In this article, we will review the purpose of domain controllers holding FSMO roles in Active Directory, how to identify the current FSMO role holders, how to transfer one or more Operation Master roles to another domain controller, and how to forcibly seize an FSMO role if the current role holder domain controller fails.
Understanding FSMO Roles in Active Directory Domain
Let’s take a quick look at the purpose of the FSMO (Flexible Single Master Operation) roles within an Active Directory domain.
Most standard operations in Active Directory, such as creating new users and security groups or joining computers to the domain, can be performed on any domain controller. The AD Replication Service is responsible for distributing these changes throughout the Active Directory. Various conflicts, such as the simultaneous renaming of a user on several domain controllers, are resolved according to the simple principle that the last action takes precedence. However, there are several operations for which a conflict would be unacceptable, such as creating a new child domain/forest or changing the AD schema. Operations that require mandatory uniqueness require domain controllers with FSMO roles. The main task of the FSMO roles is to prevent such conflicts.
A total of five FSMO roles can exist in an Active Directory domain. In this context, a domain controller with any of these roles is referred to as an Operations Master.
Two roles are unique for an AD forest:
- The Schema master is responsible for making changes to the Active Directory schema. For example, when extending the AD schema using the
adprep /forestprepcommand or adding new object attributes (managing the role requires Schema admins permissions) - The Domain naming master – ensures that all created domains and application partitions in the AD forest have unique names. It is used to add or remove domains in the forest, establish trust relationships with other domains, or rename domains in AD (to manage this role, Enterprise admins privileges are required).
There are three roles for each domain (to manage them, your account must be a member of the “Domain Admins” group):
- The PDC emulator – is the Domain Master Browser used to show computers in the network environment, it handles user lockouts when entering wrong passwords (in accordance with the AD password policy settings), is a priority DC when changing (resetting) the user password, is the main NTP time source in the domain, it is used for compatibility with legacy clients running Windows 2000/NT, it is used by DFS root servers to update the namespace information; is the default connection point for the Domain Group Policy Editor (GPMC);
- The Infrastructure Master is responsible for updating the cross-domain object links (for example, when a user from one domain is added to a group in another domain)
- The RID Master is a server that distributes Relative Identifiers/ RIDs (in blocks of 500) to other domain controllers to create unique object identifiers (SIDs) for new objects.
How to Check FSMO Role Owners in Active Directory
How can you find out which domain controllers are FSMO role holders in your Active Directory forest?
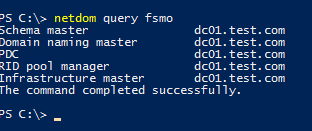
To list all FSMO role owners in the AD, run the command:
netdom query fsmo
Schema master dc01.test.com Domain naming master dc01.test.com PDC dc01.test.com RID pool manager dc01.test.com Infrastructure master dc01.test.com
You can view the FSMO roles for another domain.
netdom query fsmo /domain:woshub.com
In this example, all the FSMO roles are located on the DC01. When a new Active Directory forest is deployed, all the FSMO roles are assigned to the first domain controller. Any domain controller, except Read-Only Domain Controllers (RODCs), can be the owner of any FSMO role. A domain administrator can transfer any FSMO role to another domain controller.
You can also use the Get-ADDomainController PowerShell cmdlet to display information about FSMO roles (the RSAT Active Directory for PowerShell module must be installed):
Get-ADDomainController -Filter * | Select-Object Name, Domain, Forest, OperationMasterRoles |Where-Object {$_.OperationMasterRoles}
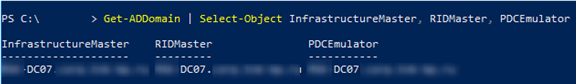
Or list the forest- or domain-level FSMO roles separately:
Get-ADDomain | Select-Object InfrastructureMaster, RIDMaster, PDCEmulator
Get-ADForest | Select-Object DomainNamingMaster, SchemaMaster
Here are the general Microsoft recommendations for FSMO role placement in the domain:
- Place the forest-level roles (Schema master and Domain naming master) on the root domain
- Place all three FSMO domain roles on a single domain controller that has sufficient performance.
- All forest DCs must be Global Catalog servers since it improves AD reliability and performance. In this case, the Infrastructure Master role is not necessary. If you have a DC without the Global Catalog role, assign the Infrastructure Master role to it.
- Unless necessary, it is not recommended to constantly move the FSMO role between domain controllers (for example, there is no need to transfer the role during a planned DC reboot after installing updates). If any of the FSMO owners are offline for a short period, this will not be noticed.
