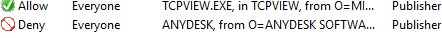Using AppLocker security policies, administrators can block or allow specific applications to run on Windows. With Applocker, it is possible to restrict program execution for a specific user group while allowing others, such as administrators, to run them. This guide explains how to create and deploy AppLocker application access policies using GPO.
The AppLocker application control feature was originally available only on Enterprise editions of Windows. However, starting with Windows 10 version 2004 and all Windows 11 versions, these edition restrictions were removed, allowing AppLocker policies to be applied to Pro editions as well.
Let’s create a new domain GPO containing the AppLocker control settings using the domain Group Policy management snap-in gpmc.msc (in the same way you can configure Applocker settings on a standalone machine using the Local Group Policy editor),
- Create a new GPO and switch to edit mode.
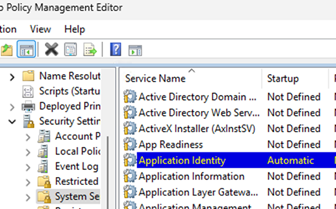
- In order for the AppLocker policies to be applied to clients, the Application Identity service must be enabled and running (the
AppIDSvcservice by default is disabled in Windows). - Navigate to Computer Configuration -> Windows Settings -> Security Settings -> System Services. Open the Application Identity service properties and enable the automatic startup.
- Then expand Computer Configuration -> Policies -> Windows Settings -> Security Settings -> Application Control Policies -> AppLocker. You can create rules for four software categories here:
Executable Rules – Executable files (.EXE and .COM).
Windows Installer Rules – Windows Installer files (.MSI, .MSP, .MST).
Script Rules – script files (.BAT, .CMD, .JS, .PS1, and .VBS).
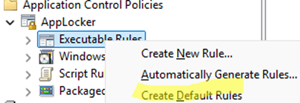
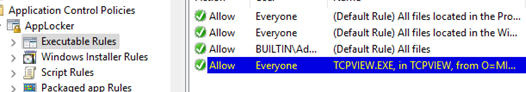
Packaged app Rules – APPX and MSIX Microsoft Store apps. - In this example, we will create software control rules for executable files. So, right-click on Executable Rules and select Create Default Rules
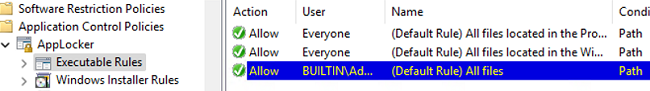
- Several predefined rules will be created.
Allow Everyone (All files located in the Program Files folder) – this rule enables users to run files from theProgram Filesdirectory.
Allow Everyone (All files located in the Windows folder) – it allows users to run any file from theWindowsdirectory.
Allow BUILTIN\Administrators (All files) – members of the local Administrators group can run any file.
- For example, you may want to allow non-admin users to run a specific application, regardless of its version or where it is located on the disk.
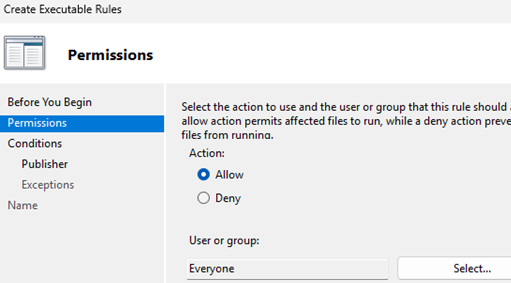
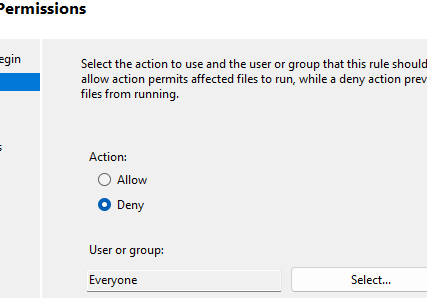
- Create a new AppLocker rule. Select whether you want to Allow or Deny the executable file to run. Select the user group to which this policy will apply (by default Everyone).
