Active Directory is a reliable yet critical service, and the functionality of the entire enterprise network depends on its proper operation. The proper functioning of Active Directory requires constant monitoring by the system administrator. This article describes how to use the dcdiag, repadmin, PowerShell, and other built-in tools to check and diagnose the health of your Active Directory domain, domain controllers, and replication status.
How to Check AD Domain Controller Health Using Dcdiag
Dcdiag (Domain Controller Diagnostic Tool) is a basic built-in tool for checking the health of Active Directory domain controllers. To quickly check the state of a specific AD domain controller, use the command:
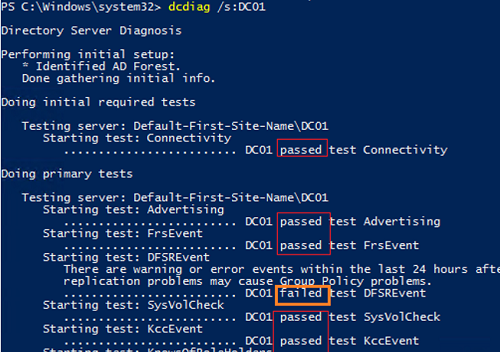
dcdiag /s:DC01
The command performs various tests against the specified domain controller and returns the status for each test (Passed | Failed).
Typical tests:
- Connectivity – checks if the DC is registered in DNS, tests LDAP and RPC connectivity
- Advertising – checks the roles and services published on the DC
- FRSEvent – checks for errors in the file replication service and SYSVOL replication errors
- FSMOCheck – verifies that the DC can connect to the KDC, PDC, and Global Catalog server
- MachineAccount — verifies that the DC account is correctly registered in AD and that the domain trust relationship is correct
- NetLogons – checks the logon privileges to allow replication to proceed
- Replications – checks the status of the replication between the domain controllers and whether there are any errors
- KnowsOfRoleHolders – checks the availability of the domain controllers with FSMO roles
- Services – checks that the required services are running on the domain controllers
- Systemlog – checks for errors in the DC logs
- Etc.
In addition to the standard checks performed by default, there are additional checks you can run against the domain controller:
- Topology – checks if KCC has generated a full topology for all DCs
- CheckSecurityError
- CutoffServers – finds a DC that is not replicated because its partner is unavailable
- DNS – six DNS checks are available (
/DnsBasic,/DnsForwarders,/DnsDelegation,/DnsDymanicUpdate,/DnsRecordRegistration,/DnsResolveExtName)- OutboundSecureChannels
- VerifyReplicas – checks if the application partitions are replicated correctly
- VerifyEnterpriseReferences
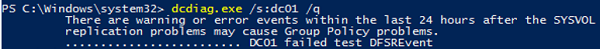
For example, if you want to verify that DNS is working correctly on all of your domain controllers, use the command:
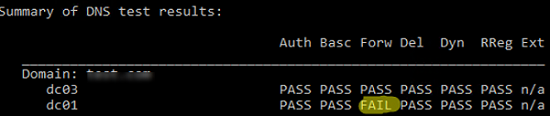
dcdiag.exe /s:DC01 /test:dns /e /v
It will result in a summary table showing test results on how DNS resolves names on all DCs (if it is OK, you will see Pass in each cell). If you see Fail, you need to run this test against the problem DC:
dcdiag.exe /s:DC01 /test:dns /DnsForwarders /v
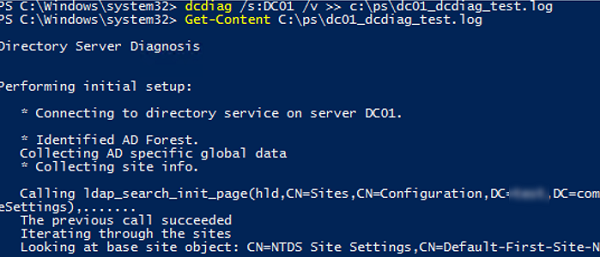
Get detailed information about the domain controller test results and save the output to a text file:
dcdiag /s:DC01 /v >> c:\ps\dc01_dcdiag_test.log
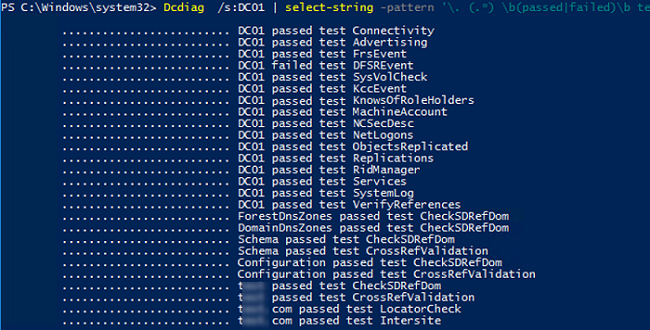
Dcdiag /s:DC01 | select-string -pattern '\. (.*) \b(passed|failed)\b test (.*)'
Query the status of all domain controllers:
dcdiag.exe /s:woshub.com /a
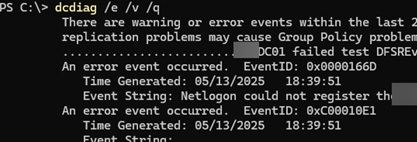
