internet -> Network Connections on the Hyper-V host. You will see a list of network adapters on your host. There are two new virtual adapters (Hyper-V Virtual Ethernet Adapter) for the virtual switches you have created. Assign IP addresses to them using PowerShell or via the network adapter properties.
New-NetIPAddress -InterfaceAlias 'vEthernet (vSwitchIntMUN)' -IPAddress 192.168.13.1 -PrefixLength 24
New-NetIPAddress -InterfaceAlias 'vEthernet (vSwitchIntHH)' -IPAddress 192.168.113.1 -PrefixLength 24
As you can see, we have assigned the IP addresses of the default gateways on each subnet to these interfaces.
Connect each VM to its virtual switch (if you have not done it yet):
Connect-VMNetworkAdapter -VMName mun-dc01 -SwitchName vSwitchIntMUN
Connect-VMNetworkAdapter -VMName hh-dc03 -SwitchName vSwitchIntHH
Then your VMs will send traffic via these interfaces of virtual switches.
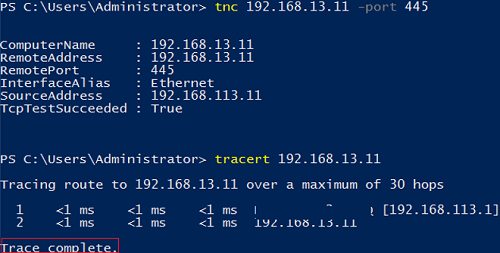
Make sure that Hyper-V virtual machines from different internal networks see each other. Check the routing using tracert and the port availability using the Test-NetConnection PowerShell cmdlet:
Test-NetConnection 192.168.13.11 -port 445
tracert 192.168.13.11
As you can see, the hosts are now responsible for ICMP ping and TCP. Note that Windows Defender Firewall settings in your VMs may block the traffic. Make sure you have allowed ICMP traffic in Windows Firewall and added other allowing firewall rules.
So, we have configured routing between multiple virtual networks on a Hyper-V host. The method is applicable for Hyper-V on Windows 10 and Windows Server 2016/2019.
3 comments
I’m looking for something which doesn’t appear to be on the net, maybe you could be the one to post the solution?
I setup a virtual-switch in hyperv:
New-VMSwitch -SwitchName “k-dmz” -SwitchType Internal
New-NetIPAddress -IPAddress 192.168.140.1 -PrefixLength 24 -InterfaceAlias “vEthernet (k-dmz)”
New-NetNAT -Name “k-dmz” -InternalIPInterfaceAddressPrefix 192.168.140.0/24
I can access VMs on this ip from the host system running hyper-v but cannot access the VMs from any other system on the local lan. I’ve tried adding routes to systems on the local lan, as well as setting up a route on the default gateway (router) of the local lan, and though it appears correct … tracepath reaches the hyper-v system and then reaches the vm, I cannot connect to the VMs from other systems on the local lan.
I’ve set the ‘IpEnabledRouter’ value in the registry, enabled the ‘Routing and Remote Access’, even installed ‘Remote Access’ feature, and then configured it by ‘Enable LAN Routing’. Still, no go. Not sure what else to try.
I have the samen no connection to the other subnet
Thank you, you have made what I wanted to achieve so very simple.