SID (Security IDentifier) is a unique identifier that is assigned to users, groups, computers, or other security objects when they are created in Windows or Active Directory domain. Windows uses the SID, but not the username, to control access to different resources: shared network folders, registry keys, file system objects (NTFS permissions), printers, etc. In this article, we’ll show you some simple ways to find the SID of a user, group, or computer, and the reverse procedure – how to get an object name by a known SID.
What is SID (Windows Security Identifier)?
As we said, SID (security identifier) allows you to uniquely identify a user, group, or computer within a certain scope (domain or local computer). SID is a string of the form:
S-1-5-21–489056535-1467421822-2524099697–1231
- 489056535-1467421822-2524099697– this is the unique identifier of the domain that issued the SID (this part will be the same for all objects in the same domain):
- 1231 – the object’s relative security identifier (RID). It starts at 1000 and increases by 1 for each new object. Issued by a domain controller with FSMO role RID Master.
SIDs of Active Directory objects are stored in the ntds.dit database, and SIDs of local users and groups in the local Windows Security Account Manager (SAM) database in the HKEY_LOCAL_MACHINE\SAM\SAM registry key.
There are so-called Well-known SIDs in Windows. These are the SIDs for built-in users and groups on any Windows computer. For example:
S-1-5-32-544– built-in Administrators groupS-1-5-32-545– local usersS-1-5-32-555– Remote Desktop Users group that are allowed to log in via RDPS-1-5-domainID-500– built-in Windows administrator account- Etc.
On Windows, you can use various tools to convert SID -> Name and Username -> SID: whoami tool, wmic, WMI classes, PowerShell, or third-party utilities.
How to Find a Local User Security Identifier (SID)
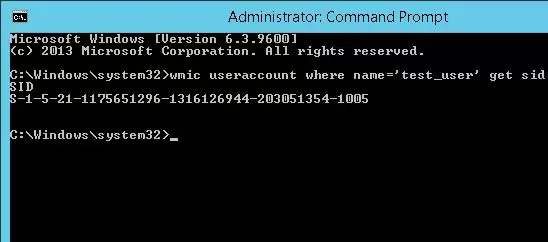
To get the SID of the local user account, you can use the wmic tool, which allows you to query the computer’s WMI namespace. To get the SID of the local user test_user, you can use the WMIC command:
wmic useraccount where name='test_user' get sid
The command above returned the SID of the specified local user. In this example – S-1-5-21-1175659216-1321616944-201305354-1005.
To list the SIDs of all local Windows users, run:
wmic useraccount get name,sid
If you need to get the SID of the current user, run the following command:
wmic useraccount where name='%username%' get sid
You can query WMI directly from PowerShell:
(Get-WmiObject -Class win32_userAccount -Filter "name='test_user' and domain='$env:computername'").SID
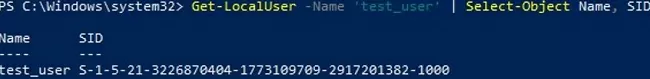
Get-CimInstance instead of the Get-WmiObject cmdlet.But it’s even easier to get the SID of a local user by using PowerShell:
Get-LocalUser -Name 'test_user' | Select-Object Name, SID
In the same way, you can get the SID of a group of the local computer:
Get-LocalGroup -Name tstGroup1 | Select-Object Name, SID
You can also use the .NET classes System.Security.Principal.SecurityIdentifier and System.Security.Principal.NTAccount to get the user’s SID via PowerShell:
$objUser = New-Object System.Security.Principal.NTAccount("LOCAL_USER_NAME")
$strSID = $objUser.Translate([System.Security.Principal.SecurityIdentifier])
$strSID.Value
How to Get User/Group SID in Active Directory
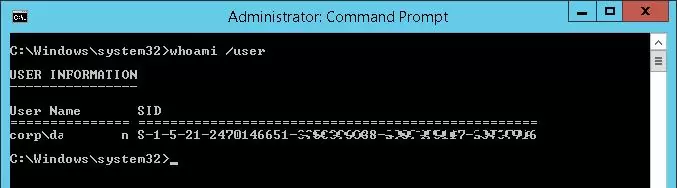
The following command can be used to get a SID of the current domain account:
whoami /user
You can find the SID of an Active Directory domain user using WMIC tool. You must specify your domain name in the following command:
wmic useraccount where (name='jjsmith' and domain=′corp.woshub.com′) get sid
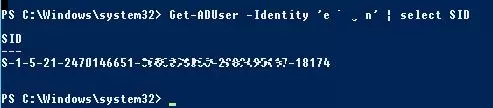
To find the SID of an AD domain user, you can use the Get-ADUser cmdlet which is a part of the Active Directory Module for Windows PowerShell. Let’s get the SID for the jabrams domain user account:
Get-ADUser -Identity 'jabrams' | select SID
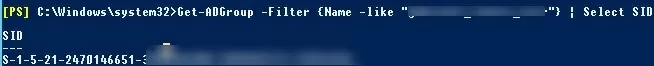
You can get the SID of an AD group using the Get-ADGroup cmdlet:
Get-ADGroup -Filter {Name -like "fr-sales-*"} | Select SID
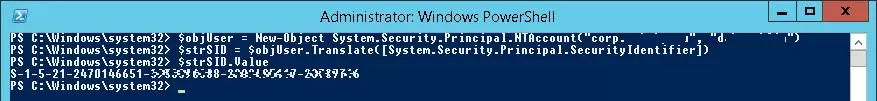
If the PowerShell AD module is not installed on your computer, you can get the user’s SID from the AD domain using the .Net classes mentioned earlier:
$objUser = New-Object System.Security.Principal.NTAccount("corp.woshub.com","jabrams")
$strSID = $objUser.Translate([System.Security.Principal.SecurityIdentifier])
$strSID.Value
The same PowerShell one-liner command:
(new-object security.principal.ntaccount “jabrams").translate([security.principal.securityidentifier])
Checking the Domain and Local Machine SID of a Computer
If a Windows computer is joined to an Active Directory domain, it will have two different SIDs. The first SID is the local computer identifier (Machine SID), and the second is the unique computer object identifier in AD.