To prevent unnecessary information about successful checks from cluttering the dcdiag output, you can add the /q parameter to query the status of domain controllers and AD, displaying only errors that require administrator attention:
dcdiag /q /e /v
Or get errors for a specific DC:
dcdiag.exe /s:dc01 /q
The dcdiag command has a /fix option that allows automatic fixing of trivial errors in AD on a specific DC:
dcdiag.exe /s:dc01 /fix
On all domain controllers:
dcdiag /e /fix
Checking Active Directory Replication Health
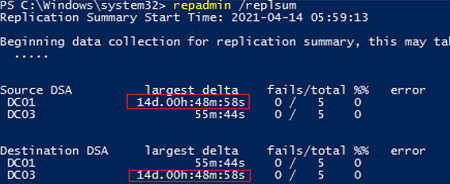
The built-in repadmin utility is used to check the replication status between Active Directory domain controllers. The basic command for checking the status of both inbound and outbound replication on a DC is:
repadmin /replsum
The tool returns the current status of replicating between all DCs. Ideally, the largest delta value should be less than 1 hour (depends on the AD topology and inter-site replication frequency settings), and the number of replication fails should be 0. In my example, you can see that one of the last replications took 14 days, but now it is OK.
To check replication for all DCs in the domain:
repadmin /replsum *
Verify inter-site replication:
repadmin /showism
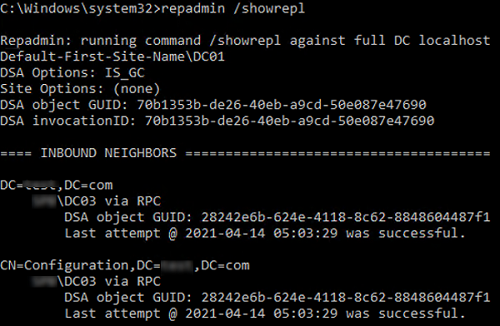
To view the replication topology and errors (if any), run this command:
repadmin /showrepl
The command checks the DC and returns the time and date of the last successful replication for each directory partition (last attempt xxxx was successful).
repadmin /showrepl *
To initiate password replication from a writable domain controller (RWDC) to a read-only domain controller (RODC), use the /rodcpwdrepl option.
The /replicate option forces replication of the specified directory partition to a specific DC.
Use the following command to force a specified domain controller DC to synchronize with all of its replication partners (performs pull replication, which means that the domain controller pulls changes from its replication partners):
repadmin /syncall
Add the /AdeP switch to push changes from the domain controller outward to all other domain controllers:
repadmin /syncall /AdeP
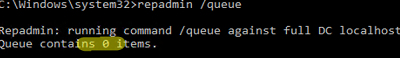
To view the replication queue:
repadmin /queue
Ideally, the replication queue should be empty.
Check when the last backup of the current domain controller was created:
Repadmin /showbackup *
There are also several PowerShell cmdlets that you can use to check the status of replication in AD.
Get a list of DCs in a domain:
Get-ADDomainController
List replication errors on the specified DCs:
Get-ADReplicationFailure -Target DC1,DC2
View AD replication errors in a site ( -Scope Site ) or domain ( -Scope Domain ):
Get-ADReplicationFailure -scope site -target Berlin| FT Server, LastError, Partner-Auto
Get-ADReplicationFailure -Target woshub.com -Scope Domain
Get the current DC’s replication partner list:
Get-ADReplicationConnection -Filter *
To force replication, use the Sync-ADObject cmdlet.
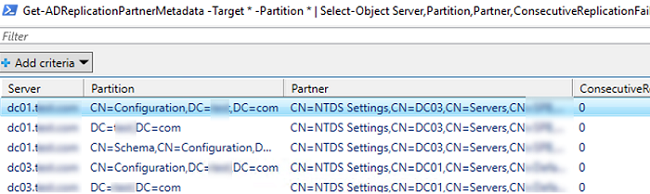
For example, the following command will display all replication errors detected in the Out-GridView table:
Get-ADReplicationPartnerMetadata -Target * -Partition * | Select-Object Server,Partition,Partner,ConsecutiveReplicationFailures,LastReplicationSuccess,LastRepicationResult | Out-GridView
https://github.com/maxbakhub/winposh/blob/main/ADHealthCheck.ps1
- This script is for the English version of Windows Server.