- Next, choose the conditions for the AppLocker rule. Three options are available:
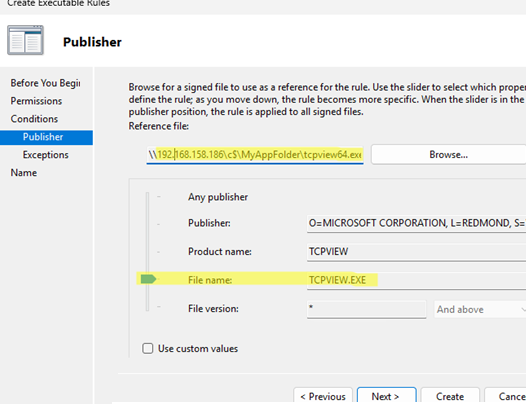
Publisher – it allows creating rules for signed files (files from a specific publisher). With this rule, you can select from the following options: publisher name, product name, executable file name, or file version.
Path – specify the path to the directory or file to which the rule will be applied. You can either specify the full path to the EXE file or use the wildcard character (*). For example, the ruleC:\MyAppFolder\*will apply to all executable files in the specified directory.
File hash – rule can be used to identify an unsigned file based on its SHA-256 hash. This rule allows or denies execution of a file, regardless of its name or location on the disk. However, if the file version is changed (e.g., after a software update), the rule must be recreated for the new file hash.The following AppLocker-specific environment variables can be used when specifying paths in rules.Windows directory or drive AppLocker path variable Windows directory %WINDIR%System32 and sysWOW64 %SYSTEM32%Windows installation drive %OSDRIVE%Program Files %PROGRAMFILES%Removable media (CD or DVD) %REMOVABLE%Removable storage device (USB flash drive) %HOT% - We will create an AppLocker rule for a specific app by its publisher. Select the target executable file. Because the target file may be missing from the domain controller where the AppLocker rule is created, you can use a UNC path to select the file from the client computer over the network (for example, use the Windows admin share path format
\\computer123\c$\tools\tcpview64.exe) - I want to allow this file to run based on its name, regardless of the version. The slider should be moved to the File Name. Or, configure more flexible conditions using the Use custom values option.
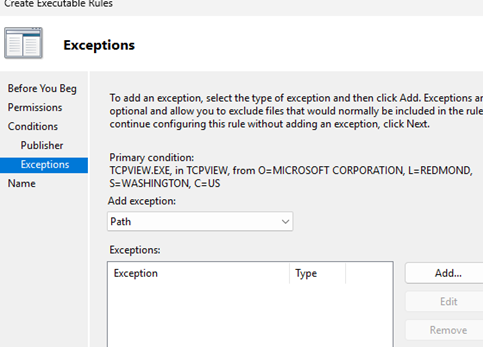
- In the Exceptions section, you can make exceptions to the rule by path, publisher, or file hash. For example, you can prevent old, vulnerable versions of apps from running or restrict them to certain folders.
- Set the new AppLocker rule name.
Now, let’s create a rule that blocks users from running the AnyDesk.exe app.
- Add a new AppLocker rule
- The rule should prevent anyone from running the app. Select Action: Deny, User or Group: Everyone.
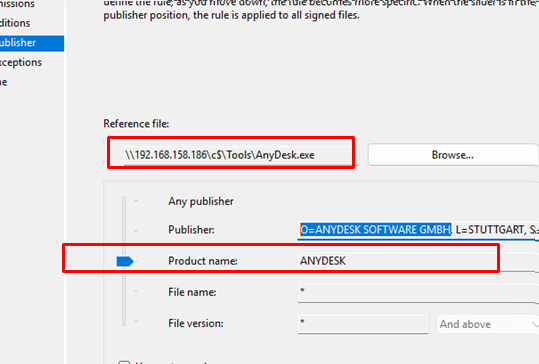
- Create a Publisher rule and browse for the AnyDesk executable.
- This rule should apply regardless of the file’s version or location. You can either completely deny the launch of files signed by the publisher
O=ANYDESK SOFTWARE GMBHor restrict it by product name. - Such a rule will block the program from launching regardless of the directory where the executable resides or the actual file name.
