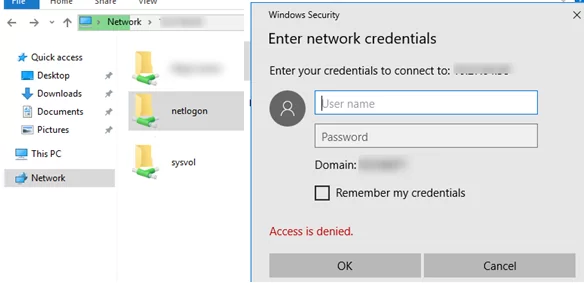
I noticed some strange things when trying to access SYSVOL and NETLOGON folders in the domain from Windows 10/Windows Server 2016. When I tried to access the domain by the UNC path \\<domain.com>\SYSVOL or by the domain controller IP address \\192.168.100.10\Netlogon, there appeared an ‘Access is denied’ error and the Windows Security prompt to enter a user credentials to access folder. After entering a valid domain user or even domain administrator credentials, the folders still did not open.
Meanwhile, the same Sysvol/Netlogon folder opens normally (without a password) if you specify the domain controller host or FQDN name: \\be-dc1.domain.com\sysvol or simply \\be-dc1\sysvol.
Also, the issues with Group Policy applying may occur on problem computers. You can find errors with the EventID 1058 in the Event Viewer logs:
The processing of Group Policy failed. Windows attempted to read the file \\domain.com\sysvol\domain.cpo\Policies\{GPO GUID}\gpt.ini from a domain controller and was not successful. Group Policy settings may not be applied until this event is resolved.This is related to new Windows security setting that protects domain computers from running code (logon scripts, executables) and getting policy configuration files from untrusted sources — UNC hardening. Windows 10/Windows Server 2016 security settings require the following security levels are used to access UNC directories with enhanced security (SYSVOL and NETLOGON shared folder):
- Mutual Authentication of a server and a client. Kerberos is used for authentication. (NTLM is not supported.) This is why you cannot access SYSVOL and NETLOGON shares on the domain controller by its IP address. By default,
RequireMutualAuthentication=1. - Integrity is the SMB signature check. It allows to make sure that data in an SMB session have not been modified during transmission. SMB signature is supported in SMB 2.0 or higher (SMB v 1 does not support SMB session signing). The default value is
RequireIntegrity=1. - Privacy is related to data encryption in an SMB session. It is supported starting from SMB v 3.0 (Windows 8/Windows Server 2012 or newer). The default value is
RequirePrivacy=0.If you have any computers or domain controllers with legacy Windows versions (Windows 7/Windows Server 2008 R2 or earlier) in your network, do not use the RequirePrivacy=1 option. Otherwise, the legacy clients won’t be able to access network shared folders on domain controllers.
Originally, these changes were made in Windows 10 in 2015 as a part of security updates MS15-011 and MS15-014. It resulted in changes in Multiple UNC Provider (MUP) algorithm that is now using special rules to access critical folders on the domain controllers: \\*\SYSVOL and \\*\NETLOGON.
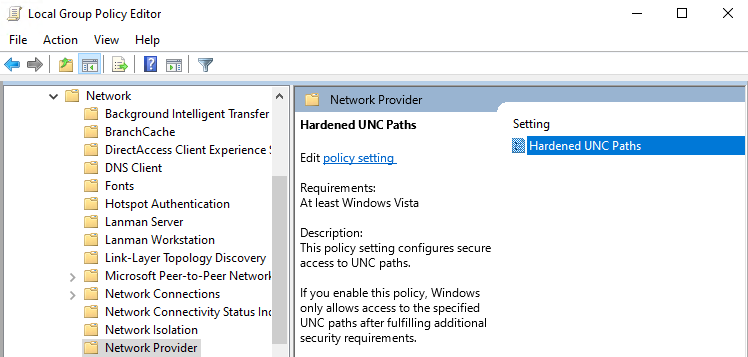
To access SYSVOL and NETLOGON, you can change UNC hardening settings in Windows 10 using Group Policy. You can use special security settings to access different UNC paths in the Hardened UNC Paths policy.
