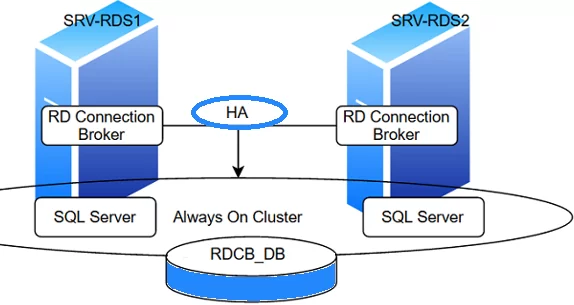
Remote Desktop Connection Broker (RDCB) is a component of the Remote Desktop Services (RDS) role in Windows Server. RD Connection Broker allows you to load-balance the RDS farm servers (when connecting to an RDS farm, the user is redirected to the least loaded RDS host), provides user access to VDI and RemoteApps, manages RDS host configuration in the farm. Also, RDCB allows users to reconnect to their sessions: when connecting to RDS, RDCB checks if there is any incomplete session on other servers of the farm and redirects them to their previous sessions.
In this article, we’ll show how to configure a fault-tolerant high availability RD Connection Broker instance maintaining its features in case one of the servers with the RDCB role fails. A database server running MS SQL Server 2019 will be used to store Remote Desktop Connection Broker data. To avoid a single point of failure, an RDCB SQL database should also be deployed in a fault-tolerant configuration. In this example, we will use two SQL Server nodes with the SQL Always On Availability Group configured.
RD Connection Broker High Availability requirements and supported configurations:
- At least 2 servers with the RD Connection Broker role running Windows Server 2022/2019;
- If you want to use high availability for an RDCB SQL database, you will need at least 2 hosts with SQL Server 2014 or newer (Standard or Enterprise edition). In this example, we have installed a standalone MS SQL Server 2019 Enterprise instance on each of the servers. If you are not going to have an HA SQL database, one server with SQL Express is enough;
- Install SQL Server Native Client on the servers with the RD Connection Broker role;
- Grant full control over your SQL database and SQL installation folder to RD Connection Broker servers;
- At least one server with the Remote Desktop Session Host role in the farm.
We will create a highly available RDCB configuration of two servers. Both of them will have the RD Connection role and SQL Server installed. High availability and disaster recovery of the SQL Server database will be provided by the SQL Server Always On Availability group.
Preparing Infrastructure for Remote Desktop Connection Broker
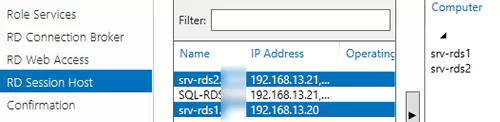
Assign static IP addresses to all servers with the RD Connection Broker role and join them to your Active Directory domain.
srv-rds1.woshub.com—192.168.13.20srv-rds2.woshub.com—192.168.13.21
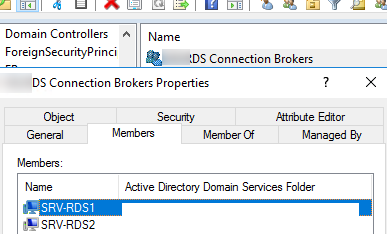
Create a new security group in Active Directory (MUN_RD_Connection_Brokers) and add all RDCB servers to it. You can create the group with the ADUC snap-in (dsa.msc) or by using PowerShell:
New-ADGroup "MUN_RD_Connection_Brokers" -path 'OU=Groups,OU=Berlin,DC=woshub,DC=com' -GroupScope Global -PassThru –Verbose
Add two RDS hosts to the group:
Add-AdGroupMember -Identity "MUN_RD_Connection_Brokers" -Members srv-rds1$,srv-rds2$
Create A records for the cluster name of your RDS farm (in our example, it is MUNRDCB) in DNS. DNS records must contain the IP addresses of all RDCB servers. It enables load balancing (Round Robin) between RD Connection Broker servers. I have created the following entries:
- A —
MUNRDCB.woshub.com 192.168.13.20(IP address of the first RDCB server — srv-rds1.woshub.com) - A —
MUNRDCB.woshub.com 192.168.13.21( IP address of the second RDCB server — srv-rds2.woshub.com)
You can create A records in DNS using PowerShell:
Add-DnsServerResourceRecordA -Name MUNRDCB -IPv4Address 192.168.13.20 -ZoneName woshub.com
Add-DnsServerResourceRecordA -Name MUNRDCB -IPv4Address 192.168.13.21 -ZoneName woshub.com
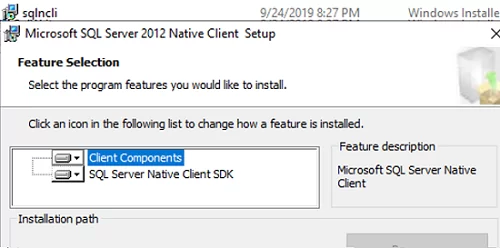
Install the SQL Server Native Client on all servers with the RDCB role. You can download the SQL Server Native Client for your SQL Server version from the Microsoft website or copy it from the SQL Server install image (D:\1033_ENU_LP\x64\Setup\x64\sqlncli.msi).