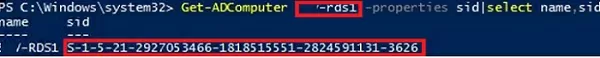
You can get the SID of a computer in the Active Directory domain using the command:
Get-ADComputer mun-rds1 -properties sid|select name,sid
The SID of the local computer (Machine SID) can be obtained using the PsGetSID tool (https://docs.microsoft.com/en-us/sysinternals/downloads/psgetsid). But you have to download and install the tool on each computer manually.
.\PsGetsid64.exe
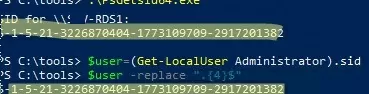
Or simply by trimming the last 4 characters (RID) from the SID of any local user:
$user=(Get-LocalUser Administrator).sid
$user -replace ".{4}$"
sysprep utility before joining them to the domain. This tool resets the local Machine SID. This will save you from common trust relationship errors.How to Convert a SID to a User or Group Name
To find out the name of the user account by the SID (a reverse procedure), you can use one of the following commands:
wmic useraccount where sid='S-1-3-12-12451234567-1234567890-1234567-1434' get name
You can get the domain user’s name by a SID using the RSAT-AD-PowerShell module:
Get-ADUser -Identity S-1-3-12-12451234567-1234567890-1234567-1434
To find the domain group name by a known SID, use the command:
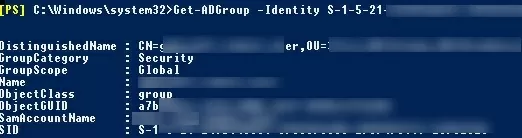
Get-ADGroup -Identity S-1-5-21-247647651-3965464288-2949987117-23145222
You can also find out the group or user name by SID with the built-in PowerShell classes (without using additional modules):
$objSID = New-Object System.Security.Principal.SecurityIdentifier ("S S-1-3-12-12451234567-1234567890-1234567-1434")
$objUser = $objSID.Translate( [System.Security.Principal.NTAccount])
$objUser.Value
Searching Active Directory by SID using PowerShell
If you don’t know what type of AD object a certain SID belongs to and what exact PowerShell cmdlet you need to use to find it (Get-AdUser, Get-ADComputer, or Get-ADGroup), you can use the universal method of searching objects in the Active Directory domain by a SID using the Get-ADObject cmdlet.
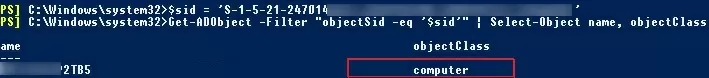
$sid = ‘S-1-5-21-2412346651-123456789-123456789-12345678’
Get-ADObject –IncludeDeletedObjects -Filter "objectSid -eq '$sid'" | Select-Object name, objectClass
IncludeDeletedObjects parameter allows you to search for deleted objects in the Active Directory Recycle Bin.In our case, the AD object with the specified SID is a domain computer (see the objectClass attribute).
5 comments
This was very useful, and thank you. I’ve noticed SIDs on files in O365, that are grouped in the format “S——. Additionally, some SIDs have another “2” 10-digit strings appended.
Do you happen to know what these mean? And why some have more groups of numbers than others? Are they group SIDs, perhaps, that are appended? Thanks very much in advance.
Perhaps you have in mind not the SIDs, but the SDDL (Security Descriptor Definition Language) file permission format?
Check out the article: https://woshub.com/how-to-backup-and-restore-ntfs-permissions-using-icacls/
Excellent! Showing multiple ways to obtain result. Love the PowerShell one-liner for obtaining “SID from User” and the $objSID + $objUser to obtain the “User from SID” that you shared. Those work for both Local and Domain cross reference!
Use this post at work, thank you.
Another command that could be added to the post is a simple command to see you’re own domain User SID using the whoami command like this at a command prompt: whoami /user .
fantastic, works like a charm.
thankyou