When you delete an object in Active Directory (user, group, computer, or OU), it is not permanently removed right away. Within 180 days, deleted AD objects can be recovered by using graphical tools or PowerShell/console commands.
When an object is deleted from Active Directory, it is not physically removed from the database, instead, it is marked as logically deleted (the isDeleted attribute value changes to true). A deleted AD object can be restored within 180 days (the default value set in the msDS-deletedObjectLifetime domain attribute).
Before attempting to restore an accidentally deleted object, check whether the Active Directory Recycle Bin is enabled or disabled in the domain. Your next steps will depend on this.
Active Directory Recycle Bin on Windows Server
The Active Directory Recycle Bin is available in AD starting from the Windows Server 2008 R2 functional level. This Recycle Bin for deleted objects makes it much easier to restore objects in AD without losing attributes and group memberships.
Deleted Objects container, but most of its attributes and links are cleared (Recycled Object). After the tombstoneLifetime period expires (also 180 days by default, but it can be increased), the object is completely removed from AD by an automatic cleanup task and cannot be restored (such objects can only be recovered from an AD domain controller backup).Use PowerShell to verify that the Recycle Bin is enabled in your AD forest (the AD Recycle Bin is disabled by default and can only be enabled manually by the enterprise administrators).
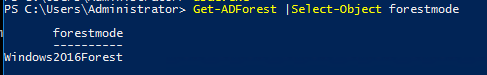
Make sure that the AD forest level is not lower than the Windows2008R2Forest:
Get-ADForest |Select-Object forestmode
Check if AD Recycle Bin is enabled in the forest
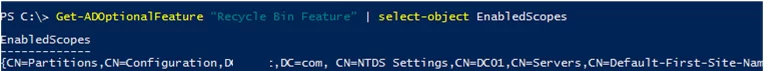
Get-ADOptionalFeature "Recycle Bin Feature" | select-object name,EnabledScope
- If the EnabledScopes value is not empty. It means that the Active Directory Recycle Bin is already enabled in your domain. In this case, go to the section of this article that describes how to restore deleted items from the AD Recycle Bin.
- If the Recycle Bin is disabled, you must follow the instructions in the Recovering a deleted user without the AD Recycle Bin section.
Therefore, you should not enable the Recycle Bin until you’re certain that none of the previously deleted AD objects need to be restored
To enable the Active Directory Recycle Bin, use the Enable-ADOptionalFeature cmdlet:
Enable-ADOptionalFeature "Recycle Bin Feature" -Scope ForestOrConfigurationSet -Target "woshub.com"
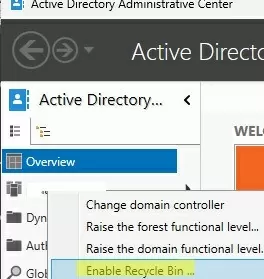
Or, more easily, use the Active Directory Administrative Center graphical console (dsac.exe). Launch the ADAC console, connect to the root domain, click on the domain name, and select Enable Recycle Bin.
How to Restore a Deleted User with AD Recycle Bin
Let’s look at a simple example of how to restore a deleted object using the Active Directory Recycle Bin. For example, we will delete a user account and then try to restore it from the AD Recycle Bin.
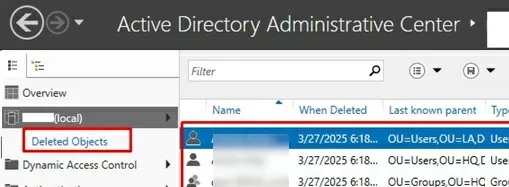
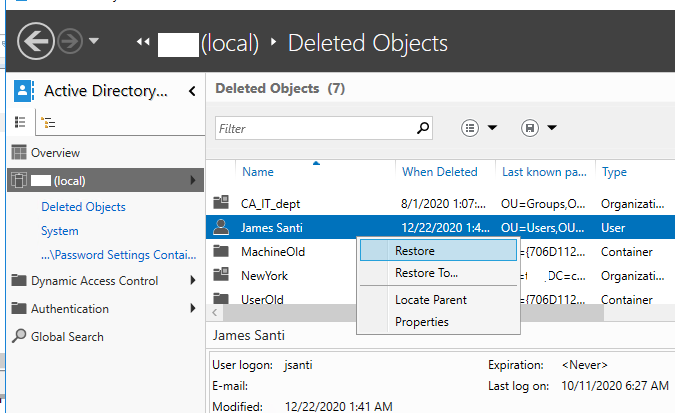
Once the AD Recycle Bin is enabled, all deleted objects are moved to a special hidden container, Deleted Objects. Find this container in the Active Directory Administrative Center console (dsac.exe).
