By default, the RDP access to the desktop of Windows Server member servers or Active Directory domain controllers is restricted to users added to the local Administrators or Domain Admins groups. In this post, we’ll show you how to grant non-admin users RDP access to Windows Server hosts or domain controllers without assigning them local admin rights.
By default, Windows security settings allow a remote user to make RDP connections through Remote Desktop Services (TermService) if:
- The user is a member of the local Administrators or Remote Desktop Users group;
- The local Allow the log on through Remote Desktop Services policy allows the user to connect.
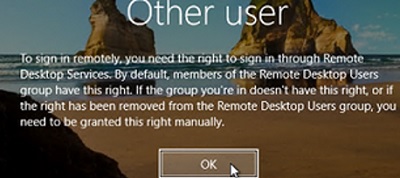
To Sign in Remotely, You Need the Right to Sign in Through Remote Desktop Services
The user receives an error when attempting to remotely connect to the Windows Server desktop:
To sign in remotely, you need the right to sign in Remote Desktop Services. By default only members of the Administrators group have this right. If the group you’re in doesn’t have this right, or if the right has been removed from Administrators group, you need to be granted this right manually.
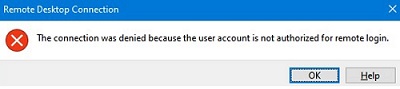
If Network Level Authentication (NLA) is enabled in the RDP setting on the remote host, another error occurs when connecting:
The connection was denied because the user account is not authorized for remote login.
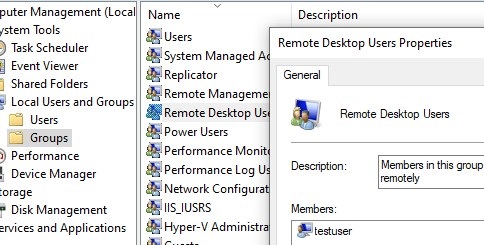
In this case, you simply need to add the user to the local Remote Desktop Users group to allow them to connect to Windows Server via RDP:
- Open the Local Users and Groups MMC snap-in (
lusrmgr.msc) and navigate to the Groups section; - Double-click the Remote Desktop Users group;
- Click the Add button and enter the name of the user (or group) you want to grant RDP access to;
- Users can then connect to the Windows host via RDP.
It is also possible to add a user to an RDP access group from the command line:
net localgroup "Remote Desktop Users" /add woshub\testuser
or using PowerShell:
Add-LocalGroupMember -Group "Remote Desktop Users" -Member testuser
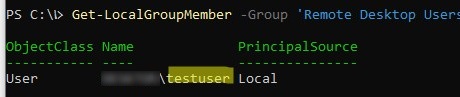
List users in the Remote Desktop Users group:
Get-LocalGroupMember -Group 'Remote Desktop Users'
By default, Windows Server allows two concurrent Remote Desktop sessions. This means that two users can work simultaneously in their own Remote Desktop sessions. If you need more concurrent RDP connections, you will need to purchase and activate licenses (RDP CALs) on the RDS License Server and install the Remote Desktop Services role (this can be a standalone RDSH server or a full RDS farm consisting of several hosts).
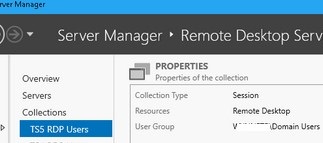
You can use RDS Collections to provide remote desktop access in an RDS farm. Open Server Manager -> Remote Desktop Services –> Tasks -> Edit Deployment Properties.
Open the collection and the User Group section will list the security group allowed to connect to the RDSH hosts in that collection.
Allow RDP Access to Domain Controller for Non-Admin User
If you need to grant a regular (non-admin) user remote access to the desktop of a domain controller, the method described above won’t work.
