In this article, we’ll show how to restore the Active Directory domain controller from a previously created System State backup (see the Active Directory backup post), and discuss the types and principles of AD DC recovery.
If a domain controller fails, even if you have a backup, you must select the AD recovery scenario you want to use. It depends on whether you have other healthy domain controllers, whether they are accessible over the network from the site with the failed DC, and whether the Active Directory database on them is consistent.
Replacing a Failed Domain Controller with a New One with AD Replication
If you have several additional domain controllers deployed (which is the recommended configuration for Active Directory), it might be easier to deploy a new domain controller instead of restoring a failed server with the DC role from a backup
After a server is promoted to a DC, the new DC synchronizes (replicates) the NTDS.dit database, GPOs, SYSVOL folder contents, and other AD objects from other healthy DCs that remain online. This is the simplest way to restore the domain controller’s functionality, ensuring that no irreversible changes are made to the Active Directory
Authoritative and Non-Authoritative Active Directory Restore
There are two types of restoring Active Directory Domain Services from a backup that you need to clearly understand before you start:
- Authoritative Restore – after recovery of AD objects, replication is performed from the recovered DC to all other domain controllers in the domain. This type of restoring is used in scenarios where a single DC or all DCs have failed simultaneously (for example, as a result of a ransomware or virus attack), or where a corrupted NTDS.DIT database has been replicated across the domain. This mode increments the Update Sequence Number (USN) on the restored AD object by 100,000. Such restored objects are considered newer by other DCs and are replicated across the domain. Use Authoritative Restore very carefully!If you perform an authoritative restore, you will lose all changes made to AD since the backup was created (AD group membership, Exchange attributes, etc.).
- Non-authoritative Restore – restored DC tells other DCs it has been restored from backup and needs the latest AD changes (a new DSA Invocation ID is created for the DC). This restore mode can be used at remote sites where it is difficult to immediately replicate a large AD database over a slow WAN channel; or if the failed server contained critical data or apps.
Restoring AD Domain Controller from a System State Backup
Let’s say there is only one DC in your domain and that DC becomes unavailable due to a physical server hardware failure. You have a system state backup of the old domain controller and want to restore Active Directory to a brand-new server using authoritative restore mode.
Prepare a new host (physical or virtual) to restore a DC from a backup:
- The new server must be running the same version of Windows Server as the failed DC.
- Perform a clean installation of Windows Server. It is not necessary to set the hostname of the old DC and the IP address.
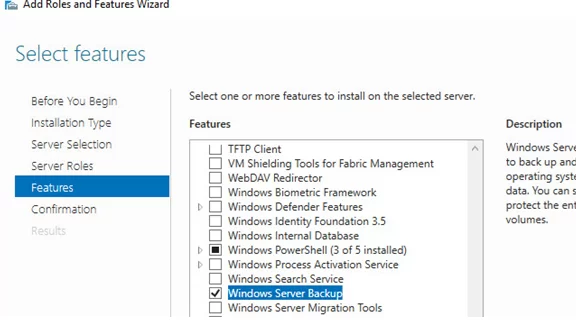
- Install the Active Directory Domain Services role (don’t configure it) and the Windows Server Backup feature. Server Manager or PowerShell can be used to add these components:
Install-WindowsFeature -Name AD-Domain-Services, Windows-Server-Backup
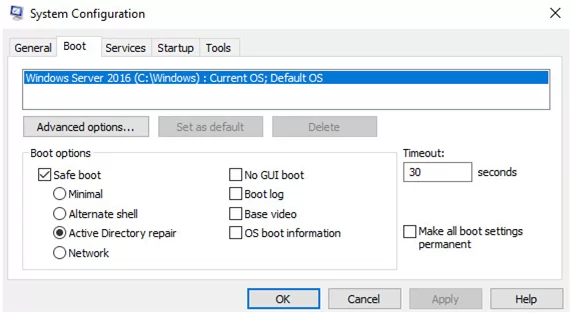
To proceed with the Active Directory restore, boot the server into the Directory Services Restore Mode (DSRM). To do this, run msconfig and on the Boot tab, select Safe Boot -> Active Directory repair. Or run commands:
bcdedit /set safeboot dsrepair
shutdown /r /t 0
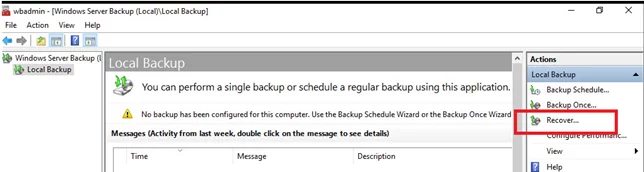
After restart, the server will boot into DSRM safe mode. Open the Windows Server Backup Management snap-in (wbadmin.msc) and select Restore from the right pane.