All deleted objects are displayed here, including users, computers, contacts, groups, and OUs. Deletion date and original OU (last known parent) are also listed.
To restore an object, right-click on it and choose Restore (to restore to the original OU) or Restore to (to restore it to an arbitrary AD container).
When a deleted user is restored from the Recycle Bin, most of the object’s attribute values and its AD group memberships are also restored.
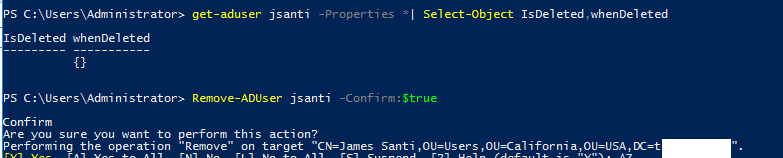
Use the Get-ADUser cmdlet to display the value of the IsDeleted attribute of a user (it is empty):
get-aduser jsanti -Properties *| Select-Object IsDeleted,whenDeleted
Then, remove the user account:
Remove-ADUser jsanti
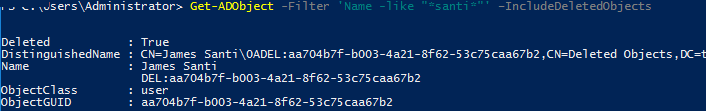
To find a deleted user account in the AD Recycle Bin, use the Get-ADObject cmdlet with the IncludeDeletedObjects parameter:
Get-ADObject -Filter 'Name -like "*santi*"' –IncludeDeletedObjects
As you can see, the user was found in the Deleted Objects container.
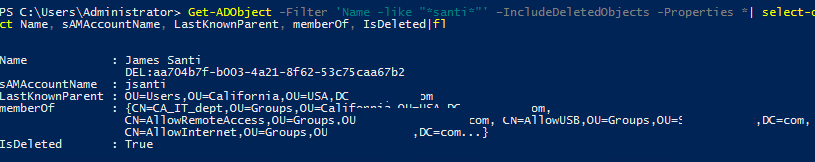
Check the value of the IsDeleted attribute, the container where the user was located before deletion (LastKnownParent), and the list of groups the user was a member of:
Get-ADObject -Filter 'Name -like "*santi*"' –IncludeDeletedObjects -Properties *| select-object Name, sAMAccountName, LastKnownParent, memberOf, IsDeleted|fl
Get-ADObject –filter {Deleted -eq $True -and ObjectClass -eq "user"} –includeDeletedObjects
Copy the ObjectGUID value and run the following command to restore a deleted user account
Restore-ADObject -Identity ‘aa704b7f-b003-4a21-8f62-53c75caa67b2
Or restore a user by using it SAMAccountName:
Get-ADObject -Filter 'SAMAccountName -eq "jsanti"' –IncludeDeletedObjects | Restore-ADObject
Open the ADUC console (dsa.msc) and confirm that the user account has been restored to the same container (OU) it was located in prior to deletion. The user account will be disabled after the restore operation is complete. Enable the AD account and reset the password before giving it to the user.
In the same way, you can restore a deleted group, a computer or a container in Active Directory.