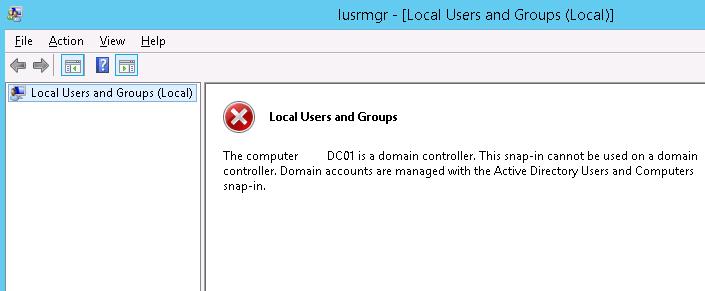
After the server role is promoted to an Active Directory domain controller, you cannot manage local users and groups from the Computer Management MMC snap-in. When you try to open the Local Users and Groups console (lusrmgr.msc), the following error appears:
The computer xxx is a domain controller. This snip-in cannot be used on a domain controller. Domain accounts are managed with the Active Directory Users and Computers snap-in.
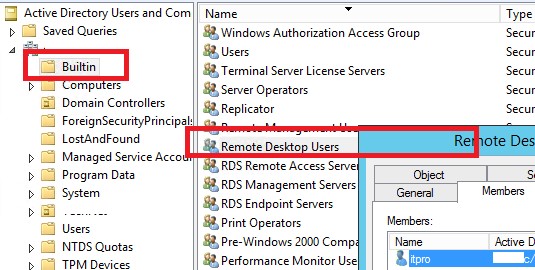
As you can see, there are no local groups on the domain controller. Instead of the local group Remote Desktop Users, the DC uses the built-in domain group Remote Desktop Users (located in the Builtin container). You can manage this group from the ADUC console or the DC command prompt.
However, it is not recommended to use this group to grant Remote Desktop access as this will give the user access to all DCs in the domain. In this case, it is better to grant permissions using the Allow log on through Remote Desktop Services policy.
However, in large corporate networks with a large number of employees, it is often necessary to provide RDP access to the DC (Usually to branch DCs or RODCs) for different groups of server administrators, on-duty administrators, or other technical staff. There are also situations where third-party services managed by non-domain administrators are deployed on the DC, and there’s a need to maintain these services.
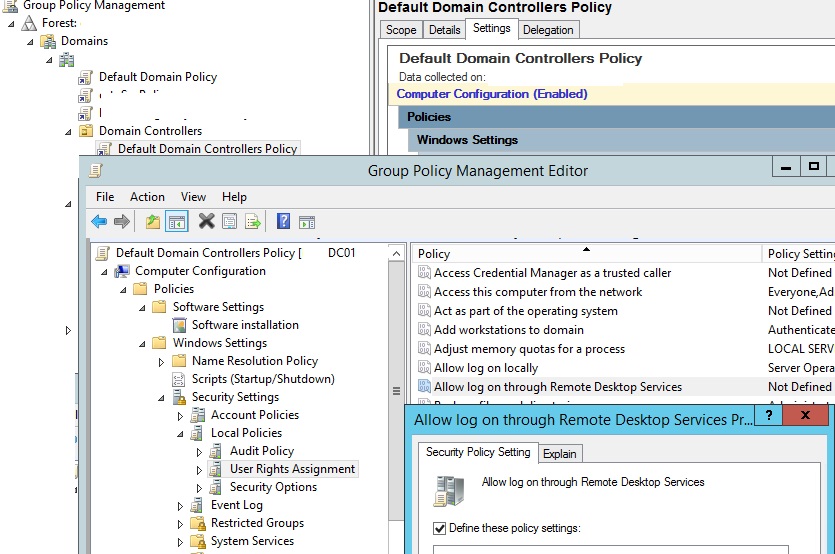
How to Allow Log on Through Remote Desktop Services?
To allow a domain user or group to remotely connect to Windows via RDP, you must grant them the SeRemoteInteractiveLogonRight privilege. You can grant this permission using the Allow log on through Remote Desktop Services policy.
