SMB over QUIC is a new feature available on Windows Server 2025 that allows you to configure secure access to a Windows file share over the Internet without using a VPN (it was previously available only in the Windows Server 2022 Azure Edition). In the past, accessing SMB file servers remotely required deploying an additional VPN or RDS solution. Now, with SMB over QUIC, you can securely access a file server directly from untrusted and public networks.
- The connection between the SMB server and user is protected by TLS 1.3 encryption with certificates. User authentication occurs within a secure TLS tunnel.
- UDP/443 is used instead of the traditional SMB port TCP/445.
- QUIC is a modern transport protocol that offers improved performance and resistance to poor network channels. It also includes a new compression algorithm.
- With QUIC Client Access Control, you can restrict access to a file server for clients using certificates.
- SMB 3.1.1 is used within the TLS tunnel.
SMB over QUIC is often referred to as an SMB VPN because it allows remote users to securely access a corporate file server over the Internet without the need for an additional VPN.
Let’s look at how to share a folder on a Windows Server 2025 file server via SMB over QUIC and provide secure access to it from clients using certificate authentication. Windows Admin Center (WAC) and PowerShell can be used to configure SMB over QUIC.
First, configure a file server on Windows Server 2025 with SMB over QUIC support. Although an Active Directory domain is preferred, SMB over QUIC can be configured for workgroup scenarios with local user accounts.
You need an SSL certificate containing the FQDN of your file server in the Subject Alternative Name (SAN). You can use a certificate from an external Certificate Authority, including a Let’s Encrypt certificate, a certificate from an internal CA, or a self-signed certificate, which is acceptable but not recommended. The certificate’s Enhanced Key Usage (EKU) field must include the use for Server Authentication.
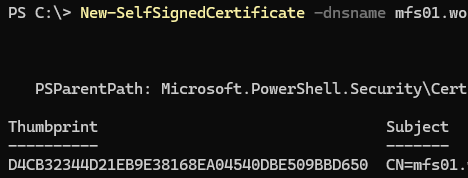
In this example, I will use a scenario with a self-signed certificate on the server. Generate a self-signed certificate for the file server’s FQDN.
$todaydate = Get-Date
$add3year = $todaydate.AddYears(3)
New-SelfSignedCertificate -dnsname mfs01.woshub.com -notafter $add3year -CertStoreLocation cert:\LocalMachine\My
Select a certificate by its fingerprint:
$cert=Get-ChildItem -Path "Cert:\LocalMachine\My" | Where-Object Thumbprint -eq D4CB32344D21EB9E38168EA04540DBE509BBD650
Assign the certificate to the QUIC SMB server.
New-SmbServerCertificateMapping -Name mfs01.woshub.com -Thumbprint $cert.Thumbprint -StoreName My
Enable support for SMB over QUIC for the file server.
Set-SmbServerConfiguration -EnableSMBQUIC $true
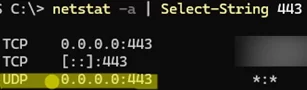
Verify that the SMB server is listening on UDP port 443.
netstat -a | Select-String 443
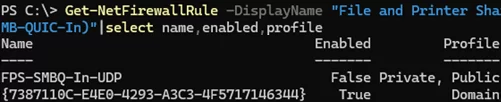
To allow access to a file share over SMB QUIC, the appropriate rules must be enabled in the Windows Defender Firewall:
Get-NetFirewallRule -DisplayName "File and Printer Sharing (SMB-QUIC-In)"|select name,enabled,profile
By default, SMB QUIC access is granted for the Domain profile, but it is denied for the Private and Public network profile types (enable the required rules depending on your environment).
Next, configure a connection to the SMB shared folder via QUIC on the client computer (the following operating systems are supported as clients: Windows 11, Windows Server 2025, and Linux with Samba version 4.23 or newer. However, Windows 10 doesn’t support the QUIC protocol.
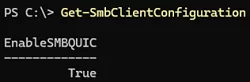
Check if SMB over QUIC support is enabled on the Windows 11 client:
Get-SmbClientConfiguration | select EnableSMBQUIC
Now you can map a shared folder from the file server using the New-SmbMapping PowerShell cmdlet:
New-SmbMapping -LocalPath W: -RemotePath \\mfs01.woshub.com\Docs -TransportType QUIC
Or using the net use command:
net use W: \\mfs01.woshub.com\Docs /TRANSPORT:QUIC
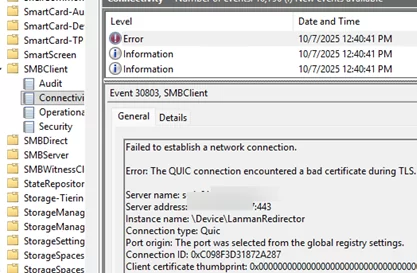
To ensure that the QIUC transport was used to connect a shared folder, check the Event Viewer logs on a client for Event ID 30832 (Event Viewer -> Applications and Services Logs -> Microsoft -> Windows -> SMBClient -> Connectivity).
The initial connection to the share was established. Share name: \xxxxx Server address: xxxxxxx:443 Session ID: 0x1900014000079 Tree ID: 0xD Transport type: Quic Signing used: true
If you see Event ID 30803 in the log, it most likely means that the server certificate is not installed on the client, or the client doesn’t trust it.
Failed to establish a network connection. Error: The QUIC connection encountered a bad certificate during TLS.
You can use Client Access Control rules to allow access to a server share via the QUIC protocol only if clients have the necessary certificates. Enable mandatory SMB client certificate authentication for connections to the file server.