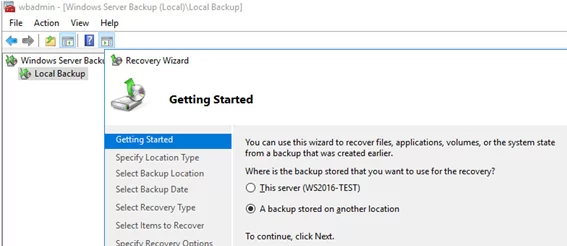
In the Recovery Wizard, select A backup stored on another location.
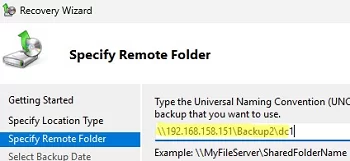
Select the drive where the DC backup is located, or enter the UNC path to the shared network folder where WindowsImageBackup is located. For example, \\192.168.158.151\Backup\DC1 .
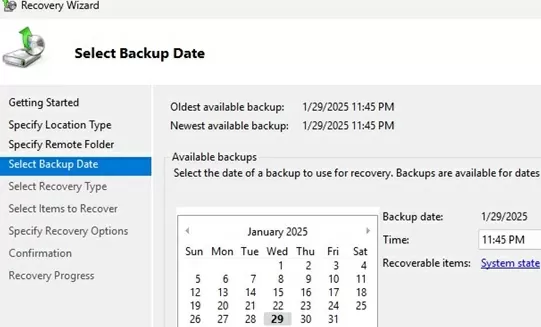
wbadmin get versions -backupTarget:D:Select the date of the backup to be used for recovery.
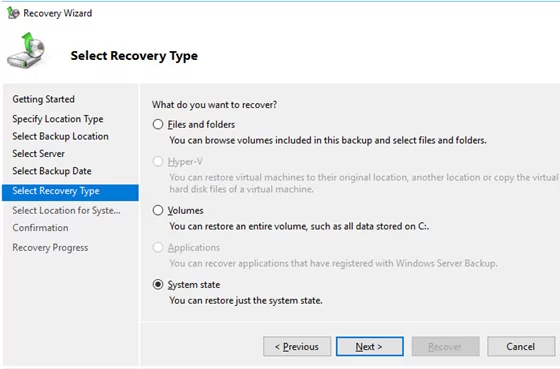
Check the System State to restore.
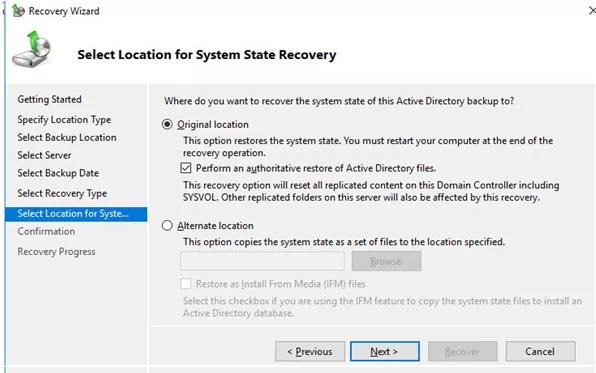
Select the Original location and check the box Perform an authoritative restore of Active Directory files.