To allow remote connection to the domain controllers for members of the Remote Desktop Users group you need to change the settings of this policy on your domain controller:
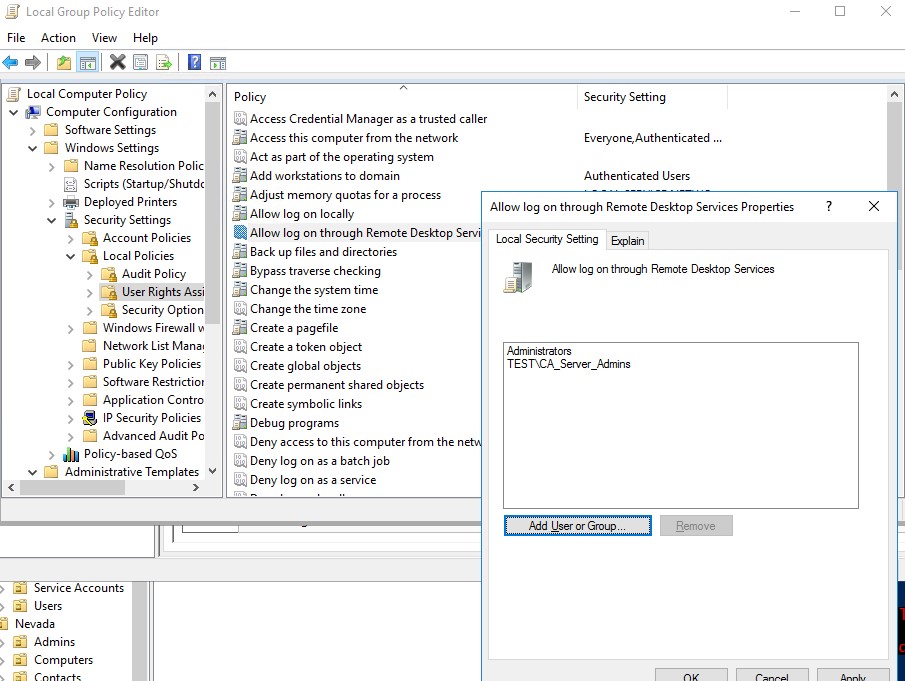
- Open the Local Group Policy Editor (
gpedit.msc); - Go to the GPO section Computer Configuration -> Windows settings -> Security Settings -> Local policies -> User Rights Assignment;
- Find the policy Allow log on through Remote Desktop Services;Once the server has been promoted to a DC, the only group that remains in this local policy is the Administrators group (these are Domain Admins).
- Edit the policy and add the domain user or group directly (
domain\CA_Server_Admins) to it; - Update the Local Group Policy settings on the DC using the command: :
gpupdate /force
Note that the group that you added to the Allow log on through Remote Desktop Services policy should not be present in the “Deny log on through Remote Desktop Services” policy because it has a higher priority (check the article Block remote access under local user accounts). Also, if you restrict the list of computers that users can log on to, you must add the server name to the user account properties in AD (LogonWorkstations user attribute).
- Backup Operators
- Administrators
- Print Operators
- Server Operators
- Account Operators
If you do not do this, you will get an error message when you try to connect to Remote Desktop: The sign-in method you’re trying to use isn’t allowed.
To make things easier, you can create a new security group in the domain, for example AllowDCLogin. Next, add the accounts that need to be allowed to remotely access the DC to the policy. If you need to allow access to all AD domain controllers at once, rather than editing the local policy on each DC, it’s better to add the user group to the Default Domain Controllers Policy using the Group Policy Management Console (GPMC.msc). Edit the policy item Allow log on through Remote Desktop Services under the section Computer Configuration\Windows Settings\Security Settings\Local Policies\User Rights Assignment.
The users you added to the policy will now be able to connect to the AD domain controller’s desktop via RDP.
