In the previous post, we covered how to deploy a centralized log collection and management service based on the Graylog stack (Graylog + OpenSearch + MongoDB). Now let’s cover how to send Event Viewer logs from Windows hosts (including Active Directory domain controller events) to Graylog collector.
Configuring Graylog Data Collector for Windows Devices
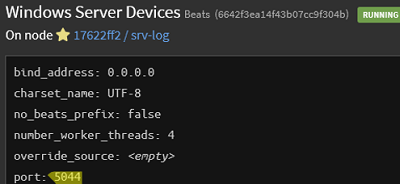
Go to System -> Inputs and add a new Windows Server Devices collector with type Beats that listens on port TCP:5044
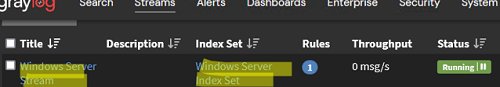
Then create a separate index for Windows Event logs. Based on the new Input and index, create a new Windows stream (under the Streams section) and run it.
Winlogbeat: Sending Windows Event Logs to Graylog
To send EventViewer logs on Windows hosts to the Graylog server, use the Winlogbeat log collector service. Winlogbeat is the open-source part of the ELK stack. The Winlogbeat service must be installed on each Windows host whose events you want to see on the Graylog.
- Download the Winlogbeat archive from the download page (https://www.elastic.co/downloads/beats/winlogbeat)
- Extract the archive to a folder
C:\Program Files\winlogbeat - Edit the winlogbeat.yml configuration file.
In the simplest case, use the following configuration, where all events from the Application, Security, and System Event logs will be sent to the specified Graylog server
winlogbeat.event_logs:
- name: Application
ignore_older: 72h
- name: Security
- name: System
output.logstash:
hosts: ["192.168.14.146:5044"]
Use more flexible filtering to get only the event logs you need. For example, use the following configuration to collect events with specific severity levels and EventID numbers:
---
winlogbeat.event_logs:
- name: Security
event_id: 4627, 4703, 4780-4782
ignore_older: 24h
level: critical, error
- name: Microsoft-Windows-TerminalServicesRDPClient/Operational
event_id: 1102
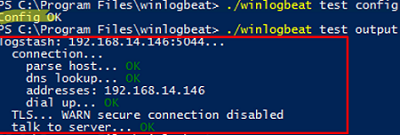
Save the winlogbeat.yml file. Check that the Winlogbeat configuration is correct and that the log collector service is available:
cd "C:\Program Files\winlogbeat"
./winlogbeat test config
./winlogbeat test output
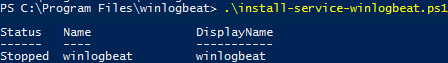
Install and start the winlogbeat service if everything is OK:
.\install-service-winlogbeat.ps1
Start-Service winlogbeat
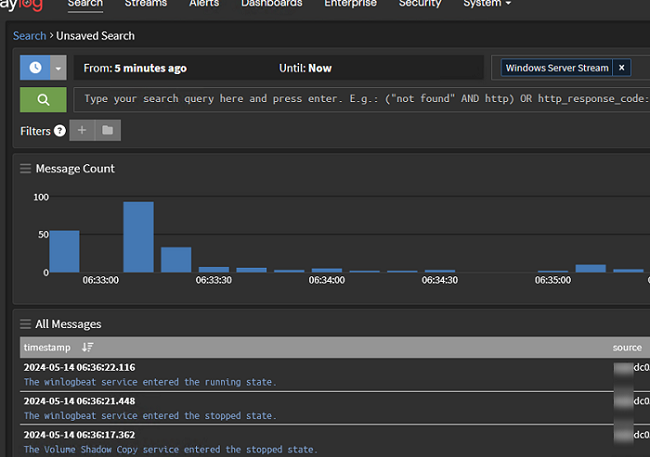
Go to the Graylog Server web interface and check that events from your Windows servers have started to appear in the corresponding stream.
Collect Active Directory Domain Controller Event Logs with Graylog
Let’s take a look at how to use the Graylog server to search and analyze Windows events. We’ll use the events of the Active Directory domain controller as an example.
