This article shows how to allow anonymous access to shared network folders and printers on a computer in a workgroup or Active Directory domain. Anonymous access to a remote computer means that users do not need to authenticate (without the need to enter credentials or passwords) to access a shared resource and a Guest account is used for access.
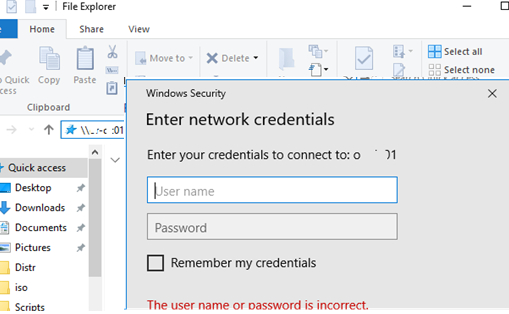
By default, when you access a shared folder on a remote computer, you are prompted for a username and password (except in cases where both computers are in the same domain, or workgroup and use the same local user accounts with the same passwords). Anonymous access means that when you connect to a remote computer, you are not prompted for a password and can access shared resources without authentication.
Configuring Anonymous Access Settings in Windows
Windows uses a special built-in guest account for anonymous access. This account is disabled by default.
To allow anonymous (unauthenticated) access to the computer, you need to enable the Guest account and change some settings of the Local Security Policy in Windows.
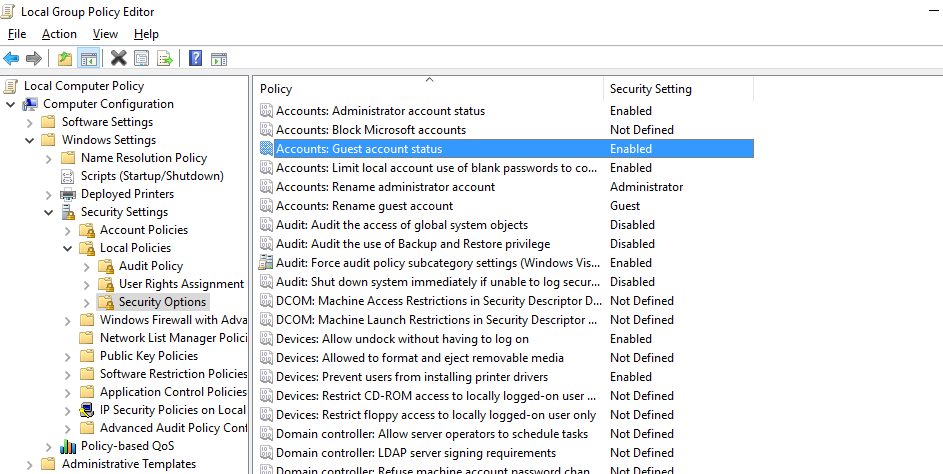
Open the Local Group Policy Editor console (gpedit.msc) and navigate Computer Configuration -> Windows Settings -> Security Settings -> Local Policies -> Security Options
- Accounts: Guest Account Status: Enabled
- Network access: Let Everyone permissions apply to anonymous users: Enabled
- Network access: Do not allow anonymous enumeration of SAM accounts and shares: Disabled
For security reasons, it is also a good idea to open the “Deny log on locally” policy under the Local Policies -> User Rights Assignment to ensure that the Guest account is specified in the policy settings.
Then make sure that Guest or Everyone is also specified in the Access this computer from network policy and the Deny access to this computer from the network policy should not have Guest as the value.
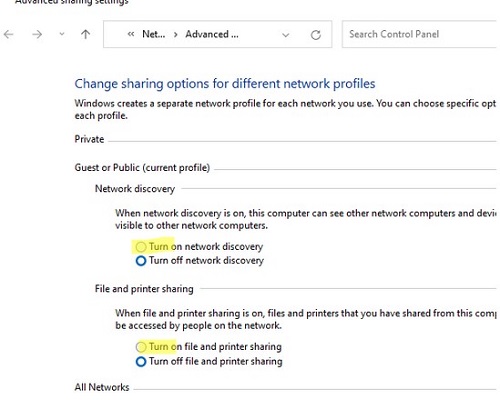
Also, make sure that network folder sharing is enabled under Settings -> Network & Internet -> Ethernet -> Change advanced sharing options. Check that Turn on file and printer sharing, Network Discovery (allows to show computers in the network environment) are enabled, and Turn off password protected sharing option is disabled in all network profile sections (Private, Public, All networks).