Then run SQL Server Management Studio and connect to your first SQL server, on which a shared Connection Broker database will be created (later we will move it to the Always On high availability group).
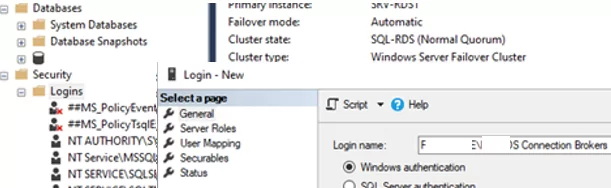
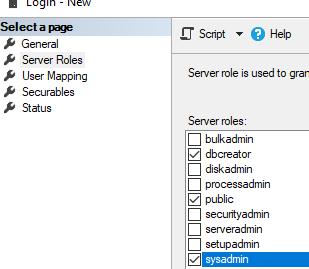
Open Security -> Logins to add a new login. Click Search, select your domain in Locations, set Object Types = Groups, and find the domain group MUN_RD_Connection_Brokers.
Assign dbcreator and sysadmin roles to the group.
Open SQL Server ports in Windows Defender Firewall (by default, TCP 1433 port is used to connect to Microsoft SQL Server).
Install Remote Desktop Services Roles on Windows Server
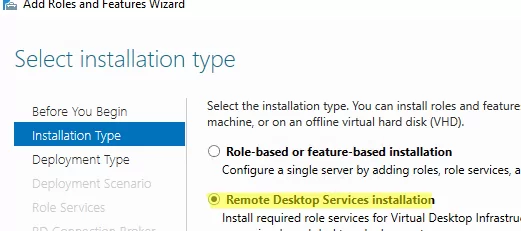
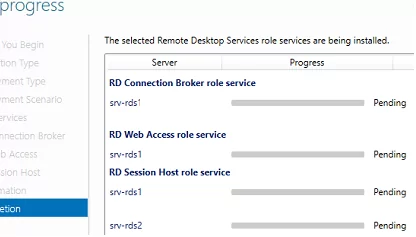
Then you have to install RDS roles on your servers. Open the Server Manager console, select Manage -> Add roles and Features -> Remote Desktop Services Installation.
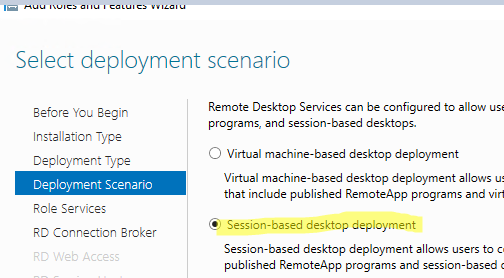
Select Standard deployment -> Session-based desktop deployment.