To apply the AppLocker rules that you create to client computers, open the AppLocker properties in the GPO console. There are four types of rules available here:
- Executable rules – rules for classical Win32 executable (Exe) files
- Windows Installer rules – MSI installer rules
- Script Rules – script execution rules
- Packaged all Rules – rules for Microsoft Store AppX/MSIX Packages
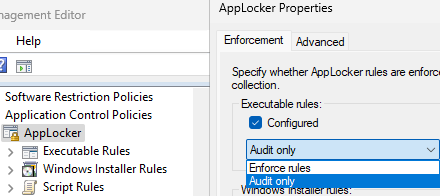
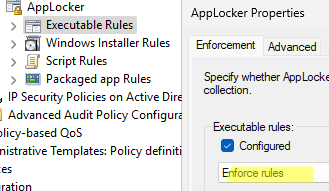
By default, AppLocker rules are not applied. To apply rules to clients, you need to enable the Configured option and select whether you want to apply the rules in Audit only or in Enforce rules mode.
It is recommended to initially apply the rules in audit mode to test their impact on clients without actually blocking app execution
Link the GPO with AppLocker settings to the target OU (it is strongly recommended to test the software restriction rules on test computers/OUs first).
After applying new Group Policy settings on a client, check how AppLocker rules work on it. Since the AppLocker rules are currently applied in audit mode, applications are not actually blocked from launching.
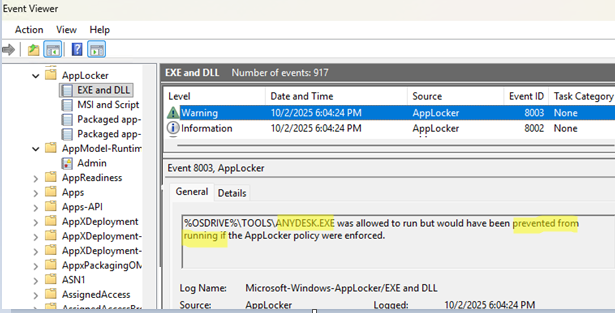
You can use Event Viewer logs to determine how AppLocker policies are triggered when specific executable files are launched. Open the Event Viewer console (eventvwr.msc) and navigate to Application and Services Logs -> Microsoft -> Windows -> AppLocker -> EXE and DLL.
When AppLocker detects an attempt to run a blocked executable file, it logs a warning with Event ID 8003 that includes the name of the blocked app.
%OSDRIVE%\TOOLS\ANYDESK.EXE was allowed to run but would have been prevented from running if the AppLocker policy were enforced.
If the application is permitted to run, Event ID 8002 will be added.
Test AppLocker rules under non-administrative user accounts, as the default rules allow administrators to run all applications without restrictions. Users must work within their sessions, launching the necessary programs and performing their standard daily tasks.
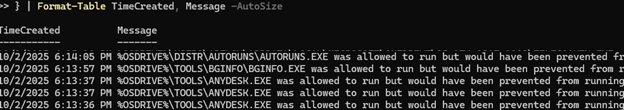
Review the apps that are blocked from running according to the audit events. You can use PowerShell to query the Event Viewer logs and get a list of apps blocked by AppLocker rules on a computer.
$TimeSpan = (Get-Date).AddHours(-24)
Get-WinEvent -FilterHashtable @{LogName = "Microsoft-Windows-AppLocker/EXE and DLL"; Id = 8003; StartTime = $TimeSpan } | Format-Table TimeCreated, Message -AutoSize
If the current application control policy blocks a required executable file, edit the AppLocker GPO to add a rule allowing that app to run.
After debugging the AppLocker rules in audit mode, you can apply them in enforced mode. To do this, change the Audit setting in the AppLocker policy to Enforce rules.
AppLocker will now block the launch of any programs that are not authorized or explicitly denied.
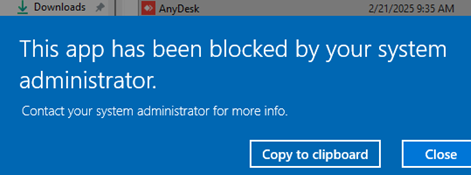
This app has been blocked by your administrator
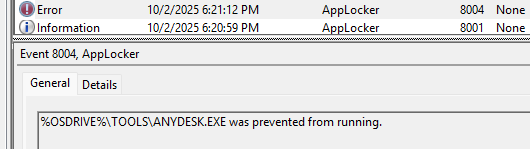
The event with ID 8004 will now be added to the Event Viewer, which contains the name of the blocked executable file.
