Microsoft recently announced that mandatory SMB packet signing for access to shared network folders will be enabled by default in Windows 11 24H2. This may cause problems when accessing shared folders on NAS (Network Attached Storage) devices where SMB signing is not supported or disabled by default.
SMB signing is required for all outbound SMB connections starting with Windows 11 24H2 (Accessing a third-party NAS with SMB in Windows 11 24H2 may fail). If the SMB server doesn’t support this mode, the Windows client will reject the connection. Other supported versions of Windows will later receive this change.
If the remote device does not support SMB signing, errors will occur when accessing a shared folder on that device:
-
0xc000a000 -1073700864-
STATUS_INVALID_SIGNATURE -
The cryptographic signature is invalid
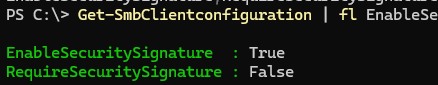
The default Windows (and Samba) SMB server settings assume that SMB packet signing is only used when requested by one of the parties. Use PowerShell to list the current SMB signing settings on a Windows client:
Get-SmbClientconfiguration | fl EnableSecuritySignature,RequireSecuritySignature
- RequireSecuritySignature = False — mandatory use of the SMB signature is not enabled.
- EnableSecuritySignature = True – the client only uses SMB signing when required by the server.
To disable (or enable) mandatory SMB signing, use the command
Set-SmbClientConfiguration -RequireSecuritySignature $false
Restart the computer after changing the settings.
In the same way, you can enable or disable SMB signing on the server side (host with shared folders):
Get-SmbServerConfiguration | fl *sign*
Set-SmbServerConfiguration -RequireSecuritySignature $true (or $false )
The EnableSecuritySignature option value is ignored if the legacy SMB1 protocol is disabled (this is the default behavior in Windows).
These SMB client and server options can be enabled via the registry. The next set of commands will turn off the mandatory use of SMB signing for both the client and the server:
reg add "HKLM\SYSTEM\CurrentControlSet\Services\LanManServer\Parameters" /v RequireSecuritySignature /t REG_DWORD /d 0 /f
reg add "HKLM\SYSTEM\CurrentControlSet\Services\LanManServer\Parameters" /v EnableSecuritySignature /t REG_DWORD /d 1 /f
reg add "HKLM\SYSTEM\CurrentControlSet\Services\LanmanWorkstation\Parameters" /v RequireSecuritySignature /t REG_DWORD /d 0 /f
reg add "HKLM\SYSTEM\CurrentControlSet\Services\LanmanWorkstation\Parameters" /v EnableSecuritySignature /t REG_DWORD /d 1 /f
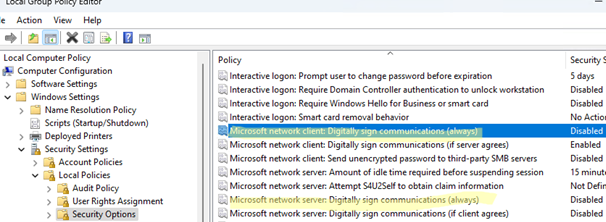
The GPO editor can also be used to configure the SMB signing mode for a Windows client. The following options are available in the local Group Policy Editor (gpedit.msc) under Computer Configuration -> Windows Settings -> Security Settings -> Local Policies -> Security Options
- Microsoft network client: Digitally sign communication (always)
- Microsoft network client: Digitally sign communication (if server agrees)
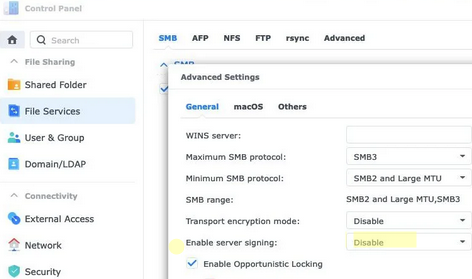
Some NAS models and firmware versions support the SMB signing mode, but it is not enabled by default (for example in Synology, ASUStor, QNAP, and some other devices). For example, in Synology DSM 7+, this option can be found in the Control Panel -> File Services -> SMB -> Advanced Settings. Find the option Enable server signing. Signing is disabled by default. To enable SMB signing when requested by the client, select Client defined from the drop-down menu.
Thus, if you experience problems when accessing NAS shares after upgrading to Windows 11 24H2, you will need to:
- Enable SMB signing on the NAS device (recommended way)
- Disable mandatory SMB signing on the Windows client (less secure option)