- To periodically check the status of domain controllers, you can add a PowerShell script to the Task Scheduler.
Check Basic Domain Controller Services Health
Let’s look at how to check the status of other basic domain controller services.
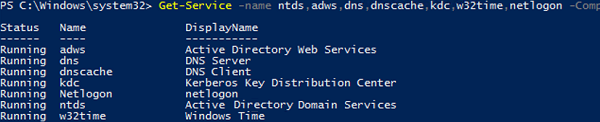
To get the status of the ADDS services, use the Get-Service cmdlet:
Get-Service -name ntds,adws,dns,dnscache,kdc,w32time,netlogon
You can also check the state of ADDS basic services on a domain controller using the Get-Service cmdlet:
- Active Directory Domain Services (
ntds) - Active Directory Web Services (
adws) – all cmdlets from the AD PowerShell module connect to this service - DNS (
dnscacheanddns) - Kerberos Key Distribution Center (
kdc) - Windows Time Service (
w32time) - NetLogon (
netlogon)
Also, check that the SYSVOL and NETLOGON shared folders are published on the DC:
net share
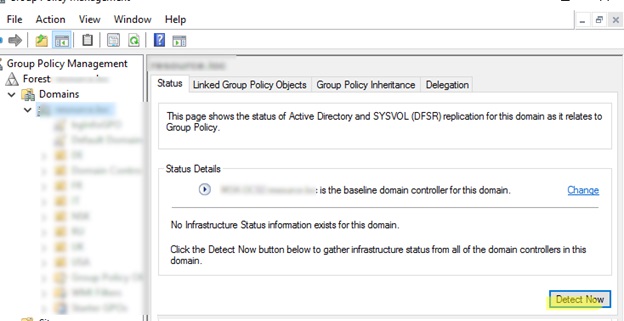
To check the health of the GPO infrastructure on domain controllers, use the Group Policy Management graphical console ( gpmc.msc ). Run GPMC, select the domain root, and click the Detect Now button on the Status tab.
This compares the GPO information in AD with the SYSVOL information on each domain controller.
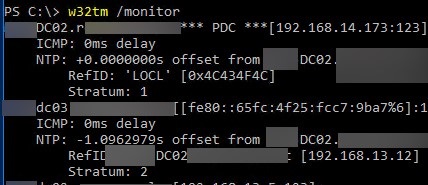
Next, be sure to check the time synchronization on the domain controllers using the command:
w32tm /monitor
The time difference between the PDC (the primary time source in the domain) and other DCs should be around 0 (NTP offset). If not, check the NTP time synchronization in Active Directory.
So, in this article, we have covered basic tools, commands, and PowerShell scripts that you can use to diagnose the health of your Active Directory domain. You can use them in all supported versions of Windows Server, including domain controllers running in Server Core mode.
3 comments
Thanks for sharing. Really appreciated. Francesco
Thanks for sharing. My reprot have some issue:
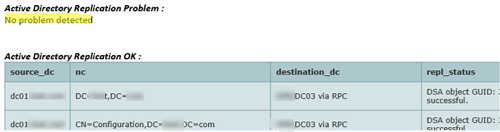
The full Active Directory Replication report is available here
Active Directory Replication Problem :
No problem detected
Active Directory Replication OK :
–>here is null<–
To quickly get the replication status for all DCs on the specified site:
Get-ADReplicationFailure -scope site -target Madrid | FT Server, LastError, Partner-Auto
Or for all domain controllers in the domain or in the forest (-Scope Forest):
Get-ADReplicationFailure -Target “woshub.com” -Scope Domain
Get-ADReplicationConnection cmdlet is used to display information about the replication partners for the current domain controller.
Get-ADReplicationConnection -Filter *
To force synchronization of the specific object between domain controllers, Sync-ADObject cmdlet is used
Get-ADDomainController -filter * | foreach {Sync-ADObject -Object “cn=John Silvia,cn=Users,dc=woshub,dc=com” -source DC1 -Destination $_.hostname}
Get the replication status of a certain object:
Get-ADReplicationAttributeMetadata -Object “CN=Maggie Skosana,OU=Users,DC=woshub,DC=com” -Server DC1
Get-ADReplicationUpToDatenessVectorTable cmdlet allows to get the list of USN values for replication partners:
Get-ADReplicationUpToDatenessVectorTable * | ft Partner,Server,UsnFilter