If you suspect that the built-in Windows Defender firewall is blocking network connections (from a specific program or service), it is a bad idea to disable it completely. Instead, you can log all network traffic that passes through the Windows Defender Firewall, identify the filtered/dropped packets, find ports and source/destination IP addresses, and then create appropriate allow rules.
In this article, we’ll show how to enable network connection logging in Windows Firewall and how to analyze the logs.
Enable Logging in Windows Firewall
Windows Defender Firewall allows to log both successful and blocked network connections. Logging can be enabled separately for each network profile (Private, Public, or Domain Network). By default, traffic logging is disabled in the Windows Firewall. To turn on traffic debugging in the firewall :
- Open the snap-in Windows Firewall with Advanced Security MMC (
wf.msc). - Right-click on the root of the console and select Properties;
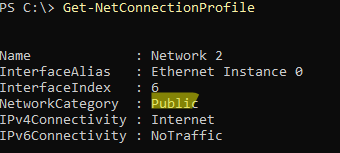
- Then go to the tab of the Windows network profile for which you want to enable logging (Domain, Private, or Public Profile).To check the network profile assigned to an active network interface in Windows, use the command:
Get-NetConnectionProfile
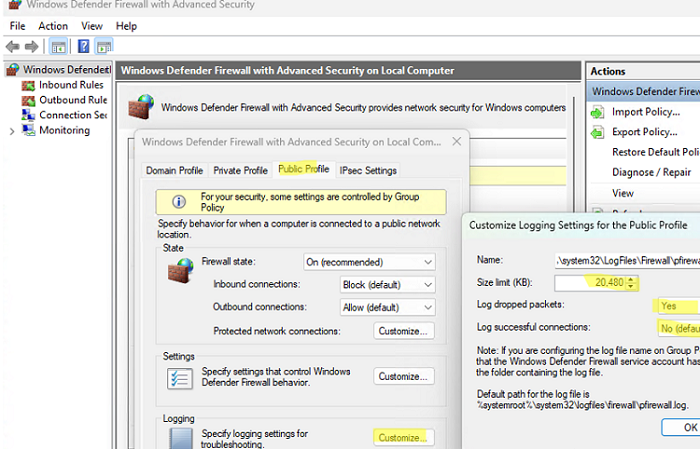
- On the Profile tab, click the Customize button in the Logging section.
- Here you can configure the following settings:
Name (log file): by default%systemroot%\system32\LogFiles\Firewall\pfirewall.log
Size limit: increase the maximum log size from 4 MB to 20 MB (20480KB)
Log dropped packets: is it necessary to log dropped packet connections?
Log successful connections: logging all successful network connections can result in a very large log file.
To effectively monitor and understand which network profile (Domain, Private, or Public) is blocking or allowing specific network connections, you can configure Windows Firewall to log the activity of each profile in a separate log file. For example:
%windir%\system32\logfiles\firewall\pfirewall_domain.log%windir%\system32\logfiles\firewall\pfirewall_private.log%windir%\system32\logfiles\firewall\pfirewall_public.log
Windows Firewall logging options can also be configured through PowerShell:
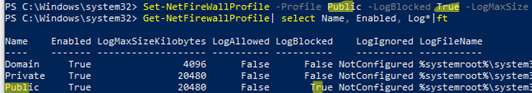
Set-NetFireWallProfile -Profile Public -LogBlocked True -LogMaxSize 20480 -LogFileName "%systemroot%\system32\LogFiles\Firewall\pfirewall.log" -Verbose
Lists the current firewall logging settings for all profiles:
Get-NetFirewallProfile| select Name, Enabled, Log*|ft
Parsing Windows Firewall Logs with PowerShell
All network connections are now logged to a plain text file by the Windows Firewall. You can open the log file manually, or use PowerShell to search for specific connections in the log file (the Windows equivalent of the grep and tail commands is the Select-String cmdlet).