Suppose there are several additional domain controllers in Active Directory. In that case, it can be difficult for administrators to find a specific event because they have to check the logs on each DC. However, a central log collector server on Graylog that stores events from all DCs can find any event in seconds.
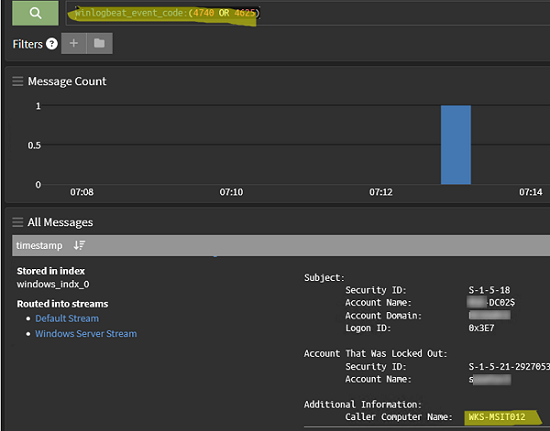
For example, you may need to identify the computer where the user account was locked because of an incorrect password. To do this, open the Graylog filter prompt, select the desired Stream, or specify it in the query code (streams:xxxxxxxxxxxxx) and run the following query:
winlogbeat_event_code:(4740 OR 4625) AND winlogbeat_event_provider:Microsoft\-Windows\-Security\-Auditing
The Graylog server will quickly find the event that you are looking for. Under its properties you will see the the computer from which the account was locked.
Here are some more examples of searching for different events in Active Directory:
- Event ID
4767– find out who unlocked the AD user - Event ID
4724– who/when reset the domain user’s password - Event ID
4720– who and when created a new user in AD;4722– account enabled,4725– disabled,4726– user deleted. - Tracking changes to Active Directory group membership:
4727(new group created),4728(user added to group),4729(user removed from group),4730(security group removed) - Event ID
5137(new domain Group Policy/GPO created),5136(GPO changed),5141(GPO removed) - Event ID
4624— successful domain user logon event (allows to quickly view the login history of AD user)
Ensure that the Winlogbeat agents are configured to send logs on each Domain Controller (list the active DCs using the Get-ADDomainController cmdlet). The collection of some Active Directory security events must be enabled in the Audit Policy settings in the Default Domain Controller policy.
You can create saved queries and dashboards in Graylog to quickly find the events that interest you. Gralog notifications can be used to alert administrators about critical events in AD.
Centralizing Event Logging for Windows Hosts
Graylog provides convenient collection, storage, retrieval, and analysis of events from other Windows Server services. The following are examples of different scenarios where an administrator might need to search through the Windows event logs.
- Audit file and folder access events on a file server
- Track the deletion of files/folders in a shared folder
- Audit changes made to file and folder permissions in Windows
- Tracking Remote Desktop (RDP) connection logs
- Detect RDP brute force attacks on Windows
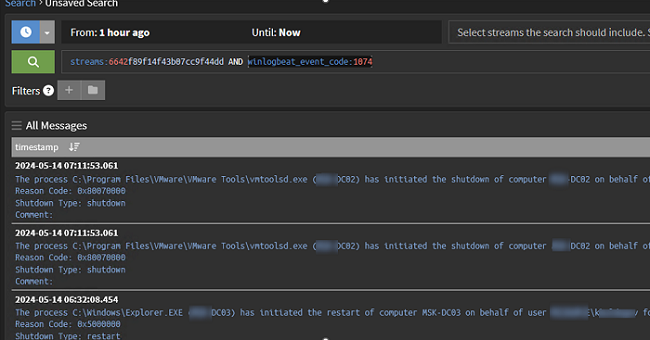
- How to find out who shutdown or restarted a computer:
winlogbeat_event_code:1074 - Response to the clearing of the event logs (may indicate a possible compromise of the Windows Server)
- Get alerted when the built-in Windows Defender antivirus detects a virus on one of your Windows Server hosts (Event ID
1006,1116).
The fast and simple Graylog collector makes it easy to search and filter events in Windows logs. See this post on the Graylog site to get started monitoring critical event IDs on Windows hosts.
Centralized storage of Windows and Active Directory event logs makes it easy to quickly investigate and respond to information security incidents, analyze infrastructure events, and troubleshoot problems.