When creating new user accounts in Active Directory, an administrator sets a unique initial password for each account and tells it to a user (usually at the first logon a user is prompted to change this password by the option “User must change password at next logon” of the AD userAccountControl attribute). If you do not want to invent a new random password for each user or you are using a PowerShell script to create AD accounts, you can generate unique passwords automatically using a simple PowerShell script.
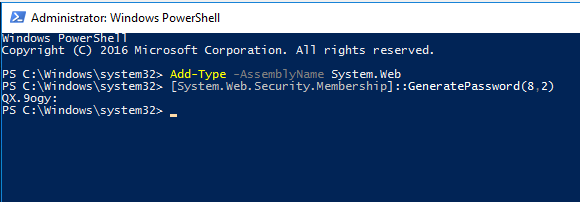
To generate a password, you can use the GeneratePassword method from the System.Web.Security.Membership class of .NET. Let’s generate a strong random password using the following PowerShell commands:
# Import System.Web assembly
Add-Type -AssemblyName System.Web
# Generate random password
[System.Web.Security.Membership]::GeneratePassword(8,2)
The GeneratePassword method allows to generate a password up to 128 characters. The method uses two initial parameters: the password length (8 characters in my case) and the minimum number of non-alphabetical or non-numerical special characters, like !, -, $, &, @, #, %, etc(2 special characters). As you can see, according to these arguments the following password has been generated for me: QX.9ogy:
k};E^]$|).Thus, if you create new users with the New-ADUser PowerShell cmdlet and want to set unique passwords for them, use the following commands:
Add-Type -AssemblyName System.Web
New-ADUser -Name "Jeremy Irons" -GivenName "Jeremy" -Surname "Irons" -SamAccountName "jirons" -UserPrincipalName "jirons@woshub.com" -Path "OU=Users,OU=Glasgow,OU=UK,DC=woshub,DC=com" –AccountPassword ([System.Web.Security.Membership]::GeneratePassword(8,2)) -ChangePasswordAtLogon $true -Enabled $true
If your company is using a strong password policy, in some cases a password generated with the GeneratePassword method may not meet the requirements of your AD domain password policy. Prior to setting a password to a user, you can make sure that it complies with the password complexity policy. Of course, it does not make sense to check its length and the presence of username in a password. You may check if the password meets at least 3 requirements of the “Password must meet complexity requirements” policy (the password must contain at least 3 types of characters from the following list: numbers, lower-case characters, UPPER-case characters, and special characters). If the password check failed, you would have to re-generate it.
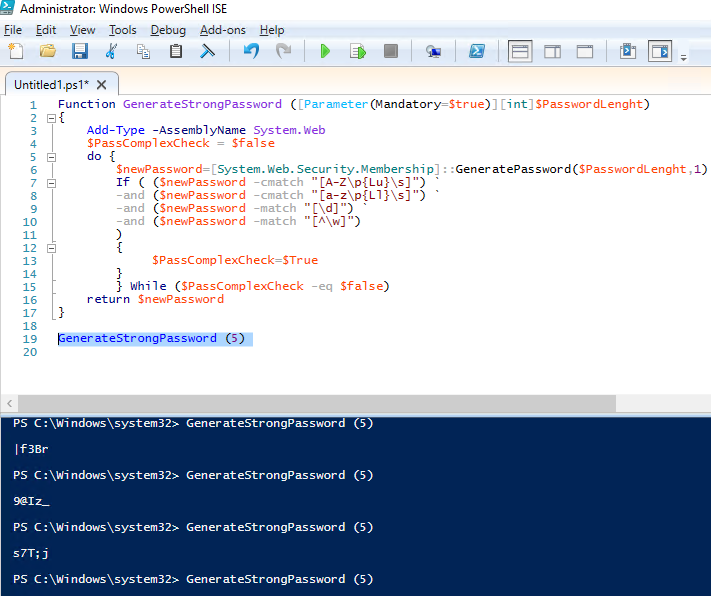
I have written a small PowerShell script that generates a new random password and checks if it meets the password complexity requirement:
Function GenerateStrongPassword ([Parameter(Mandatory=$true)][int]$PasswordLenght)
{
Add-Type -AssemblyName System.Web
$PassComplexCheck = $false
do {
$newPassword=[System.Web.Security.Membership]::GeneratePassword($PasswordLenght,1)
If ( ($newPassword -cmatch "[A-Z\p{Lu}\s]") `
-and ($newPassword -cmatch "[a-z\p{Ll}\s]") `
-and ($newPassword -match "[\d]") `
-and ($newPassword -match "[^\w]")
)
{
$PassComplexCheck=$True
}
} While ($PassComplexCheck -eq $false)
return $newPassword
}
To generate a password having 5 characters and at least one special character, run this command:
GenerateStrongPassword (5)
This script will always create a password that meets your AD password complexity policy.
2 comments
Didn’t know of this simple method, thanks for sharing. I turned your script into an easy foolproof function 😉
function Get-Password
{
[CmdletBinding()]
param
(
[Parameter(Mandatory=$false)]
[int]
$Length = (Read-Host ‘Password length (1 – 128)’),
[Parameter(Mandatory=$false)]
[int]
$NonAlphabeticChars = (Read-Host ‘The number of Non-alphabetic characters’)
)
try
{
Add-Type -AssemblyName System.Web
[System.Web.Security.Membership]::GeneratePassword($Length,$NonAlphabeticChars)
}
catch [System.ArgumentException]
{
# retrieve information about runtime error
$info = [PSCustomObject]@{
Exception = $_.Exception.Message
Reason = $_.CategoryInfo.Reason
Target = $_.CategoryInfo.TargetName
Script = $_.InvocationInfo.ScriptName
Line = $_.InvocationInfo.ScriptLineNumber
Column = $_.InvocationInfo.OffsetInLine
}
# output information. Post-process collected info, and log info (optional)
$info
}
}
H Everyone,
Can somebody help me with creating new user with generating strong password with above script?