- Open the Local Group Policy Editor (gpedit.msc);
- Go to the policy section Computer Configuration -> Administrative Templates -> Network -> Network Provider;
- Enable the Hardened UNC Paths policy ;
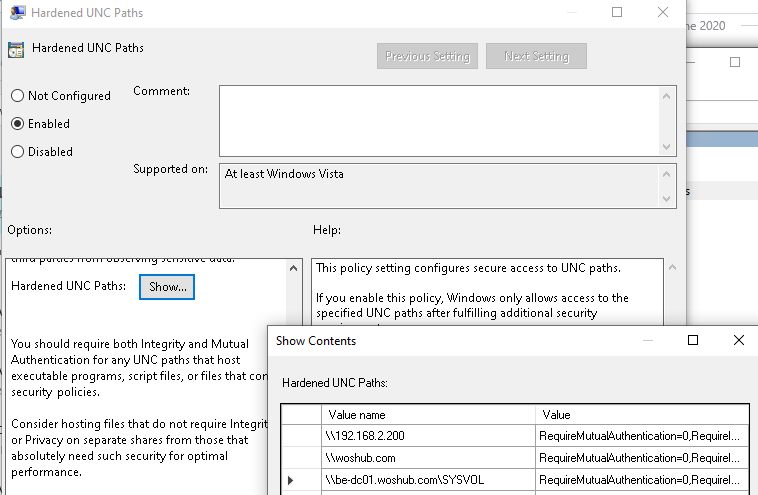
- Click the Show button and create entries for the UNC paths to Netlogon and Sysvol. To completely disable UNC hardening for specific folders (not recommended!), specify the following values:
RequireMutualAuthentication=0,RequireIntegrity=0,RequirePrivacy=0
\\192.168.200.2(the domain controller IP address)\\domain.com\\DCName
Or you can allow the access to Sysvol and Netlogon independently of the UNC path (on any DC):
\\*\SYSVOL\\*\NETLOGON
Specify all the domain (domain controller) names or IP addresses you need.
Microsoft recommends using these settings to safely access critical UNC directories:
- \\*\NETLOGON
RequireMutualAuthentication=1, RequireIntegrity=1 - \\*\SYSVOL
RequireMutualAuthentication=1, RequireIntegrity=1
Now you just have to update the policies on your computer using gpupdate /force command and make sure that you can access Sysvol and Netlogon.
You can configure these parameters using the centralized domain GPO or the following commands on the clients: (These commands will disable Kerberos authentication when you access SYSVOL and NETLOGON folders on the domain controllers. NTLM will be used instead, and you will be able to open the protected folders on the DC by their IP address.)
reg add HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\NetworkProvider\HardenedPaths /v "\\*\SYSVOL" /d "RequireMutualAuthentication=0" /t REG_SZ /f
reg add HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\NetworkProvider\HardenedPaths /v "\\*\NETLOGON" /d "RequireMutualAuthentication=0" /t REG_SZ /f
- You have an old version of administrative templates on a domain controller (a DC running Windows Server 2008 R2/ Windows Server 2012) having no Hardened UNC Paths parameter;
- Clients cannot get the Domain Policies settings due to Sysvol inaccessibility and you cannot deploy these registry settings.
4 comments
[…] some articles going into more detail below: _https://help.univention.com/t/how-to…-clients/18743 Unable to Access SYSVOL and NETLOGON folders from Windows 10 | Windows OS Hub We have it set in our domain for the \*SYSVOL and \*NETLOGON shares (you can use wildcards) as […]
[…] This sounds similar to issue we had on the new central network we have just implemented, and it was harden paths we noticed every now and again policy's where not applying as sysvol wasn't accessible. Unable to Access SYSVOL and NETLOGON folders from Windows 10 | Windows OS Hub […]
The same problem appeared on our Windows 10 Pro 21H2 (19044.2546) domain computers.
Domain policies were not applied and the gupdate/force command on the client returned the “Windows attempted to read the file \\domain.com\sysvol\domain.cpo\Policies\{GPO GUID}\gpt.ini from a domain controller and was not successful” message.
We had this issue but only on the SYSVOL share from random computers and randomly, failing once every 3 to 5 logins. Turned out to be caused by having UE-V enabled on the machines. Disabling that solved it for us but we didn’t need UE-V any more thankfully.