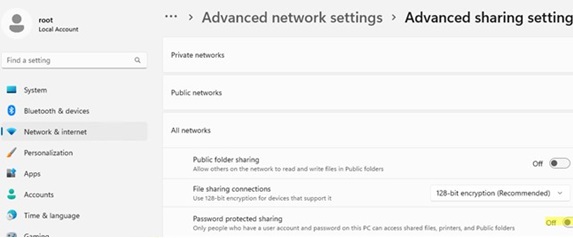
In Windows 11, you can find these options here: Settings -> Network and Internet -> Advanced network settings -> Advanced sharing settings.
Use the following command to update the local Group Policy settings on the computer:
gpupdate /force
Allow Guest Access to Shared Folders on Windows without Password
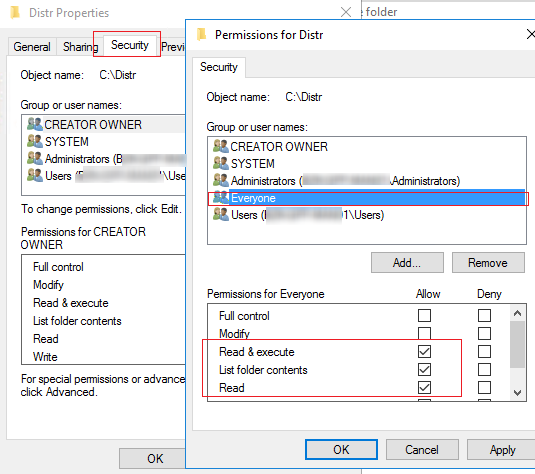
After you have configured the guest access policies, you must allow anonymous access to the target shared folder on the Windows host. You must change the security settings of the Windows share you want to allow anonymous access to. Open the folder properties, go to the Security tab, and check the current folder’s NTFS permissions. Assign Read permissions (and Modify if needed) to the Everyone local group. To do this, click Edit -> Add -> Everyone and select the NTFS access permissions for anonymous users. I have granted read-only permissions.
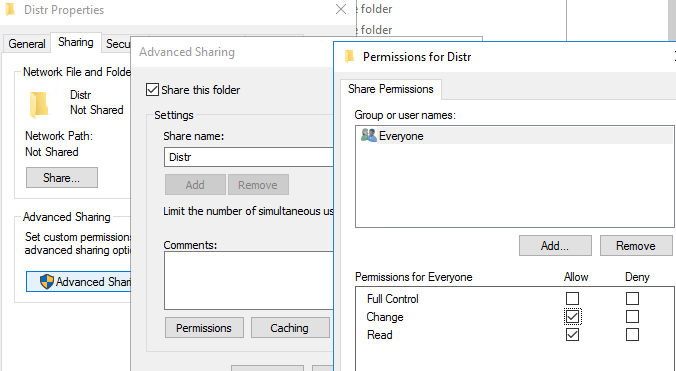
You must also grant anonymous users access to the network share on the Sharing tab (Sharing -> Advanced Sharing -> Permissions). Make sure that the Everyone group has the Modify and Read permissions. Make sure that the Everyone group has Change and Read permissions.