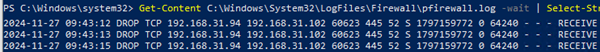
For example, the following command displays in real-time all filtered (DROP) network connections to TCP port 445 (SMB):
Get-Content C:\Windows\System32\LogFiles\Firewall\pfirewall.log -wait | Select-String -pattern "DROP.*TCP.*445"
The following log file format is used:
date time action protocol src-ip dst-ip src-port dst-port size tcpflags tcpsyn tcpack tcpwin icmptype icmpcode info path pid
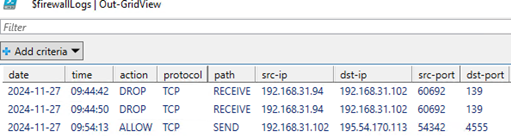
Use this PowerShell function, which displays the log in a convenient Out-GridView graphical table, to analyze the firewall log files:
function Get-WindowsFirewallLog {
param(
[parameter(Position=0,Mandatory=$false)]
[ValidateScript({Test-Path $_})]
[string]$LogFilePath = "$env:SystemRoot\System32\LogFiles\Firewall\pfirewall.log"
)
$headerFields = @("date","time", "action","protocol","src-ip","dst-ip","src-port","dst-port","size", "tcpflags","tcpsyn", "tcpack","tcpwin","icmptype","icmpcode", "info","path")
$firewallLogs = Get-Content $LogFilePath | ConvertFrom-Csv -Header $headerFields -Delimiter ' '
$firewallLogs | Out-GridView
}
Get-WindowsFirewallLog
View Windows Firewall Logs in Event Viewer
It is sometimes more convenient to write Windows Firewall connection logs to the Event Viewer rather than to text files. This can be achieved by enabling audit policies in the local GPO:
- Open the local GPO editor (
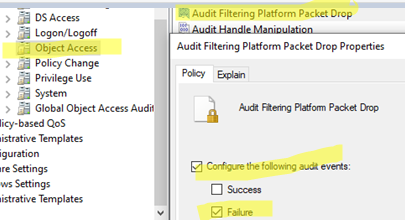
gpedit.msc) - Go to Computer Configuration -> Windows Settings -> Security Settings -> Advanced Audit Policy Configuration -> System Audit Policies — Local Group Policy Object -> Object Access
- Blocked connection events can be sent to the Event Viewer using the Audit Filtering Platform Packet Drop policy. Enable the Failure option in the policy settings.
- Audit Filtering Platform Connection parameter used to log successful connections in Windows Firewall. This audit policy is rarely used because enabling it can result in many events being written to the log (this requires increasing the maximum size of the Event Viewer log)
- Update the GPO settings on the computer:
gpupdate /force
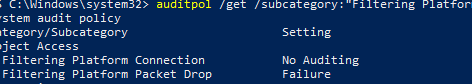
Auditpol /set /category:"System" /SubCategory:"Filtering Platform Packet Drop" /failure:enable
View the current Windows Firewall audit policy settings:
auditpol /get /subcategory:"Filtering Platform Packet Drop","Filtering Platform Connection"
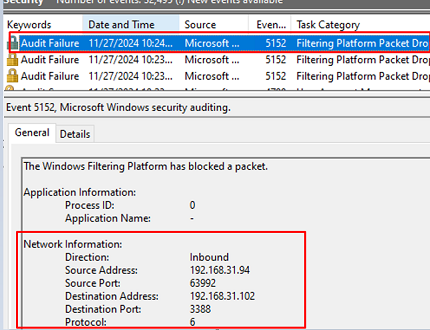
To view Windows Firewall events, open Event Viewer (eventvwr.msc). Expand Windows Logs -> Security. Enable the event filter for the Filtering Platform Packet Drop category.
All the connections that are blocked by the Windows Firewall will be available in the Event viewer. These events have EventID 5152 ( The Windows Filtering Platform has blocked a packet ). The event description includes network packet information: protocol number (TCP – 6, UDP 17, ICMP 1), IP address and source/destination port, direction (Inbound, Outbound), process name (for outgoing connections).
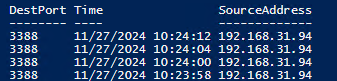
Use the Get-WinEvent PowerShell cmdlet to search and filter Windows Firewall events in Event Viewer. The following PowerShell script finds all connection attempts that are blocked by the Windows Firewall on port 3388 and returns a table with the time and source of the connection:
$destinationPort = "3388"
$filterXml = @"
<QueryList>
<Query Id="0" Path="Security">
<Select Path="Security">
*[System[(EventID=5152)]]
and
*[EventData[Data[@Name='DestPort'] and (Data='$destinationPort')]]
</Select>
</Query>
</QueryList>
"@
$FirewallLogs = @()
$events=Get-WinEvent -FilterXml $filterXml
foreach ($event in $events) {
$eventXml = [xml]$event.ToXml()
$SourceAddress = $eventXml.Event.EventData.Data | Where-Object { $_.Name -eq 'SourceAddress' } | Select-Object -ExpandProperty '#text'
$DestPort = $eventXml.Event.EventData.Data | Where-Object { $_.Name -eq 'DestPort' } | Select-Object -ExpandProperty '#text'
$FirewallLog = New-Object PSObject -Property @{
SourceAddress= $SourceAddress
Time=$event.TimeCreated
DestPort=$DestPort
}
$FirewallLogs += $FirewallLog
}
$FirewallLogs
Enabling firewall logging allows you to inspect all allowed and dropped network connections, helping identify errors in your Windows Firewall rules and create accurate ones.