Set-SmbServerCertificateMapping -Name mfs01.woshub.com -RequireClientAuthentication $true
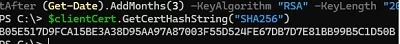
Let’s create a self-signed certificate on a client computer that is valid for three months.
$clientCert = New-SelfSignedCertificate -DnsName mfs01.woshub.com -CertStoreLocation "Cert:\LocalMachine\My" -NotAfter (Get-Date).AddMonths(3) -KeyAlgorithm "RSA" -KeyLength "2048"
Bind this certificate on the client device for use when connecting to the corporate file server:
New-SmbClientCertificateMapping -Namespace mfs01.woshub.com -Thumbprint $clientCert.Thumbprint -Store My
Get the SHA-256 hash of the client certificate.
$clientCert.GetCertHashString("SHA256")
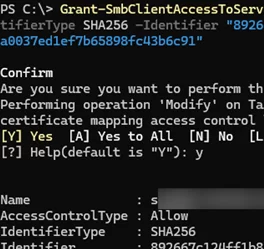
Allow connections from clients with this certificate on the SMB server with QUIC share (by its SHA-256 hash).
Grant-SmbClientAccessToServer -Name mfs01.woshub.com -IdentifierType SHA256 -Identifier "B05E517D9FCA15BE3A38D95AA97A87003F55D524FE67DB7D7E81BB99B5C1D50B"
To list all Client Access Control rules on a file server:
Get-SmbClientAccessToServer -Name mfs01.woshub.com
Or, you can allow connections from all clients with certificates from a specific publisher (specified in X.500 format). This CA’s root and intermediate certificates must be trusted by the SMB server:
Grant-SmbClientAccessToServer -Name mfs01.woshub.com -IdentifierType ISSUER -Identifier "<subject name>"
Enable auditing of certificate authentication events (Applications and Services Logs\Microsoft\Windows\SMBServer\Audit):
Set-SmbServerConfiguration -AuditClientCertificateAccess $true
As a result, only clients with approved certificates will be able to connect to your SMB file server.
With SMB over QUIC, all SMB traffic, including authentication, is fully encrypted. If a domain controller is unavailable for client authentication, then NTLMv2 authentication will be used instead of Kerberos authentication. This encryption protects NTLM authentication from being intercepted or harvested by attackers, ensuring that even when NTLM is used, the credentials and authentication process remain safeguarded inside the encrypted QUIC channel.
One drawback of the SMB over the QUIC protocol is that it doesn’t support legacy SMB clients, including Windows 10 and earlier versions, as well as Samba versions prior to 4.23.

10 comments
🗂 Windows Server 2025 introduces built-in support for SMB over QUIC. This feature enables users to securely access SMB file shares SMB file shares directly without requiring a VPN.
QUIC (Quick UDP Internet Connections) is a modern UDP-based transport protocol designed to reduce latency and improve connection reliability, useful for remote employees and mobile clients.
✅ Key advantages of SMB over QUIC
🔹 Uses QUIC instead of TCP for SMB transport
🔹 End-to-end TLS 1.3 encryption with certificate-based security
🔹 User authentication takes place inside an encrypted tunnel
🔹 Uses UDP/443 instead of TCP/445 (better firewall traversal)
🔹 Optional client certificate access control (QUIC Client Access Control)
🔹 Remote users can securely access corporate file shares without VPN, simplifying administration and reducing load on remote access infrastructure
🔹 Full Linux support beginning with Samba 4.23
📚 The referenced article covers:
✔️ Configuring SMB over QUIC on Windows Server 2025
✔️ Certificate binding and trust configuration
✔️ Windows 11 SMB client setup
✔️ Enabling certificate-based client authentication (server only accepts connections from certificates with a defined SHA-256 fingerprint or issued by a specific CA)
Does it make sense to deploy this internally too?
Is there any GPO we can use to configure the network drives on the clients via Quic?
there are several GPO options related to SMB over QUIC.
file server Enable SMB over QUIC (Computer Configuration\Administrative Templates\Network\Lanman Server)
client device Enable SMB over QUIC (Computer Configuration\Administrative Templates\Network\Lanman Workstation)
_https://learn.microsoft.com/en-us/windows-server/storage/file-server/smb-over-quic?tabs=windows-admin-center%2Cgrouppolicy%2Cgroup-policy1
Why hasn’t Microsoft enabled this for Remote Desktop Gateway? Since RDG relies on NTLMv2 for authentication using this would be more secure. MS is killing NTLM and wants to use only Kerberos, which doesn’t have line of sight to an RDG server.
In such cases, it is possible to deploy the KDC (Kerberos Key Distribution Center) proxy on an RDGW server.
The KDC Proxy is designed to enable Kerberos authentication in scenarios without direct line-of-sight to domain controllers, including RD Gateway deployments.
https://learn.microsoft.com/en-us/azure/virtual-desktop/key-distribution-center-proxy
Thanks admin!
Does that work with on prem RDG’s? I would LOVE to see a write-up on how to implement this.
Yes, the on-premises RD Gateway is compatible with the KDP Proxy. Unfortunately, Microsoft hasn’t documented it at all.
I will later update this post to include the steps for implementing KDC proxy for use with the RDGW.
You’re a Legend!
Is there a way to configure it using GUI instead of PowerShell?
SMB over QUIC can be enabled and configured via the Windows Admin Center (WAC) web UI.
https://learn.microsoft.com/en-us/windows-server/storage/file-server/smb-over-quic?tabs=windows-admin-center%2Cpowershell2%2Cwindows-admin-center1