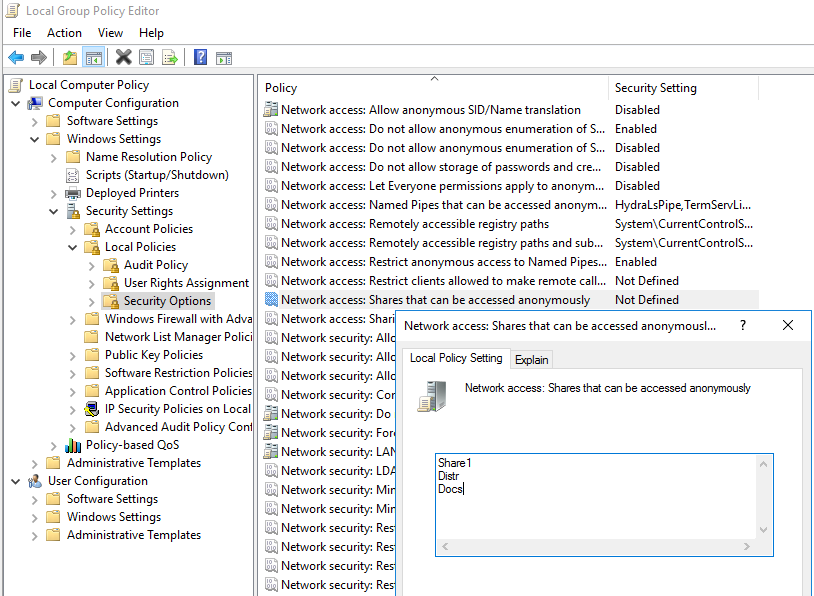
You must now specify the name of the network folder to which anonymous access is allowed in the local security policy. Open the Local Security Policy console (secpol.msc), and go to Local Policies -> Security Options. Then specify the name of the shared folder to which you want to allow anonymous access in the policy Network access: Shares that can be accessed anonymously (in my example, it is Share1, Distr, and Docs folders).
You can now anonymously connect to this computer remotely.
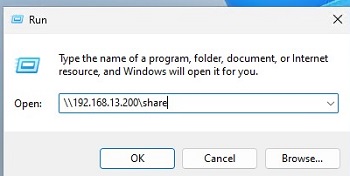
Press Win+R and type the UNC path to a shared folder you want to open (you can use the following formats: \\192.168.31.10\Docs or \\FS01\Docs).
If everything is configured correctly, you will see a list of files in a shared folder on a remote computer.
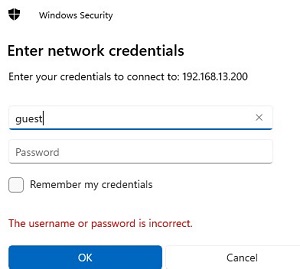
This method of granting anonymous access worked well until Windows 10 2004/Windows Server 2019. In current builds of Windows, you will still see a password prompt when you try to access a shared folder. In order to connect to a shared folder as an anonymous user, you need to specify the user name guest (you do not need to specify a password). But it’s not very convenient.
In this case, you will also need to enable the following Group Policy options:
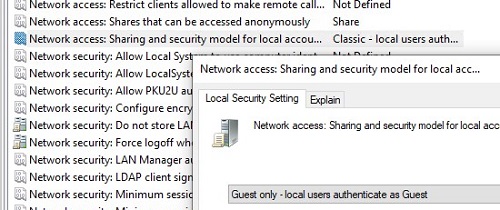
- Go to the following GPO section: Computer Configuration -> Windows Settings -> Security Settings -> Local Policies -> Security Options. Change the value of Network access: Sharing and security model for local accounts parameter from Classic to Guest Only. This policy enables the automatic use of the Guest account when you access a remote computer on the network using a local account (It is assumed that you are logged into Windows with a local account);
- Navigate to Computer Configuration -> Administrative Templates -> Network -> Lanman Workstation. Enable the policy Enable insecure guest logons. This policy allows network access to shared folders using the SMBv2 protocol under the Guest account. If you do not enable this parameter, an error will occur when you try to connect to the remote computer using the Guest account: “Y
ou can’t access this shared folder because your organization’s security policies block unauthenticated guest access” See this article.
Then specify that the Guest account should always be used to access shared resources on the specified computer. To do this, you need to add the computer name (or IP address) and the user name you want to use to connect to the remote computer to the Windows Credential Manager. Open the command prompt and run:
cmdkey /add:192.168.13.200 /user:guest
Windows will now automatically log in with the saved account (Guest in our case) when accessing the specified IP address (or hostname).