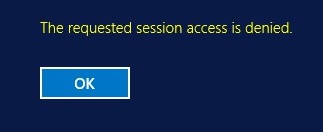
The Requested RDP Session Access is Denied
In some cases, you may receive the following error when you use RDP to connect to a Windows Server domain member host or domain controller:
The requested session access is denied.
The following problems may occur if you connect to the DC using a non-administrator account:
- You are trying to connect to the server console (using the
mstsc /adminmode). This connection mode is only allowed for administrators. Attempt to connect to the server with the mstsc.exe client in normal RDP mode (without/adminoption); - It is possible that there are already two active RDP sessions on the host (By default, no more than two concurrent RDP sessions can connect to a Windows Server without an RDS role deployed). You can get the list of active sessions and logged-on users on the remote computer by using the command:
qwinsta /server:dc01
You cannot end other users’ sessions without administrator permissions. You must wait for administrators to release or end a session; - Restricted Admin mode or Windows Defender Remote Credential Guard is enabled on the Windows Server host
31 comments
Hi there.
Went through your post.
I am having windows 2012 AD with more than 350 active users. What I want to achieve is – I want to create a user group in AD for some users and have it administered by someone else apart from the server administrator (basically creating/deleting users in that group and resetting their password.) I want this group administrator to access the server through remote desktop but, in AD users & computers only his group should be visible to him and not the entire AD.
How to achieve this.
Kindly advice.
Thanks.
Hi
Quite a strange requirements
Create separate OU in AD, move user to it and delegates the necessary permissions to admin
Give him permissions locally on the server, not through AD
hi guys,
i have problem on windows 10 home edition, i want using RDP Session but not working, still error “the requested session access is denied”. after login.
help me please!
Windows 10 Home doesn’t have Remote Desktop Connection.
I would recommend upgrading to the Pro Edition.
Otherwise, There are a few Illegal avenues to attempt.
out of all the articles i researched on how to enable non-admins to RDP into domain controllers (or any other server for that matter) …. this is the ONLY article that actually works. Thank you very much for posting this
Thanks for posting this. It’s spot on.
Thanks a lot …
i just want to access a domain server, but i don’t have any admin rights the administrator have blocked almost every thing even i cannot install a program or even uninstall a program. please help
I have a data but its coded in shell script i just want to read it please suggest.
Thank you, this worked a charm.
Thank you!! BCH address?
Welcome! You can donate us via PayPal on https://woshub.com/about/
This is also valuable for reversing the process – i.e. when you inherit a setup where lots of users can RDP to the DCs – this shows you how to stop this happening!
Normally with Remote Desktop into Windows Server 2016, if someone tries to log on and both licenses are being used, the user can disconnect of the connected users so he can log on. Is there a way to prevent the new user from knocking off a currently connected user?
much thanks bill
Only an administrator can kick off another user RDP session, you can’t disable this feature.
CAUTION !!!!!, Dont do this setting through the default domain controller policy, you will be screwed. Once you enable the allow logon through remote desktop services, the default permission like domain admin everything wiped out and the only added groups might have rdp access to the domain controllers. It’s one way change no going back.
THANK YOU!! This post was the answer to my prayers after hours of searching. Thank you, and thank you again.
This is such BAD ADVICE.
There is no reason for ANYONE who is not a domain admin to RDP onto a DC in an enterprise where there are any other admins who are not Domain Admins.
There should be NO third party tools installed on a DC except by the Domain Admin after careful analysis to determine whether they need to be there.
Answer, always, is “no”, except for system monitoring tools.
Some products need to have schema modifications in the domain – e.g. Exchange, Sharepoint, etc. These do not need to be run ON the DC. They need to be run by someone with Schema Admins (and perhaps Enterprise Admins) rights on a domain-joined server in the same site as a DC running the Global Catalog role (preferably the Schema Master).
For other administrators who have been delegated account or computer management rights in the domain, they should use Active Directory Users and Computers (if they need that console) installed preferably on a jump server they can RDP to (or on a workstation, if you must), as well as any other RBAC tools they need for their tasks.
