The security department has tasked my IT department with disabling PowerShell on certain computers. Users should be denied access to launch an interactive PowerShell console or execute PowerShell scripts. However, GPO logon scripts and PowerShell scripts in Task Scheduler (which run from the SYSTEM account) should still be allowed. This article will explore several methods for disabling PowerShell on computers, which can be implemented centrally via Group Policy.
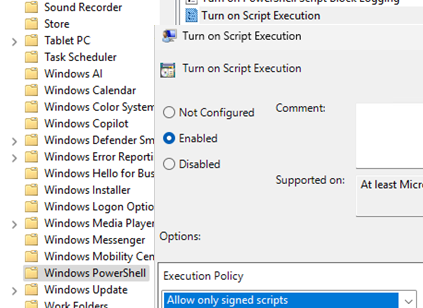
The default Windows PowerShell Execution Policy is set to Restricted, which only prevents *.PS1 script files from running (can be configured via GPO option Turn on Script Execution under Computer Configuration -> Administrative Templates -> Windows Component -> Windows PowerShell). However, it doesn’t prevent users from accessing the interactive powershell.exe console.
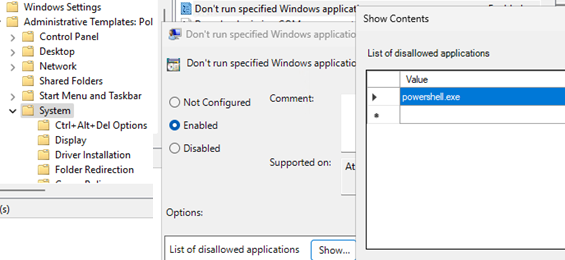
The GPO editor has a built-in policy option that lets you prevent certain executable files from running. This is policy Don’t run specified Windows applications in User Configuration -> Administrative Templates -> System. Enable the policy, click the Show button, and add the name of the executable file (powershell.exe) that you want to prevent from running.
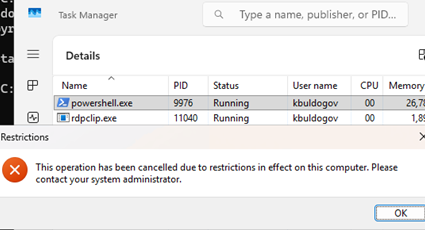
After updating the GPO settings on the client device, the following error will appear if the user tries to run powershell.exe:
Restrictions This operation has been cancelled due to restrictions in effect on this computer. Please contact your system administrator.
However, such a policy is not reliable and secure enough. For example, it didn’t prevent the launch of the Windows Terminal with a PowerShell session.
- x86 and x64 versions of
powershell.exeandpowershell_ise.exein%SystemRoot%\System32\WindowsPowerShell\v1.0\and%SystemRoot%\SysWOW64\WindowsPowerShell\v1.0\directories - If the new PowerShell Core version is installed on a computer, you must also prevent the
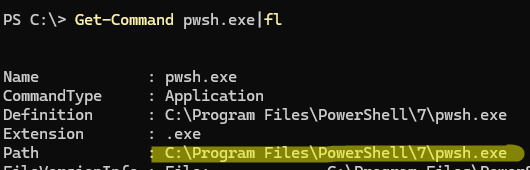
pwsh.exeexecutable from running. For example, in my case, this path isC:\Program Files\PowerShell\7\pwsh.exe(use this command to get the path to the executable:Get-Command pwsh.exe
You can set more flexible restrictions on running executable files using Software Restriction Policies (SRP).
- Create a new GPO in the AD domain using the
gpmc.mscconsole - Go to User Configuration -> Policies -> Windows Settings -> Security Settings -> Software Restriction Policies
- Select New Software Restriction Policy
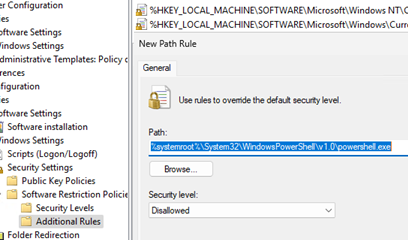
- Go to the Additional Rules section and add the following path:
%SystemRoot%\System32\WindowsPowerShell\v1.0\powershell.exe - Set Disallowed as the security level.
- Assign the policy to the target OU
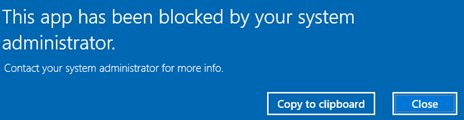
After the policy is applied, users will no longer be able to run PowerShell.exe.
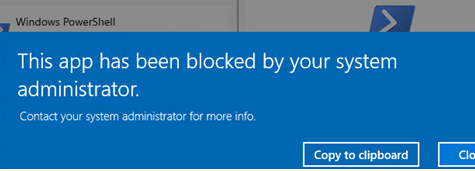
This app has been blocked by your administrator
This SRP policy also prevents users from running the PowerShell.exe process via the Windows Terminal.
