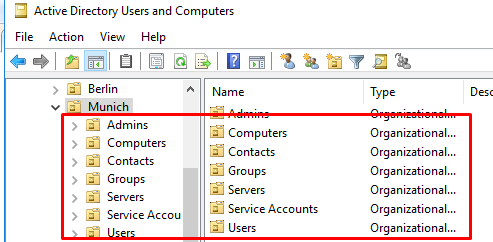
Quite often when creating new Organizational Units (OUs), an Active Directory administrator has to create a structure of nested containers inside a new OU. For example, when a company opens a new branch office, you need to create AD containers for users, groups, servers, and service accounts in the new OU. To avoid manually creating nested OUs and assigning permissions in the ADUC snap-in (dsa.msc), you can use the PowerShell script from this article to create and configure nested OUs in bulk. The script not only creates new organizational units but also creates administrative security groups and grants them permission to new OUs.
To create a new OU in Active Directory, use the New-ADOrganizationalUnit cmdlet from the RSAT-AD-PowerShell module. To create an OU in the specified container, you can use the command below:
Import-Module ActiveDirectory
New-ADOrganizationalUnit -Name "Users" -Path "OU=Berlin,OU=DE,DC=woshub,DC=com" –Description "Account container for Berlin users" -PassThru
By default, when creating AD containers, the ProtectedFromAccidentalDeletion option is enabled for them. You can disable it or change any other Organizational Unit attribute in Active Directory using the Set-ADOrganizationalUnit cmdlet:
Get-ADOrganizationalUnit -Identity “OU=Users,OU=Berlin,OU=DE,DC=woshub,DC=com”| Set-ADOrganizationalUnit -ProtectedFromAccidentalDeletion $false
To remove an OU with all nested objects, use the following command:
Remove-ADObject -Identity "OU=Users,OU=Berlin,OU=DE,DC=woshub,DC=com” -Recursive
Let’s look at a small PowerShell script to automatically create a typical OU structure in Active Directory for a new company branch office.
Suppose your company has a separate OU for each of its branches with the following structure of nested containers:
Country -City_name --Admins --Computers --Contacts --Groups --Servers --Service Accounts --Users
After creating an OU structure, you need to create branch administrator groups in AD and delegate them privileges on the new OUs:
- City_admins – branch administrators (full control over all branch OUs);
- City_account_managers – users with account operator privileges (create new users, AD password reset, etc.). Assign permissions only to Users and Service Accounts OUs;
- City_wks_admins – HelpDesk Support team with administrator privileges on the branch computers (assign the permissions on the Computers OU, add this group to the local administrators group on computers via GPO).
Here is a basic version of this PowerShell script with comments. The CreateBranchOUs.ps1 script code is available on my GitHub repo:
#Create Active Directory OU structure, security groups and assign permissions for a new branch office
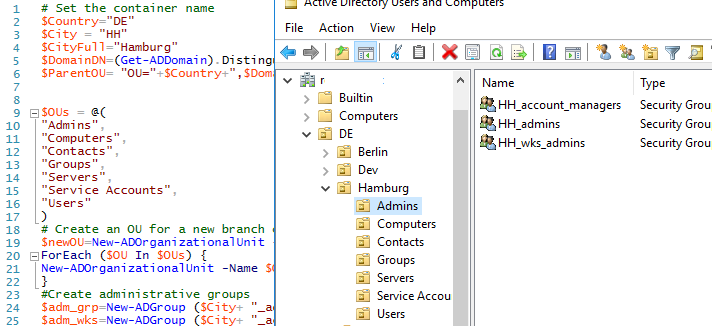
# Set the container name
$Country="DE"
$City = "HH"
$CityFull="Hamburg"
$DomainDN=(Get-ADDomain).DistinguishedName
$ParentOU= "OU="+$Country+",$DomainDN"
$OUs = @(
"Admins",
"Computers",
"Contacts",
"Groups",
"Servers",
"Service Accounts",
"Users"
)
# Create an OU for a new branch office
$newOU=New-ADOrganizationalUnit -Name $CityFull -path $ParentOU –Description “A container for $CityFull users” -PassThru
ForEach ($OU In $OUs) {
New-ADOrganizationalUnit -Name $OU -Path $newOU
}
#Create administrative groups
$adm_grp=New-ADGroup ($City+ "_admins") -path ("OU=Admins,OU="+$CityFull+","+$ParentOU) -GroupScope Global -PassThru –Verbose
$adm_wks=New-ADGroup ($City+ "_account_managers") -path ("OU=Admins,OU="+$CityFull+","+$ParentOU) -GroupScope Global -PassThru –Verbose
$adm_account=New-ADGroup ($City+ "_wks_admins") -path ("OU=Admins,OU="+$CityFull+","+$ParentOU) -GroupScope Global -PassThru –Verbose
##### An example of assigning password reset permissions for the _account_managers group on the Users OU
$confADRight = "ExtendedRight"
$confDelegatedObjectType = "bf967aba-0de6-11d0-a285-00aa003049e2" # User Object Type GUID
$confExtendedRight = "00299570-246d-11d0-a768-00aa006e0529" # Extended Right PasswordReset GUID
$acl=get-acl ("AD:OU=Users,OU="+$CityFull+","+$ParentOU)
$adm_accountSID = [System.Security.Principal.SecurityIdentifier]$adm_account.SID
#Build an Access Control Entry (ACE)string
$aceIdentity = [System.Security.Principal.IdentityReference] $adm_accountSID
$aceADRight = [System.DirectoryServices.ActiveDirectoryRights] $confADRight
$aceType = [System.Security.AccessControl.AccessControlType] "Allow"
$aceInheritanceType = [System.DirectoryServices.ActiveDirectorySecurityInheritance] "Descendents"
$ace = New-Object System.DirectoryServices.ActiveDirectoryAccessRule($aceIdentity, $aceADRight, $aceType, $confExtendedRight, $aceInheritanceType,$confDelegatedObjectType)
# Apply ACL
$acl.AddAccessRule($ace)
Set-Acl -Path ("AD:OU=Users,OU="+$CityFull+","+$ParentOU) -AclObject $acl
Set the variables at the beginning of the script and run it (don’t forget to check your current PowerShell execution policy settings). The script will create an OU structure and groups you need, and delegate password reset permissions to the Users OU.
Set-ACL cmdlet, which also allows you to assign NTFS permissions on files and folders.You can extend the script by adding typical operations that you perform when creating an OU for a new branch office.
For example, you can create Group Policies Objects (GPOs) using PowerShell and link them to the OUs:
$wksGPO=New-GPO -Name ($City +"_WKS_Policy") -Comment "$City Workstations Policy"
Get-GPO $wksGPO | New-GPLink -Target ("OU=Computers,OU="+$City+","+$ParentOU) -LinkEnabled Yes