I’m not even going to get into putting management servers on their own networks and configuring firewall rules, but at least don’t let non Domain Admin techs log onto your DCs!
Also, using a GPO to add someone to any of the BUILTIN domain groups is ridiculous. You just add them directly. The point of BUILTIN is that it applies to all DCs (and only DCs, btw).
Actually your advice is horrible. Admins should ALWAYS have 2 accounts: One admin account and one normal account. ONLY use admin account(s) when absolutely necessary as this lowers security session hijacking potential and it lessens the change that an inadvertent configuration change is made when doing routine (and mundane) tasks that do not actually require administrative permissions.
A good example is if, for some reason, you need to use a browser or even plug in a storage device. If the site you visit or device you are using has been compromised, any attack requiring admin privileges will be prevented, and if the non-admin profile was compromised, you can just delete it and re-create it.
There are literally hundreds on non-admin-level things that admins do and having a separate account to do them is imperative for security. You should never do these things on any server with an admin account (this includes workstations & all stand alone servers) if you do not need admin access.
tnx -tnx -tnx
Tried it on my 2019 Standard server. The users are still removed from remote desktop users after policy update. The only way I can users to login is make them administrators.
Probably I shouldn’t be using MS Server. It’s a small business, 10 users, I don’t need or care about DC, AD or any other soul MS infrastructure, I just want a simple Windows file-app-remote desktop server.
I also don’t want the overhead of virtualization for this small shop and the idea of 2 servers is ridiculous.
Is there another trick or an update for 2019?
I have not tried to do this on Windows Server 2019. In my opinion everything should work as in previous versions of Windows Server.
Have you edited the local policy “Allow log on through Remote Desktop Services” of your server via gpedit.msc?
I have the same problem, and yes I have have checked the local policy “Allow log on through Remote Desktop Services” and “Deny log on through Remote Desktop Services” still no succes.
Can’t deny in that way. In my environment, we need permissions to login and check if there are any disk space, performance checks on the DC, so it is required RDP login on a DC. In that case, really this article will help us. But I also have a requirement is that person (non-admin) need to patch the DC but he shouldn’t have access on AD console (dsa.msc). I am looking for a solution.
Hi We have 2 AD servers and a remote location has an RODC server. On-site RODC server after link down (MPSL) the admin RODC user is not able to log in on the server.
How do you allow non-admin users to see active RDP sessions in a RDS Session Collection? It’s like a turn-around problem…we have support staff who need to see active RDP sessions in our RDS farm.
Try this command to allow your helpdesk team to query and connect to RDS user sessions
# domain\my_helpdesk_team – your group
# 1 = WINSTATION_USER_ACCESS => Permissions: Logon, QueryInformation, SendMessage and Connect
wmic /namespace:\\root\CIMV2\TerminalServices PATH Win32_TSPermissionsSetting WHERE (TerminalName ="RDP-Tcp") CALL AddAccount "domain\my_helpdesk_team",1Unfortunately, these methods don’t work on a stock Windows 2019 or Windows 2022 server. There are some instances where you might want a particular domain user to be able to log in remotely, but don’t want that user to be an administrator. Surely there is a way to do this without making all remote desktop users admins! Can you update this blog for the later versions? I figure it’s some policy change hidden somewhere, but can’t for the life of me, find it!
do you solve the problem?
Hi.
Is there any way to configure the server in RDS to allow non-admin users to log off logged on users via the task manager?
For example, a helpdesk group would be allowed to log off locked user sessions on the RDS server.
Use this command to delegate permissions for corp\helpdesk to log off/disconnect other RDS users:
wmic /namespace:\\root\CIMV2\TerminalServices PATH Win32_TSPermissionsSetting WHERE (TerminalName='RDP-Tcp') CALL AddAccount 'corp\helpdesk',2