%OSDRIVE%\TOOLS\ANYDESK.EXE was prevented from running.
Manually creating separate rules for each allowed or blocked app in AppLocker is time-consuming and tedious. There are several tools that can speed up and improve the process of creating and implementing AppLocker rules.
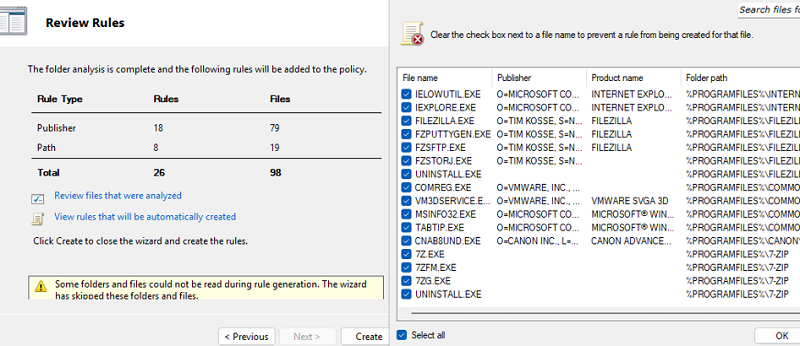
The AppLocker configuration editor in the GPO console has an automatic rule generation feature. The administrator can select the Automatically Generate Rules option and specify a target folder on the reference machine. Then, AppLocker will generate a list of rules for all the software found on the computer.
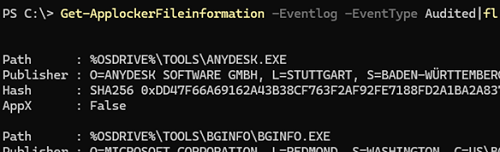
You can also create AppLocker rules by importing them from individual computers. For example, you can get a list of blocked executable files from the Event Viewer logs using PowerShell:
Get-ApplockerFileinformation -Eventlog -EventType Audited|fl
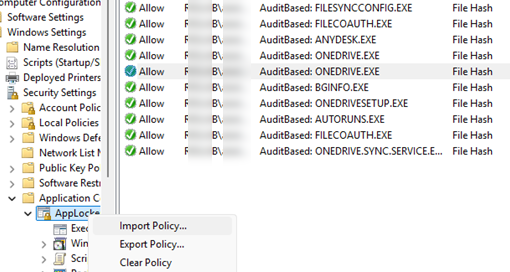
Based on this information, you can automatically add rules to the local AppLocker policy.
Get-ApplockerFileinformation -Eventlog -EventType Audited | New-ApplockerPolicy -RuleType Hash, Publisher -User jsmith -RuleNamePrefix AuditBased | Set-ApplockerPolicy –Merge
The new rules will be added to the computer’s local AppLocker policy. From there, they can be exported and imported to the domain GPO.
List only blocked executable (including the number of attempts to run each file):
Get-AppLockerFileInformation -EventLog -EventType Denied -Statistics
Keep the following points in mind when creating AppLocker rules:
- AppLocker deny rules take precedence over allow rules
- By default, everything is prohibited unless it is explicitly allowed. In other words, an executable file is allowed to run only if it is explicitly allowed by a rule and not explicitly denied by any other rule.
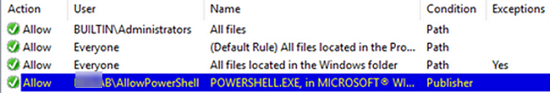
- Each rule may have exceptions. For example, this will allow certain rules to be applied to some groups of users while making exceptions for others. The screenshot shows how to use exceptions to allow PowerShell to run for administrators but block it for non-admin users (the article about disabling PowerShell on a Windows computer is an example of implementing such a rule).
- When creating rules, keep in mind that groups like “Everyone” and “Domain Users” may also include administrators.
What about the possibility of temporarily suspending AppLocker on a computer? You might think that stopping the Application Identity service would prevent AppLocker rules from being applied. However, this is not true.
To temporarily disable AppLocker on a computer, first stop the AppIDSvc service and then delete the AppCache.dat, Exe.AppLocker, and Dll.AppLocker files from the C:\Windows\System32\AppLocker\ folder.