To restore a deleted security group:
Get-ADObject -Filter { Deleted -eq $True -and ObjectClass -eq 'group' -and Name -like '*Allow*' } –IncludeDeletedObjects| Restore-ADObject –verbose
To restore a computer account:
Get-ADObject -Filter { Deleted -eq $True -and ObjectClass -eq 'computer' -and Name -like '*PCCA-sdd9302*' } –IncludeDeletedObjects| Restore-ADObject –verbose
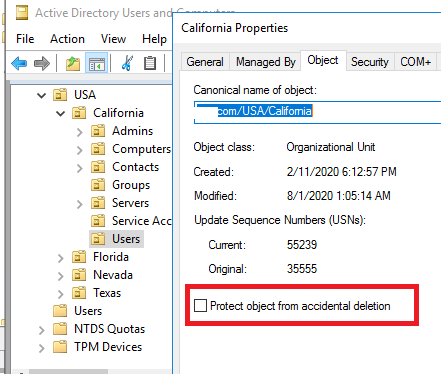
Let’s consider another scenario. For example, suppose you accidentally deleted an OU with all its nested users, computers, and groups because the Protect object from accidental deletion option was disabled for that OU.
It is not possible to automatically restore an object and its hierarchy from the AD Recycle Bin. Restore a deleted OU and all its nested objects using a PowerShell script.
- First, restore the root OU:
Get-ADObject -Filter {Deleted -eq $True
-and ObjectClass -eq 'organizationalunit' -and Name -like
'*California*'} –IncludeDeletedObjects| Restore-ADObject - Then, restore all nested OUs:
Get-ADObject -Filter {Deleted -eq $True
-and ObjectClass -eq 'organizationalunit' -and LastKnownParent -eq
'OU=California,DC=woshub,DC=com'} –IncludeDeletedObjects|
Restore-ADObject - No,w recover all deleted objects in these OUs by the LastKnownParent parameter (users, computers, groups, contacts):
Get-ADObject -Filter {Deleted -eq $True}
–IncludeDeletedObjects -Properties *| Where-Object LastKnownParent -like
'*OU=California,DC=woshub,DC=com'| Restore-ADObject
Restore Deleted Objects without AD Recycle Bin
If the Active Directory Recycle Bin is disabled in your forest, you can restore deleted objects using the ldp.exe utility (a simple but cumbersome method) or the official adrestore.exe tool from Microsoft, which is a faster and more user-friendly option
- Download the AdRestore archive (https://learn.microsoft.com/en-us/sysinternals/downloads/adrestore) and extract it on the domain controller
- Open an elevated command prompt and list the deleted objects in the domain:
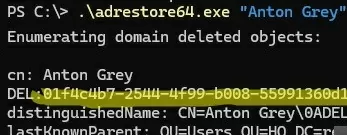
.\adrestore64.exe - To get information about a specific removed user, enter the user’s name:
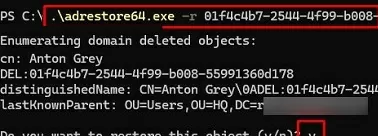
.\adrestore64.exe "Anton Grey" - To restore an object, copy its GUID and run the command:
.\adrestore64.exe -r GUID - Confirm the object restore:
y - Verify that the user has been restored to the source OU:
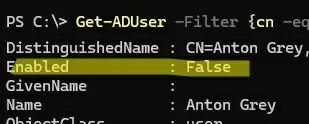
Get-ADUser -Filter {cn -eq "Anton Grey"} - After restoring, the user account is disabled, and the password is not set. You must reset the user’s password and enable the account:
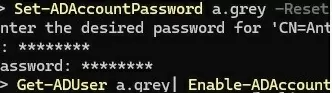
Set-ADAccountPassword agrey -Reset
Get-ADUser agrey| Enable-ADAccount
When using this method of restoring objects (as opposed to restoring using the AD Recycle Bin), most user attribute values, including group memberships, will be lost. Only basic attributes such as GUID, SID, CN, etc., will remain.
Recovering accidentally deleted accounts in AD is much easier with a Recycle Bin. However, the AD Recycle Bin does not replace the need for a full AD backup