As part of phasing out insecure protocols, Microsoft has removed support for the deprecated NTLMv1 authentication protocol starting with Windows 11 version 24H2 and Windows Server 2025, encouraging the use of more secure alternatives like Kerberos. It is also planned that NTLMv2 will be deprecated in future releases of Windows.
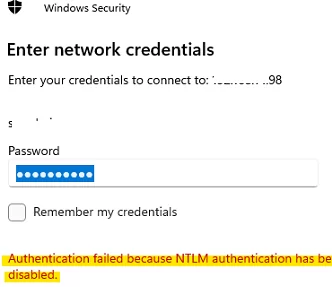
If a user attempts to connect to a remote computer or NAS device that only supports NTLMv1 authentication, an error message will appear.
Authentication failed because NTLM authentication has been disabled
In this case, in the Event Viewer, you can find events such as:
ERROR_NTLM_BLOCKED Error code: 1937 (0x791) Authentication failed because NTLM authentication has been disabled.
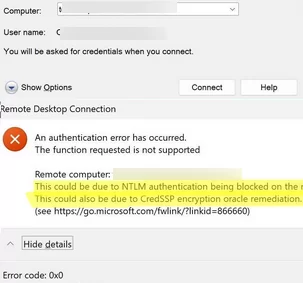
If you try to connect to a domain device running Windows 11 24H2 from a computer in a workgroup via RDP, you may receive the following error:
An authentication error has occurred. The function requested is not supported. This could be due NTLM authentication being blocked on the remote computer. This also be due to CredSSP encryption oracle remediation.
Lack of support for the NTLMv1 protocol may cause connection issues with devices that only support this outdated authentication method. Problems particularly occur with network drives that are mapped from Synology NAS and TrueNAS. In order to continue using such devices with Windows 11, you will need to configure them to use at least NTLMv2 (a firmware update may be required).
Auditing NTLMv1 Usage in Windows Environments
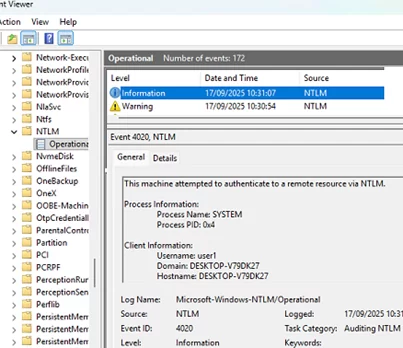
Enhanced NTLM authentication event auditing is now also available for Windows 11 24H2 and Windows Server 2025. A corresponding event is logged by Windows when NTLM authentication (v1 or v2) is used (Event Viewer -> Applications and Services Logs -> Microsoft -> Windows -> NTLM -> Operational).
The details of such events will contain:
- The user and the process on the computer attempted to use NTLM authentication.
- What version of NTLM was used
- The name and/or IP address of the remote device that requested NTLM authentication.
In my example, the NTLM authentication log contains informational messages about the use of the currently permitted NT LAN Manager version 2, as well as warnings if an attempt is made to use the obsolete NTLM1v1 version.
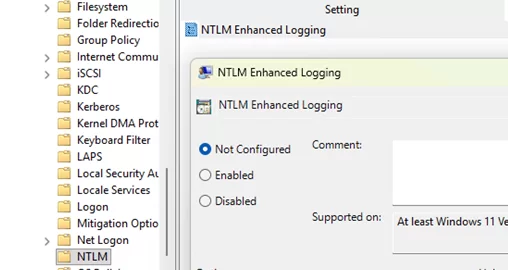
NTLM usage event collection is enabled by default. This auditing can be disabled through the NTLM Enhanced Logging option in the GPO editor (Administrative Templates -> System -> NTLM).
On AD domain controllers, this Group Policy option is Log Enhanced Domain-wide NTLM Logs.
However, NTLMv1 can still be used for authentication in some legacy cryptographic algorithms in Windows, for example, MS-CHAPv2 in an AD domain. Microsoft recommends enabling Credential Guard on devices in order to protect legacy protocols that use NTLMv1.
Microsoft has published a roadmap for disabling NTLMv1 on devices where Credential Guard is disabled, gradually rolling out auditing and enforcement changes starting with Windows 11 version 24H2 and Windows Server 2025 to enhance security by phasing out legacy protocols.
According to this roadmap:
- NTLMv1 usage auditing was enabled in August 2025 (Event ID: 4024)
- These changes will be implemented in Windows Server 2025 in November 2025.
- In October 2026, Microsoft will switch from audit mode to full enforcement, setting the default value to block the use of NTLMv1-derived credentials for Single Sign-On by default on devices where this setting has not been manually configured. This change will be implemented by setting the BlockNtlmv1SSO registry parameter. (
HKLM\SYSTEM\currentcontrolset\control\lsa\msv1_0), the value of which will be changed from 0 (audit mode) to 1 (Enforce).
Blocking NTLM Over SMB on Windows
Another change in Windows 11 (version 24H2+) and Windows Server 2025 relates to the use of NTLM for SMB authentication. It is now possible to disable the NTLM authentication protocol on the client side for outgoing SMB connections when accessing shared network folders and printers on remote computers.
Completely disable NTLM for the SMB client:
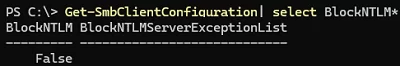
Set-SMbClientConfiguration -BlockNTLM $true
Or, you can disable NTLM for a specific mapped drive:
New-SmbMapping -RemotePath \\srv1\shared -BlockNTLM $true
or
NET USE \\srv1\shared /BLOCKNTLM
This prevents the SMB client from falling back to NTLM instead of using the more secure Kerberos protocol after negotiating the authentication protocol via SPNEGO (for example, this could happen when mapping a shared drive by IP address instead of the FQDN, or when connecting under a local account).
To allow using NTLM authentication only for certain devices, add their addresses to the exception list.
Set-SmbClientConfiguration -BlockNTLMServerExceptionList "192.168.123.12,*.woshub.com"
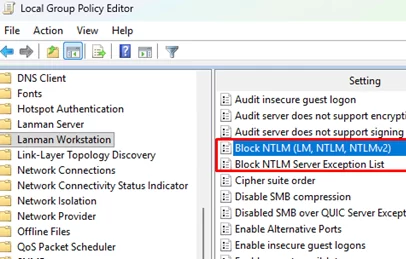
These settings can be applied via the Group Policy options under Computer Configuration -> Administrative Templates -> Network -> Lanman Workstation
- Block NTLM (LM, NTLM, NTLMv2)
- Block NTLM Server Exception List
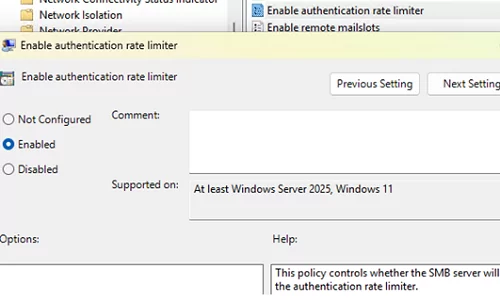
A new GPO option has been introduced that allows you to limit the time interval between failed NTLM authentication attempts when accessing a network folder. This parameter is called Enable authentication rate limiter (Computer Configuration -> Administrative Templates -> Network -> Lanman Server). This option protects the SMB server from brute force and dictionary attacks on shared folders by introducing a default 2-second (2000 ms) delay between each failed NTLM authentication attempt, significantly slowing down attack attempts