There are two possible scenarios for moving FSMO roles between domain controllers.:
- Role transfer– a voluntary transfer of the FSMO role, in which both the previous and new operation master owners are online. It is used in AD infrastructure optimization scenarios, such as when decommissioning a domain controller, or during scheduled maintenance when the current FSMO role owner is expected to be offline for a long time, such as for the whole working day or several days.
- Role seize – the forced transfer of the FSMO role if the previous owner fails and cannot be restored within a reasonable timeframe.
There are several tools available in Active Directory for transferring (or seizing) FSMO roles:
- PowerShell
- ntdsutil.exe console tool
- Graphical MMC AD management snap-ins (they are rarely used and only for voluntary movement of FSMO roles between domain controllers; don’t support forced seizure of FSMO roles.
How to Transfer FSMO Roles with PowerShell
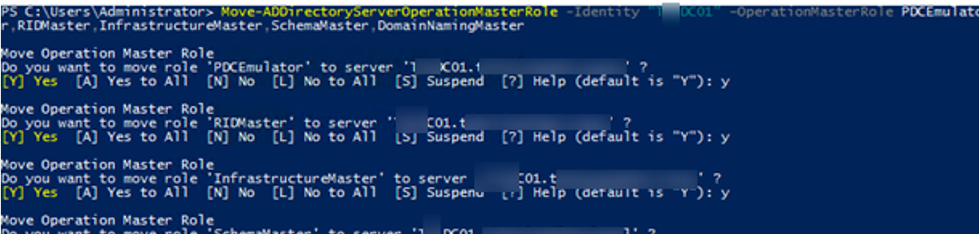
The easiest way to transfer FSMO roles in a domain is to use the Move-ADDirectoryServerOperationMasterRole PowerShell cmdlet.
You can transfer one or more FSMO roles at a time. The following command will move two roles to the specified DC02:
Move-ADDirectoryServerOperationMasterRole -Identity dc03 -OperationMasterRole PDCEmulator, RIDMaster
In the OperationMasterRole argument, you can specify either the name of the FSMO role or its index according to the following table.
| Operation master role | Role index | Permissions required |
| PDCEmulator | 0 | Domain Admins |
| RIDMaster | 1 | |
| InfrastructureMaster | 2 | |
| SchemaMaster | 3 | Schema Admins |
| DomainNamingMaster | 4 | Enterprise Admins |
To transfer all FSMO roles at once to the additional domain controller, run this command:
Move-ADDirectoryServerOperationMasterRole -Identity dc03 -OperationMasterRole 0,1,2,3,4
If you receive an Access denied error when running the Move-ADDirectoryServerOperationMasterRole command, make sure that your account has been added to the relevant administrative group.
Using Ntdsutil.exe to Transfer Operation Masters Roles from CMD
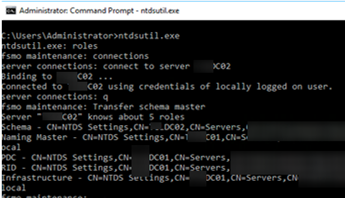
- Open a command prompt on a domain controller and run:
ntdsutil - Switch into FSMO roles maintenance mode:
roles - List DCs:
connections - Connect to the DC to which you want to transfer the FSMO roles:
connect to server <servername> - Type
qand press Enter; - To transfer an FSMO role, use this command:
transfer <role>, where <role> is the role name. For example:transfer schema master,transfer RID, etc;
- Confirm the FSMO role transfer
- When it is done, press
qand then Enter to quit ntdsutil.exe - Restart the domain controller.
Seizing FSMO Roles from an AD Domain Controller
If a DC with one of the FSMO roles has been broken and cannot be restored, it is possible to forcefully seize any of the FSMO roles. However, it is critical to ensure that the server from which the FSMO role was seized will never (!!!) appear in the network; otherwise, you risk encountering issues with the Active Directory, even if the domain controller is later restored from an AD backup.
To forcefully seize the FSMO role using the Move-ADDirectoryServerOperationMasterRole cmdlet, you need to add the -Force parameter.