As a reminder, we are considering the scenario of an authoritative AD restore when there is only DC in the domain, and there are no other healthy domain controllers!!!
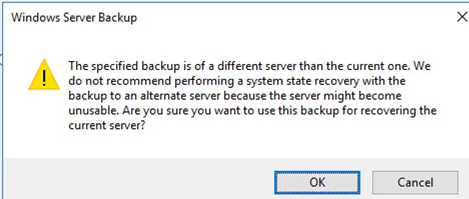
A warning will appear stating that this is a backup from another server and if recovered on a different server it may not work. Click OK.
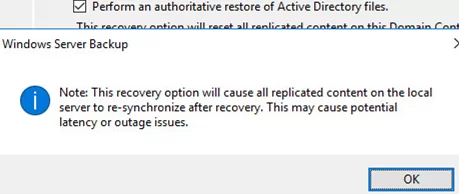
Agree to another warning as well:
Windows Server Backup Note: This recovery option will cause replicated content on the local server to re-synchronize after recovery. This may cause potential latency or outage issues.
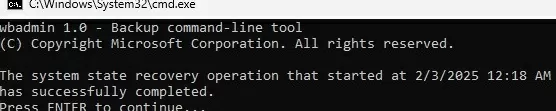
The process of restoring the AD domain controller to a new server will then begin. Once complete, the server will need to be restarted (the server hostname will automatically change to the DC name in the backup).
Login to the server using the local DSRM administrator account after the reboot. Specify the user name in the format .\administrator
Now boot the DC in normal mode by disabling DSRM boot from msconfig or with the command:
bcdedit /deletevalue safeboot
Login to the server using a domain admin account (you can reset the domain administrator password if you don’t know it).
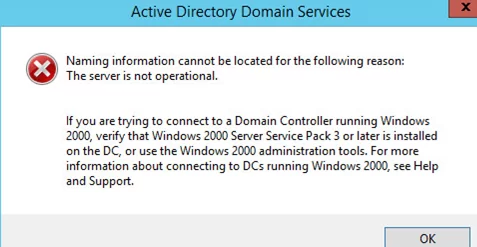
Currently, the ADDS service is not operational. An error occurs when trying to open the Active Directory Users and Computers (ADUC) snap-in:
Active Directory Domain Services Naming information cannot be located for the following reason: The server is not operational.
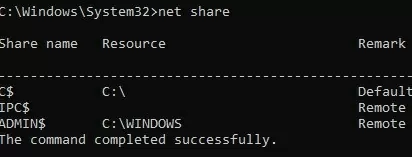
Lists available shared folders:
net share
Note that the SYSVOL and NETLOG shared folders are missing from the restored domain controller.
To fix the error:
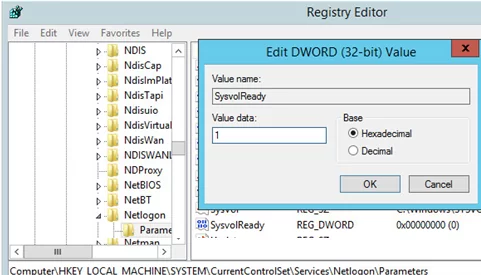
- Run the regedit.exe;
- Go to the registry key HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Netlogon\Parameters;
- Change the SysvolReady value from 0 to 1;
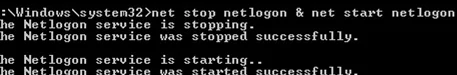
- Then restart the NetLogon service:
net stop netlogon & net start netlogon
Try to open the ADUC console again. You should now see the Organizational Units (OU) structure of the domain.