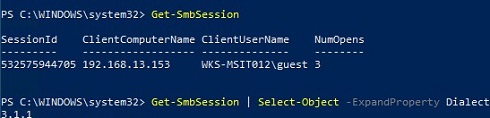
Now you can check on the remote computer that the client has connected to the shared folder under the Guest (anonymous) account:
Get-SmbSession
How to Enable Anonymous Access to Shared Printer on Windows
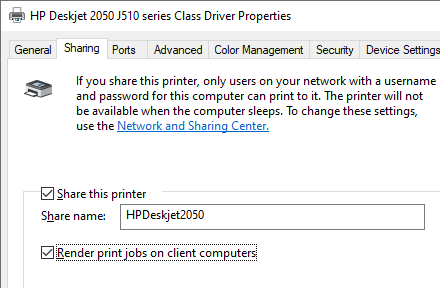
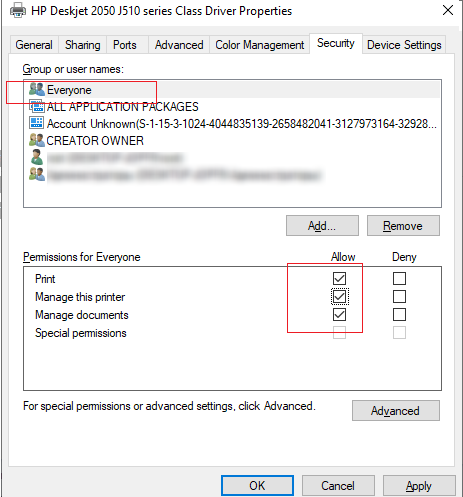
To enable anonymous access to a shared printer on your computer, open the shared printer properties in the Control Panel -> Hardware and Sound -> Devices and Printers. Enable the option Render print jobs on client computers on the Sharing tab.
Then select all Allow permissions for the Everyone group on the Security tab.
You can now connect anonymously to a shared folder (\\server-name\sharedfolder) and printer on a computer in a domain or workgroup without having to enter a username and password.
11 comments
It’s not because we can do something that it must be done.
Despite your warning, how many people will apply quickly – too quickly I would say – what is written in this article ?
Article totally useless, and moreover in the present days, very dangerous for security.
… and what will be the next article? How to do to pass all passwords in clear text ? How to do to avec all inbound rules open on a firewall ?
Be responsible
Thanks for your feedback!
Yes, you are right – anonymous access is an extremely dangerous thing from a security point of view.
In the article, I described a fairly secure way to provide anonymous access to a specific shared folder on Windows. In my case, this was the only solution available to access shared resource on a specific domain computer from a workgroup .
You can use the article for informational purposes, or check your policy settings to completely disable anonymous access in your network. 🙂
No need to be a prick. These changes are absolutely necessary in many circumstances, and the writeup is very clearly outlined and helpful to those who may need this ability.
Oliver (and other like you), what if I don’t care about corporate security? What if my windows machine is inside a local network behind a router i.e. totally inaccessible from the outside? What if I just want to print my stupid cartoon from another PC in the same network (and I don’t *really* care if somebody hijacks my printer)? What if I have not remembered any of my local users’ passwords for ages because of the stupid (but convenient) PIN sign-in thing? There are different users and use cases Oliver. You don create SECURITY by preaching about it without knowing the details.
BTW, damn Windows won’t let me print my cartoon without typing in the credentials even with all the instructions written in this post :/
People like Oliver are the worst. Without this article I couldn’t have setup my internal lab network to host deployable network images.
I don’t need staff member to have to authenticate to the share where the images are located, what’s the point, its internal with the no internet access. He probably supported the whole “Browser Choice” debacle ….
i have problem with this setting, if i want next folder with credential(local account) not work, no prompt for input user name and pass
A huge ‘Thank You’ !
This article has helped restore my sanity after being unable to ‘see’ other machines on my local Home network for purposes of simple folder sharing.
Having gone through the described steps I eventually struck gold by enabling ‘Function Discovery Resource Publication’ service which wasn’t running for some reason.
I had zero chance of figuring this out without your help, so thanks once again.
PS:
F*ck Olivier.
after 21h1 update – this not working. any idea?
I have had the same issues a while back and I read a few posts that stated win 10 home will allow you to change global sharing policies but ignores them. They are only applied in the pro versions. Something someone may be able to verify…………….
Yes, I’m most grateful for this page. The nanny state mentality that people must be protected from themselves is nonsense. People have to be responsible for their own personal actions, foolish or otherwise. We all make calculated risk decisions – even just crossing the road: but the smart ones evaluate the risk thoughtfully and decide for themselves what is and is not acceptable.
It took me a coupe of year to find this page, now I finally have access from Win 11 Pro to my passwordless network drive. A lot of thanks.