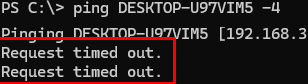
By default, the built-in Windows Firewall blocks incoming ICMP Echo Request packets for security reasons on Windows 10/11 desktops and Windows Server hosts. This means you won’t be able to remotely check the Windows computer availability using the standard ping command, as it will respond with Request timed out due to blocked ICMP Echo Replies. Suppose you need to check the availability of Windows hosts via ICMP (either from a monitoring system or manually from the command line). In that case, you can allow responses to ICMP echo requests in Windows Defender Firewall.
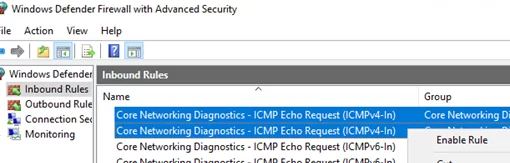
To allow responses to ICMP requests, enable the predefined rules for ICMP Echo in Windows Firewall.
- Open the Windows Defender Firewall with Advanced Security Management snap-in by running the
wf.msccommand - Go to the Inbound Rules section
- Find and enable the ‘Core Network Diagnostics – ICMP Echo Request (ICMPv4-In)‘ rule.
- There are two rules with that name in my case. One is for the private and public Windows network profile, and the other is for the domain profile. I’ve enabled both ICMP Echo Request rules. You can also enable the corresponding rule to allow ICMP echo replies over the IPv6 protocol if it is in use.
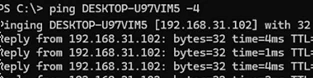
ping.Try pinging this computer to see if it now responds to ICMP echo requests.
Or use the following PowerShell command to enable the Windows Firewall rules that allow responses to ICMP echo requests
Set-NetFirewallRule -Name CoreNet-Diag-ICMP4-EchoRequest-In -enabled True
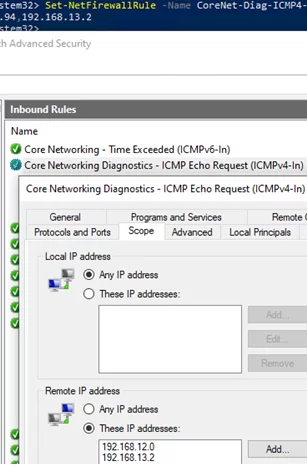
If you want to restrict which IP subnets or hosts are allowed to receive ICMP echo replies, use the following command to modify the firewall rule
Set-NetFirewallRule -Name CoreNet-Diag-ICMP4-EchoRequest-In -enabled True -RemoteAddress 192.168.31.0,192.168.13.2
Open the rule properties in Windows Firewall and verify that the ICMP Echo Reply rule is now configured to apply only to the specified IP addresses or subnets.
Here’s another PowerShell command example that creates a firewall rule to allow ping requests from all devices on the local network.
New-NetFirewallRule -DisplayName "Allow_ICMPv4_Echo_Response" -Direction Inbound -Protocol ICMPv4 -IcmpType 8 -RemoteAddress localsubnet -Action Allow
If you want to block ICMP echo reply responses regardless of existing rules, create a deny rule with a higher priority:
New-NetFirewallRule -DisplayName "Block_ICMPv4_Echo_Response" -Direction Inbound -Protocol ICMPv4 -IcmpType 8 -RemoteAddress localsubnet -Action Block
If the firewall rule for incoming ICMP echo requests is missing or has been removed, you can recreate it from the elevated command prompt:
netsh advfirewall firewall add rule name="llow_ICMPv4_Echo_Response" protocol=icmpv4:8,any dir=in action=allow
To allow ICMP ping responses on all computers on the network, you can enable this Windows Firewall rule through a domain Group Policy.
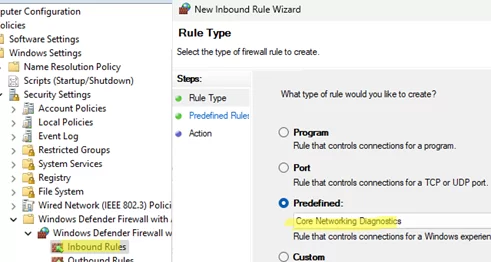
- Open the domain GPO editor (
gpmc.msc), create or edit an existing GPO, and link it to the target OU or domain root. - Go to Computer Configuration -> Windows Settings -> Security Settings -> Windows Firewall with Advanced Security -> Inbound rules
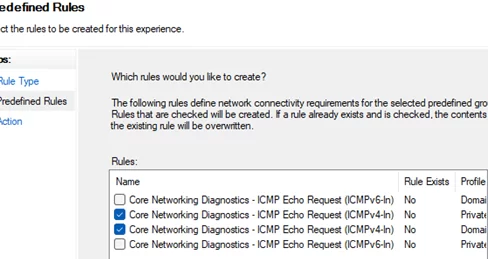
- Create a new rule, select a Predefined rule named Core Networking Diagnostics
- Choose which ICMP Echo Request rules you want to enable.
- Select Allow the connection in the next step.
- After updating the group policy settings on the client computers, the ICMPv4 Echo Request rule will be enabled on them. Users, including those with administrative privileges, cannot disable or delete a firewall rule deployed through Group Policy.