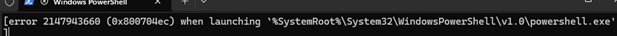
[error 2147943660 (0x800704ec) when launching `%SystemRoot%\System32\WindowsPowerShell\v1.0\powershell.exe']
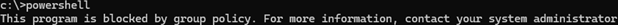
This program is blocked by group policy. For more information, contact your system administrator.
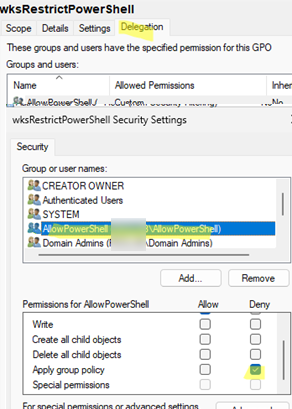
You can make an exception to the policy and allow certain users to use PowerShell. In this example, I created a security group in Active Directory (AD) named AllowPowerShell to which I added administrators who will be allowed to run PowerShell.
Then, open the Delegation tab in the policy settings in the GPMC console. I added this group with read access, but blocked the policy from applying: Apply Group Policy -> Deny.
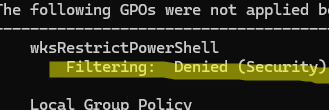
We prevented non-admin users from running PowerShell this way, but made an exception for the administrators. Similarly, this policy should not apply to the SYSTEM account. This will allow startup scripts and PowerShell scheduler tasks to run.
To verify that the GPO is not applied to administrators, use thegpresult /r command.
However, starting with Windows 10 1803 and Windows Server 2019, the Software Restriction Policies feature is considered deprecated. Instead, it is recommended to use Windows Defender Application Control (WDAC) or AppLocker restriction policies.
Next, we will look at how to use an AppLocker policy to deny the running of powershell.exe. Initially, AppLocker policies could only be applied to the Enterprise edition of Windows. Starting with Windows 10 2004, AppLocker policies can be applied to Pro editions of Windows 10 and 11.
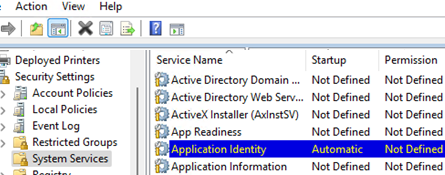
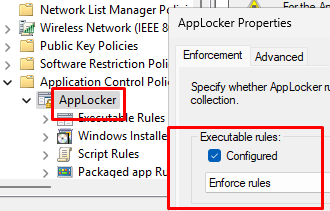
- To apply the AppLocker policy to the client device, enable the automatic startup for the Application Identity service (Computer Configuration -> Windows Settings -> Security Settings -> System Services)
- Then navigate to Computer Configuration -> Policies -> Windows Settings -> Security Settings -> Application Control Policies -> AppLocker. Open the properties and enable the Configured option under Executable rules. Set the mode to Enforce rules.
- Right-click on Executable rules and select Create Default rules.
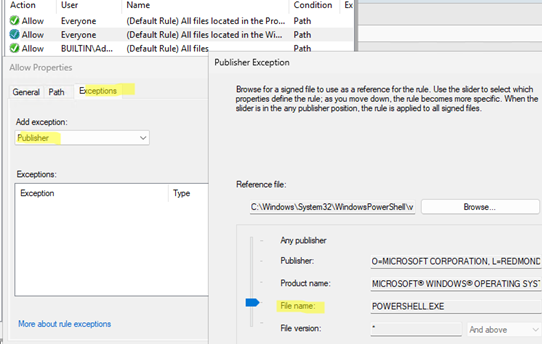
- In the “All files located in the Windows folder” rule, add a Publisher exception containing the path to the
powershell.exeexecutable. - Select the executable file and move the slider to File name
- This rule prevents users from running this file.
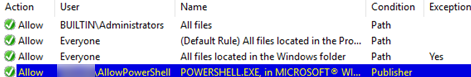
- To allow administrators to run powershell.exe, you need to create a new allow rule for them. This rule should contain only this file.
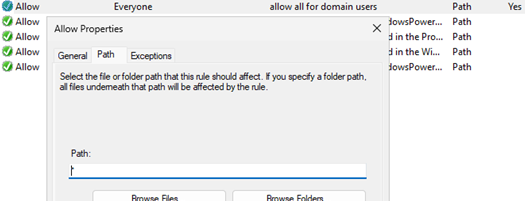
- Default Aplocker’s policies prevent users from running any executable files except those located in the Windows and Program Files folders. Therefore, if you want to prevent the launch of only PowerShell.exe, you need to add a rule that allows everything for domain users except PowerShell.exe (specify
*in the path field)
You can export the resulting AppLocker policy settings to an XML file to view them on a client.
Get-AppLockerPolicy -Effective -XML > C:\temp\applocker_result_policy.xml
When a user attempts to run PowerShell.exe on a client computer, a message appears informing them that the application has been blocked by the system administrator.
Likewise, the x86 and x64 versions of powershell.exe, powershell_ise.exe, and pwsh.exe should be blocked.