So, you have successfully recovered your AD domain controller in the Authoritative Restore mode. All objects from the recovered domain controller will be automatically replicated to other DCs
How to Restore Individual Objects in Active Directory
If you have accidentally deleted an AD object, there is no need to restore it from a backup. You can enable the Active Directory Recycle Bin, which allows you to restore deleted AD objects within 180 days (the default value for tombstoneLifetime) using the Restore-ADObject cmdlet or from the Active Directory Administrative Center snap-in.
You can use Authoritative Restore to restore individual AD objects if the tombstone time has expired or ActiveDirectory RecycleBin is not enabled. This can be used by running the ntdsutil command in DSRM mode.
- List the available back:
wbadmin get versions - Start restoring from the selected backup:
wbadmin start systemstaterecovery –version:[your_version] - Confirm the DC restore (in the Non-Authoritative mode)
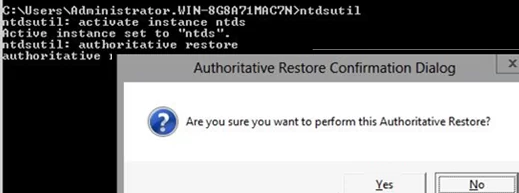
- After the restart, run the
ntdsutil activate instance ntdsauthoritative restore- Specify the full LDAP path to the object you want to restore.
To restore the entire OU:
restore subtree "OU=Users,DC=woshub,DC=com"
Or a single AD object:
restore object "cn=Test,OU=Users,DC=woshub,DC=com"
This command prevents the specified objects from being replicated from other domain controllers and increases the object’s USN by 100000. This ensures that replication considers these objects as new (updated) and copies them to all DCs in the domain.
Exit from ntdsutil:
quit
Boot the DC in normal mode and check that the deleted AD object has been restored.
12 comments
Login after performing a system state backup fails. Account that had administrator privileges in the domain that was restored now can’t log in. Local login also doesn’t go through.
Hi!
Just to be sure….
I’ve a recent system state backup on a network share and my 2 hdd died…
Can I just install a clean w2008 r2, add the 2 roles and perform the restore? Will it recreate the entire domain controller / active directory objects? Is it so easy? (i don’t need the user data and apps installed…). I’ve 25 clients in that domain…I don’t want to reconfigure those pc on a new domain…
I’ve run into the same issue that P3T did – I restored the backup, and now when I try to log in using the domain admin account I get “Invalid function”. If I try a local admin account or a server admin account it says my username/password is incorrect.
Try logging in with DSRM password
Kan vara för att maskinen fortfarande ligger i safe boot. då loggar du bara in på maskinen med det som går, ex gäst eller lokalkonto. går in på msconfig och under boot klicka ur safe boot. Nu borde du få logga in med domänadmin om du loggar ut och in dig igen.Could be because the machine is still in safe boot. then you just log in to the machine with whatever works, e.g. guest or local account. go to msconfig and under boot click out of safe boot. Now you should be able to log in with domain admin if you log out and log in again.
Try login with DSRM Password
put .\Administrator and type password used while you were promoting your AD server
AD restore from system state backup is not supported by Microsoft.
This is not a correct statement. I just did for one of my client, he had only one AD. I had a system state backup.
Hello, which is the proper method for restoring a lone domain controller – it’s the only dc in the network (very small site), thus no replication…
Kind regards,
Mihai, what is your situation – do you have a full backup? You should be able to restore from that; the same situation I went through above. The DSRM password was the key to get it all working again.
Authoritative Restore, Follow this thread carefully, there is one critical piece missing for the standalone DC and no other DC available.
1. Same IP as the old or Dead DC
2. Just need a new clean OS
3. keep your old local Admin accounts creds handy of the exDC Server. For help reach me on Github @ramzcode
“…Install the ADDS role (don’t configure it)…” This is where the process fails. The machine is not a DC and, at least in server 2022, will absolutely not boot into DSRM even after the msconfig step. DCPromo has to run in order for the ADDS and all its bits and bobs (like DSRM) to be functional.