The file system audit policy in Windows allows to monitor all access events to specific files and folders on a disk. An administrator can enable the audit policy to identify file and folder creation, read, modification, and deletion events on the NTFS file system. File system auditing is most commonly used to control access and changes to shared network folders on Windows file servers that multiple users can access simultaneously.
Enable File System Object Access Audit Policy on Windows
File system object access auditing is not enabled by default in Windows. Access auditing can be enabled via Group Policy. To configure the audit policy on a standalone server, use the local Group Policy Editor console (gpedit.msc). If you need to enable the audit policy on multiple computers in an AD domain, use the domain GPO management console (gpmc.msc).
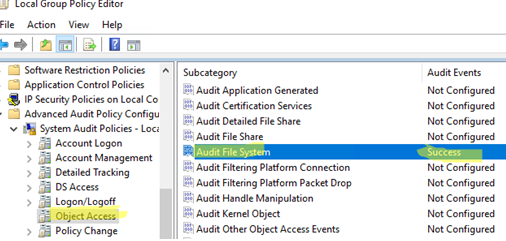
- Open the GPO editor and go to Windows Settings -> Security Settings -> Advanced Audit Policy Configuration -> System Audit Policies -> Object Access
- Open the Audit File System and specify that only successful access to filesystem objects should be logged (Configure the following audit events -> Success)
- Save the changes and update local Group Policy settings with the command:
gpupdate /force
Or enable the local file system audit policy from the command prompt.
List available audit categories:
AuditPol.exe /list /subcategory:*
Enable auditing of successful file system object access events:
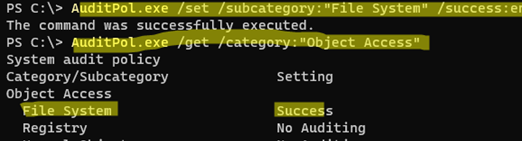
AuditPol.exe /set /subcategory:"File System" /success:enable
Check current audit settings:
AuditPol.exe /get /category:"Object Access"
How to Apply an Audit Policy to a Folder or File in Windows
Even if a policy is enabled to audit access to files and folders, no actual events are sent to the Event Viewer. Audit settings for the files and folders to be monitored must be manually enabled and configured by the administrator.
For example, your task is to track read/change/create events for all files in C:\Docs folder.
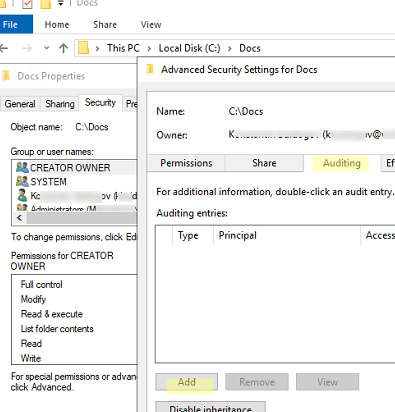
- Open the folder properties and go to the Security -> Advanced -> Auditing tab
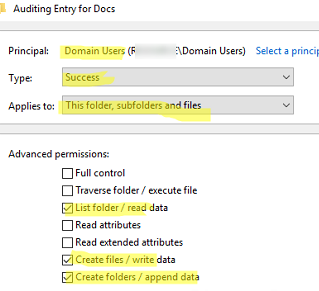
- Click Add and in the Principal field, select the users and/or groups whose object access events you want to monitor. Select Users to audit file access for all users or select Everyone if you want to include file access events by system process
- In Type, specify to track only successful access events (
Success) - Under Applies to, you can specify whether the auditing policy should be applied to the folder, files, or subfolders (default value is This folder, subfolders and files)
- In the Advanced Permissions list, select only the actions on files and folders that you want to send to the audit log. For example, to monitor only read and file modification events, select the options:
List folder/read data,Create files / write data,Create folders / append data)See an example of how to use Windows auditing policies to find the user who deleted a file from a shared folder. - Save the audit settings.
