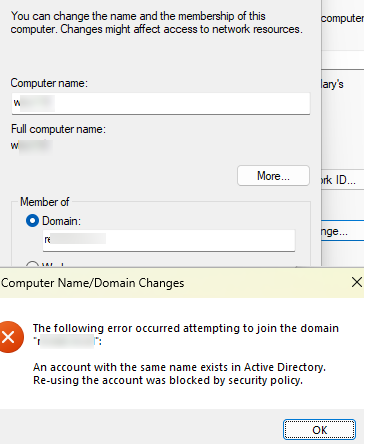
When attempting to join a computer to an Active Directory domain, an error may occur:
Error 0xaac (2732): NERR_AccountReuseBlockedByPolicy: An account with the same name exists in Active Directory. Re-using the account was blocked by security policy.
This behavior is caused by Windows updates released in October 2022 that improved the security of reusing existing computer accounts in Active Directory. These updates prevent a device from joining an AD domain by using an existing (pre-created) computer account (to help protect against critical vulnerability CVE-2022-38042). Exceptions are cases when:
- The user account that created the computer object in AD is used to perform the domain join.
- Computer was created by a member of the Domain Admins group
- The user is a member of the Domain Administrators, Enterprise Administrators, or built-in Administrators.
- User account added to the GPO option Domain controller: Allow computer account re-use during domain join (this policy option was introduced in March 2023)
When a computer is joined to a domain, a series of checks are performed to prevent access to the existing computer object in the domain if the user does not meet the above conditions.
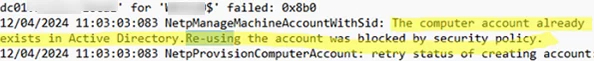
Check the domain join log on the client (C:\Windows\debug\NetSetup.LOG). It should contain the following lines:
NetpGetComputerObjectDn: Crack results: (Account already exists) DN = CN=wks0001,CN=Computers,DC=woshub,DC=loc NetpGetADObjectOwnerAttributes: Looking up attributes for machine account: CN=wks0001,CN=Computers,DC=woshub,DC=loc NetpGetADObjectOwnerAttributes: Ms-Ds-CreatorSid is empty. NetpManageMachineAccountWithSid: NetUserAdd on 'h-dc01.woshub.loc' for 'WKS0001$' failed: 0x8b0 NetpManageMachineAccountWithSid: The computer account already exists in Active Directory. Re-using the account was blocked by security policy.
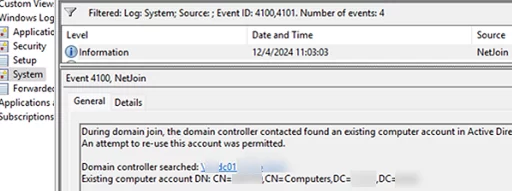
An event with event ID 4100 or 4101 should also appear in the System log in Event Viewer:
During domain join, the domain controller contacted found an existing computer account in Active Directory with the same name. An attempt to re-use this account was permitted. Domain controller searched: \\h-dc01.woshub.loc Existing computer account DN: CN=wks0001,CN=Computers,DC=woshub,DC=loc
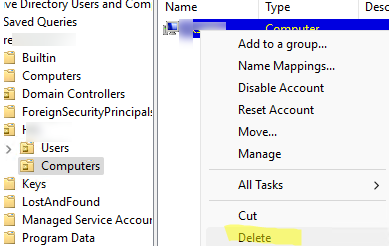
The simplest workaround is to rename the computer (hostname) or delete the previously created account with that name from AD. In this case, you can easily join the computer to the AD domain with a new name.
If you want to allow some non-admin users to join computers to existing accounts, you must configure a separate GPO for domain controllers.
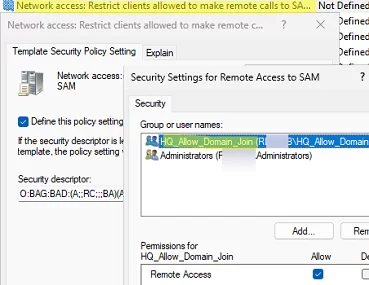
- Create a security group in the AD domain and add users who can reuse computer accounts. For example, HQ_Allow_Domain_Join
- Open the domain Policy Management Console (
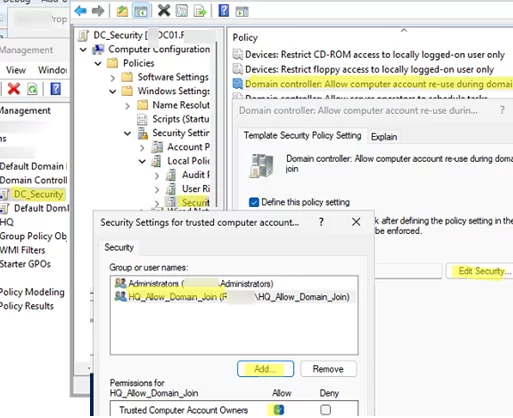
gpmc.msc), create a new GPO, and link it to the Domain Controllers OU. - Open the GPO and go to Computer Configuration -> Policies -> Windows Settings -> Security Settings -> Local Policies -> Security Options
- Open the policy Domain controller: Allow computer account re-use during domain join.
- Enable the policy. Then click Edit Security and add the previously created group of trusted users who will be allowed to join computers to the domain To enhance security, keep the number of members in this group to a minimum.
- Wait for the GPO settings to be updated on the DC, or update them immediately with the command
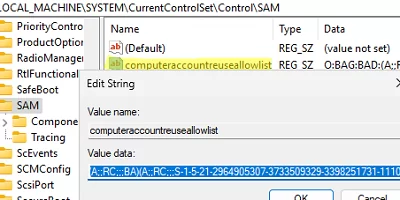
gpupdate /force - The policy changes the value of the computeraccountreuseallowlist parameter in the
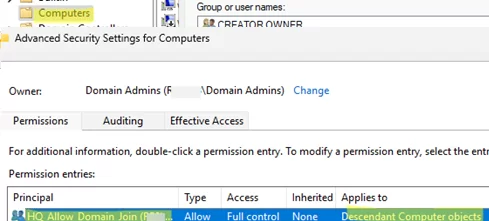
HKLM\SYSTEM\CurrentControlSet\Control\SAMregistry key on the DC. Its value will contain a list of the groups you have added (in SDDL format). - Verify that the members of this group have been delegated AD permissions to manage computer accounts in the target OU.
Now, users in this group can use existing computer accounts when joining devices to the domain.
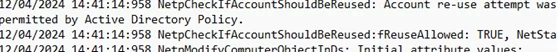
Check the NetSetup.LOG log:
NetpCheckIfAccountShouldBeReused: Account re-use attempt was permitted by Active Directory Policy. NetpCheckIfAccountShouldBeReused:fReuseAllowed: TRUE, NetStatus:0x0
If the user still cannot add the computer to the domain after applying the specified settings, check the C:\Windows\debug\NetSetup.LOG file for the following line:
Active Directory Policy check with SAM_DOMAIN_JOIN_POLICY_LEVEL_V2 returned NetStatus:0x5.
This indicates that the user does not have permission to remotely connect to the domain controller and check records in the SAM database. In this case, you must enable Network access: Restrict clients allowed to make remote calls to SAM security policy for DC and add your user group to it.
reg add HKLM\System\CurrentControlSet\Control\Lsa /v NetJoinLegacyAccountReuse /t REG_DWORD /d 1 /f
However, support for this registry setting was removed in the August 2024 updates, and this option no longer works.