For example, to seize the PDCEmulator role and force its transfer it to DC02, run the command:
Move-ADDirectoryServerOperationMasterRole -Identity DC2 -OperationMasterRole PDCEmulator –Force
You can also seize FSMO roles from one DC and assign them to another using the ntdsutil.exe tool. A role seizure is similar to a common transfer. Use the following commands:
ntdsutil
roles
connections
connect to server DC02 (the DC name to which you want to transfer the role)
quit(exit the server connections prompt)
To seize different FSMO roles, use these commands:
seize schema master quit the fsmo maintenance prompt
seize naming master
seize rid master
seize pdc
seize infrastructure master
quit
q (exit ntdsutil)
Transferring FSMO Roles in AD using GUI
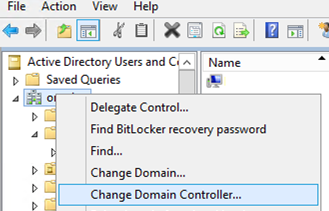
Standard Active Directory graphical snap-ins can be used to transfer FSMO roles between DCs. Ideally, the transfer operation should be performed from a DC that currently owns the FSMO role. If the server console is unavailable, use the Change Domain Controller option and select Connect to in the MMC snap-in.
| FSMO role | MMC snap-in |
| RID master | Active Directory Users and Computers snap-in (dsa.msc ) |
| PDC Emulator | |
| Infrastructure master | |
| Domain naming master | Active Directory Domains and Trusts (domain.msc) |
| Schema master | Active Directory Schema |
How to Transfer RID Master, PDC Emulator, and Infrastructure Master Roles
The Active Directory Users and Computers (dsa.msc) MMC snap-in is used to transfer domain-level roles (RID, PDC Emulator, and Infrastructure Master)
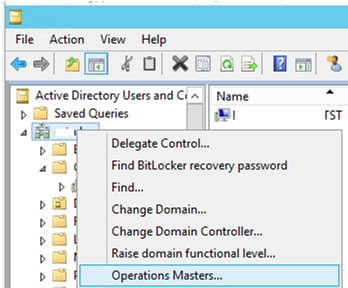
- Open the Active Directory Users and Computers (ADUC) snap-in;
- Right-click your domain name and select Operations Master;
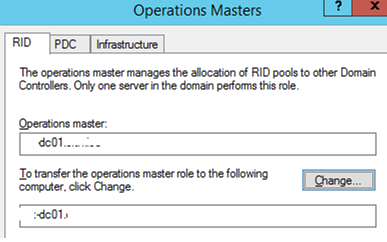
- A form containing three tabs (RID, PDC, Infrastructure) will appear. You can change the FSMO owner for each role by specifying a new DC and clicking the Change button on the corresponding tab.
How to Transfer Schema Master Role
The Active Directory Schema snap-in is used to transfer the forest-level Schema Master FSMO.
- First, register the schmmgmt.dll library using the command
regsvr32 schmmgmt.dll - Type
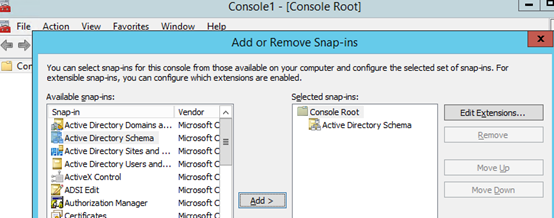
MMCin the command prompt - From the menu, select File -> Add/Remove snap-in from the menu and add the Active Directory Schema console
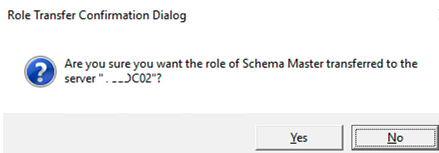
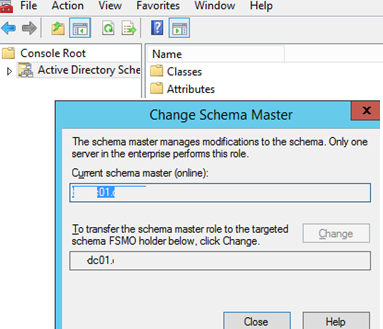
- Right-click the console root (Active Directory Schema) and select Operations Master;
- Enter the domain controller name to which you want to transfer the Schema Master role to, then click Change and OK. If the button is not available, make sure that your account is a member of the Schema Admins group.
How to Transfer Domain Naming Master FSMO
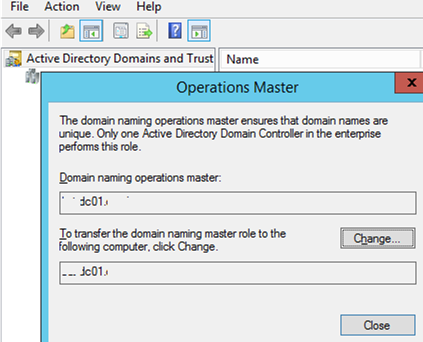
- To transfer the Domain Naming Master FSMO role, open the Active Directory Domains and Trusts snap-in
- Right-click the name of your domain and select Operations Master
- Click Change, enter the name of the domain controller, and click OK.