I encountered a strange issue where some users who upgraded their computers to Windows 11 25H2 reported that they could not connect to certain remote hosts over Remote Desktop Protocol (RDP).
Users were unable to establish an RDP connection in the following cases:
- If the account name for the RDP connection contains non-ASCII characters. This issue may occur on localized versions of Windows where the built-in Administrator account has a different name or uses usernames containing non-ASCII characters (for example, Cyrillic, Turkish, etc). In this case, the RDP logon attempt may fail due to an invalid credentials error.
- When connecting to a remote computer by its IP address. Meanwhile, the connection with the RDP host’s FQDN is established successfully. This clearly shows that connections using NTLM authentication (by IP address) were blocked, while connections using Kerberos authentication (via FQDN) worked without issues
- Computers are not joined to the same AD forest or are in different workgroups.
We spent considerable time investigating the issue by enabling KDC event logging. We discovered that the problems with RDP connections in Windows 11 are caused by Credential Guard (specifically, Remote Credential Guard). This security feature is designed to protect user credentials. Credential Guard is enabled by default on Windows 11 if the computer’s hardware meets certain requirements (TPM + UEFI + SecureBoot + Virtualization-Based Security).
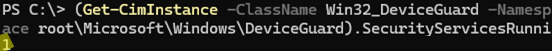
Check whether Credential Guard is enabled on a Windows 11 device using PowerShell:
(Get-CimInstance -ClassName Win32_DeviceGuard -Namespace root\Microsoft\Windows\DeviceGuard).SecurityServicesRunning
- 0 – credential protection disabled
- 1 – Credential Guard enabled
If Credential Guard is enabled on a computer without a UEFI Lock mode (protects against making changes to UEFI settings), you can disable this security feature either via GPO or through the registry:
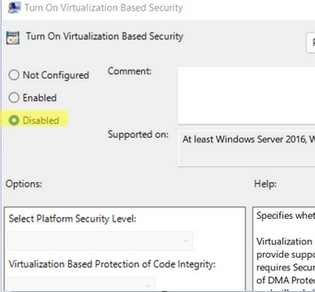
- Open the local GPO editor (
gpedit.msc) and navigate to Computer Configuration -> Administrative Templates -> System -> Device Guard. Change the value of the Turn on Virtualization Based Security option to Disabled. - Then create two registry items:
reg add HKLM\SYSTEM\CurrentControlSet\Control\Lsa /f /v LsaCfgFlags /t REG_DWORD /d 0
reg add HKLM\SOFTWARE\Policies\Microsoft\Windows\DeviceGuard /f /v LsaCfgFlags /t REG_DWORD /d 0
If the UEFI lock is enabled, you must first create a temporary boot entry in the BCD to start the computer in a mode that allows Credential Guard and Virtualization-Based Security to be disabled.
copy %WINDIR%\System32\SecConfig.efi X:\EFI\Microsoft\Boot\SecConfig.efi /Y
bcdedit /create {0cb3b571-2f2e-4343-a879-d86a476d7215} /d "DebugTool" /application osloader
bcdedit /set {0cb3b571-2f2e-4343-a879-d86a476d7215} path "\EFI\Microsoft\Boot\SecConfig.efi"
bcdedit /set {bootmgr} bootsequence {0cb3b571-2f2e-4343-a879-d86a476d7215}
bcdedit /set {0cb3b571-2f2e-4343-a879-d86a476d7215} loadoptions DISABLE-LSA-ISO
bcdedit /set {0cb3b571-2f2e-4343-a879-d86a476d7215} device partition=X:
mountvol X: /d
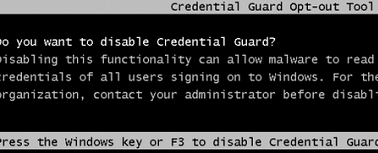
During a Windows boot, a console prompt (Credential Guard Opt-out Tool) will appear asking you to disable Credential Guard. Press F3 to confirm disabling.
After this change, Credential Guard will no longer block NTLM authentication when connecting to a remote computer over RDP.
The inability to connect via RDP for accounts with non-ASCII characters is caused by an ANSI translation bug in Credential Guard, which leads to failed authentication because Credential Guard incorrectly processes usernames containing such characters.