To enable auditing for a specific directory, PowerShell can be used:
$Path = "C:\Docs"
$AuditChangesRules = New-Object System.Security.AccessControl.FileSystemAuditRule('BUILTIN\Users', 'Delete,DeleteSubdirectoriesAndFiles', 'none', 'none', 'Success')
$Acl = Get-Acl -Path $Path
$Acl.AddAuditRule($AuditChangesRules)
Set-Acl -Path $Path -AclObject $Acl
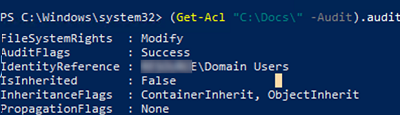
List the folder audit settings:
(Get-Acl "C:\Docs\" -Audit).Audit
If you want to recursively scan all directories and find the subfolders for which file system auditing is enabled, use this script:
$folders=Get-ChildItem "c:\docs" -Recurse |Where-Object {$_.PSIsContainer}
foreach ($folder in $folders)
{
$auditacl=(Get-Acl $folder.FullName -Audit).audit
if ($auditacl -ne "") {write-host $folder.FullName}
}
Viewing File System Access Events on Windows
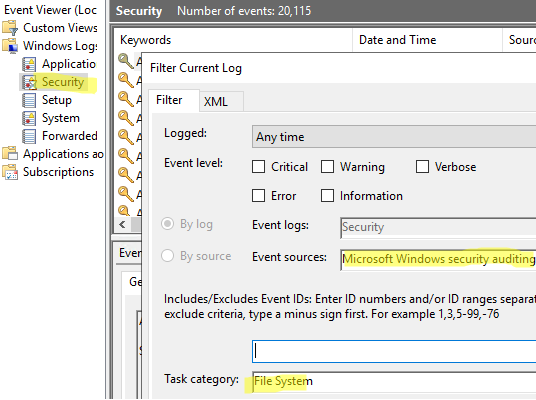
The audit policy will write a log to the Event Viewer if any actions are performed on files in the folder with auditing enabled. To view events:
- Open the Event Viewer snap-in (
eventvwr.msc) - Go to the Windows Logs -> Security section and filter the events by source:
Microsoft Windows security auditing, Task Category:File System.
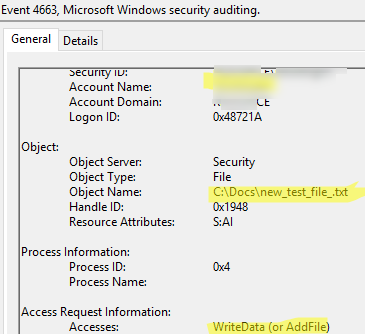
- Open any event found. For example, the event with EventID 4663 (“
An attempt was made to access an object“) contains information about the user who interacted with the file:Account Name:
File name:object_name:
type of operation (write to file in this case): Accesses:WriteData (or AddFile)
However, the Event Viewer console’s filtering and search capabilities are quite poor, and using it to search for all actions on a particular file is inconvenient.
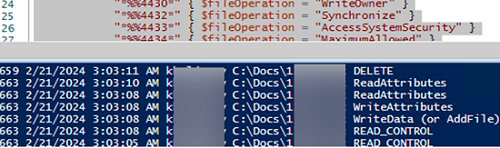
It is better to use PowerShell to find and list all access events for a particular file system object. The following PowerShell script finds and lists all access events for a specified file in Event Viewer (the Get-WinEvent cmdlet is used to query the Event Viewer):
$fileName = "C:\\docs\\new_test_file.txt"
$results = Get-WinEvent -FilterHashtable @{logname='Security'; id=4663,4659} |`
Where-Object { $_.message -match $fileName -and $_.message -notmatch "Account Name:\s*machine$*"}`
foreach ($result in $results) {
$Account = $result.properties[1].Value
$objectName = $result.properties[6].Value
$accessMask = $result.properties[8].Value
if ( $accessMask -like "*00000000-*") { $accessMask=$result.properties[9].Value}
$accessMask2 = $result.properties[9].Value
$fileOperation = ""
switch -Wildcard ($accessMask) {
"*%%1538*" { $fileOperation = "READ_CONTROL" }
"*%%4416*" { $fileOperation = "ReadData (or ListDirectory)" }
"*%%4417*" { $fileOperation = "WriteData (or AddFile)" }
"*%%4418*" { $fileOperation = "AppendData (or AddSubdirectory or CreatePipeInstance)" }
"*%%4419*" { $fileOperation = "ReadEA" }
"*%%4420*" { $fileOperation = "WriteEA" }
"*%%4423*" { $fileOperation = "ReadAttributes" }
"*%%4424*" { $fileOperation = "WriteAttributes" }
"*%%4426*" { $fileOperation = "Delete" }
"*%%4428*" { $fileOperation = "ReadControl" }
"*%%4429*" { $fileOperation = "WriteDAC" }
"*%%4430*" { $fileOperation = "WriteOwner" }
"*%%4432*" { $fileOperation = "Synchronize" }
"*%%4433*" { $fileOperation = "AccessSystemSecurity" }
"*%%4434*" { $fileOperation = "MaximumAllowed" }
"*%%4436*" { $fileOperation = "GenericAll" }
"*%%4437*" { $fileOperation = "GenericExecute" }
"*%%4438*" { $fileOperation = "GenericWrite" }
"*%%4439*" { $fileOperation = "GenericRead" }
"*%%1537*" { $fileOperation = "DELETE" }
default { $fileOperation = "Unknown" }
}
Write-Host $result.Id $result.TimeCreated $Account $objectName $fileOperation
}
Write-Host $result.Id $result.TimeCreated $Account $objectName $fileOperation
}
You can send the resulting list of access audit events to your log collector, database, text log file, or send an email notification using Send-MailMessage when a monitored file is accessed/modified.
 .
.