Active Directory (AD) is a hierarchical directory service from Microsoft that is used in a Windows domain environment to organize and centrally manage different types of objects: computers, users, servers, printers, etc. AD is at the heart of management and authentication in Windows Domain organizations. Active Directory is tightly integrated with many Microsoft services and applications such as DNS, DHCP, Exchange Server, etc. Because all user accounts are stored in a single AD database, users can log into any computer in the AD domain using their personal account and password (this is unlike a workgroup, where each computer has its own local database of users).
Understanding Active Directory concepts and architecture
AD is organized in a hierarchical structure. The AD architecture consists of the following basic elements:
- AD forest – the top level of the Active Directory hierarchical structure. A forest is a collection of related domains that share a common schema, structure, and global catalog;
- Domain – a separate area within the AD forest, with its own security boundary and replication. Contains users, computers, groups, and other objects;
- Organizational Unit (OU) – Containers for logical grouping of objects within a domain (similar to folders on a drive). The OU is the point at which the GPO is linked and AD permissions are delegated;
- In order to install an Active Directory domain, you will need to install the Active Directory Domain Services (ADDS) role on the Windows Server machine. This server is called an Active Directory Domain Controller (DC). Depending on the needs and size of the domain, a domain can have one or more domain controllers. Domain controller authenticates users and services requests to access network resources (used as a logon server);
- The Active Directory database (NTDS.DIT) is stored on the domain controller. Each domain controller stores its own copy of the AD database and replicates any new or changed data to other DCs;
- Active Directory Sites – AD objects, one or more physical IP subnets connected by fast LAN channels. Typically, AD sites reflect physical geographic or logical boundaries within your corporate network. Clients authenticate and retrieve GPO files from domain controllers at their sites. There can be one or more domain controllers at each site. To reduce the load on WAN links, you can configure replication intervals between sites;
- Global Catalog (GC) – this role can be assigned to any domain controller. This DC is used to perform lookups and authentication across domains. It also stores a summary of object information across the forest;
- Group Policy Objects (GPO) — allows administrators to configure settings for domain computers and users centrally;
- AD Schema – defines the structure and the possible attributes of the objects in the Active Directory.
Install and configure Active Directory domain controller on Windows Server
Let’s take a look at some useful guides for the installation, configuration, and maintenance of AD domain controllers:
- Installing AD controller on Windows Server Core
- Adding an additional DC to an existing AD domain
- How to demote (remove) a domain controller from Active Directory
- How to properly rename the AD domain
- Install and Configure Read-Only Domain Controller (RODC)
- Checking AD domain controller health and replication state
- How to backup and restore the Active Directory domain controller
- Reset domain administrator password in AD
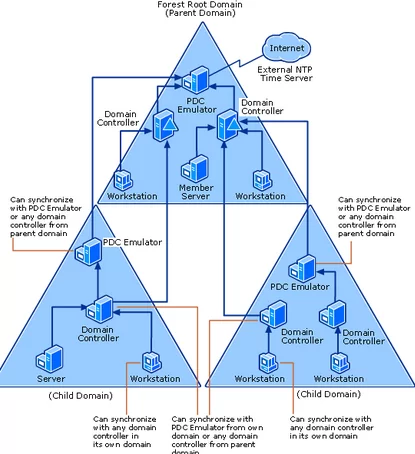
Active Directory domain controllers are equal and perform the same functions. However, in order to prevent conflicting updates, some operations in AD require the change source controller to be unique. These operations are called Flexible Single-Master Operations (FSMO), and the Domain Controllers that perform FSMO roles are called Operations Masters.
There are five FSMO roles:
- Schema Master
- Domain Naming Master
- Infrastructure Master
- RID Master
- PDC Emulator
The list of Operation Master DCs holding FSMO roles can be displayed using the following command
netdom query fsmo
You can move FSMO roles from one domain controller to another.
Active Directory management tools
In the Windows environment, several tools are available to help administer Active Directory. You can use both graphical MMC snap-ins, command-line tools, and PowerShell cmdlets for AD management:
- Active Directory Users and Computers ADUC (
dsa.msc) MMC console – is One of the most widely used AD administration tools. It allows you to create, edit attributes, delete, and move various AD objects: users, computers, groups, organizational units (OUs); - ADAC (Active Directory Administrative Center) – the basic functionality is similar to ADUC, but has more possibilities for the management of child domains;
- ADSS (Active Directory Sites and Services) — used to manage AD sites, subnets, topology, and replication schedule;
- ADDT (Active Directory Domains and Trusts) – used to manage trust relationships between domains and establish cross-domain connections;
- AD Schema – AD schema management tool;
- GPMC (Group Policy Management,
gpmc.msc) – used to manage Group Policy Objects (GPOs) in the AD domain; - ADSIEdit – MMC snap-in that allows you to connect to the LDAP AD directory database and edit attributes and configuration at a lower level;
- Active Directory module for Windows PowerShell includes all the cmdlets you need to manage AD objects, settings, and policies from the PowerShell console.
Add-WindowsCapability –online –Name Rsat.ActiveDirectory.DS-LDS.Tools~~~~0.0.1.0
Manage users, groups, and computers in Active Directory
There are many detailed Active Directory setup and administration guides available on our website. The following is a list of typical operations with different types of AD objects:
Active Directory machine (computer) accounts:
- Join a Windows computer to an Active Directory domain
- Cached domain logon credentials on Windows
- Deny and allow workstation logons in Active Directory
- Fill the AD computer description with PowerShell
- Repairing the trusted relationship between the workstation and the AD domain
Active Directory users:
- Create a new user account in Active Directory
- How to find the source of AD account lockouts
- Unlock user account in Active Directory
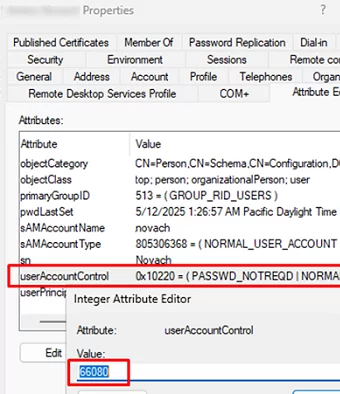
- Change (reset) a user’s password in Active Directory
- Managing UserPrincipalName and UPN suffixes in Active Directory
- Notify AD users when their password is about to expire
- Add user to local administrator group on AD computers
Active Directory groups:
- How to create an AD group with dynamic membership using PowerShell
- Temporary group membership in Active Directory
Other Active Directory features and usage scenarios