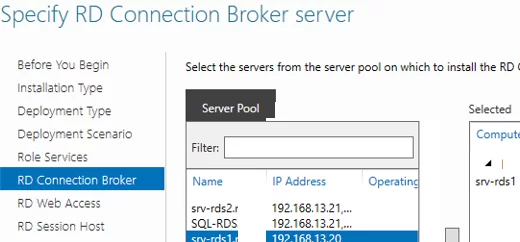
Choose one server you want to install the RD Connection Broker role on. You don’t need to install the RDCB role on the second server now.
Install the RD Web Access role on the same server. Install the RD Session Host role on both servers.
Wait for the installation of RDS roles to complete.
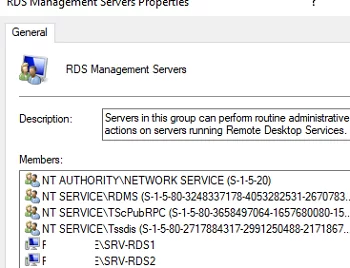
When you have finished installing the roles, add the RDCB hosts and ‘NT AUTHORITY\NETWORK SERVICE’ accounts to the local RDS Management Servers group on both servers.
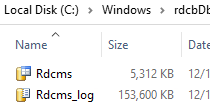
During the installation of the RD Connection Broker role on the first server in the farm, a local SQL database will be created in C:\Windows\rdcbDb\rdcms.mdf on the local drive of the RD Connection Broker server.
This database keeps the information about the farm and terminal user sessions. Since it is located on the local computer, other RDCB servers will not be able to use it. To provide RDCB HA, you have to move it to a dedicated SQL server where other servers can access it.
Deploying RD Connection Broker High Availability
Before you add a second host with the RD Connection Broker role to the farm, you must migrate the local RDCB database to an external SQL Server.
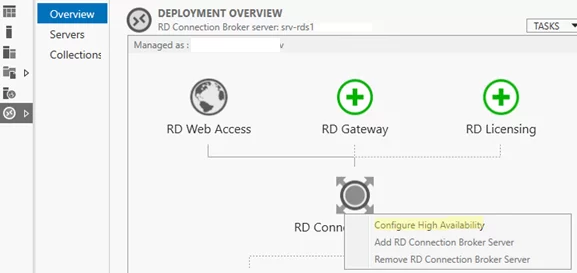
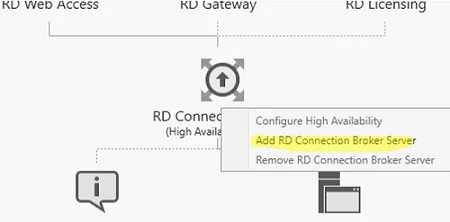
To move the Connection Broker database from the local database to the dedicated SQL Server, open Server Manager -> Remote Desktop Services -> Overview. To run the Remote Desktop Connection Broker Failover Configuration Wizard, click the RD Connection Broker role image and select Configure High Availability.
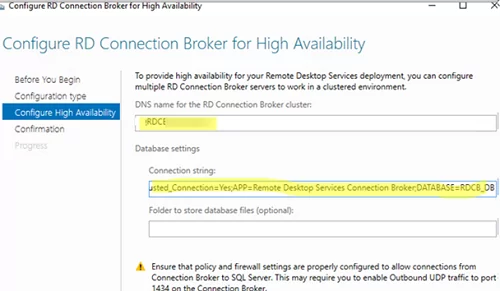
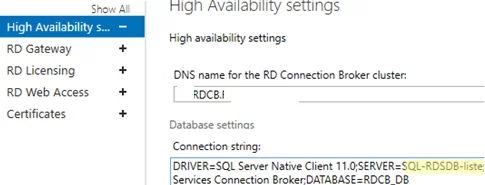
Then select Dedicated Database Server. Specify SQL Server connection settings the local RDCB database will be moved.
Fill in two fields:
- DNS name for the RD Connection Broker Cluster: an FQDN name of your RDCB farm we have created Round Robin DNS records for (in our example, it is
MUNRDCB.woshub.com). This is the address that RDP clients will use when connecting to RD Connection Broker servers; - Database Connection String – specify the connection string to the SQL Server database. Here is the string format:
DRIVER=SQL Server Native Client 11.0;SERVER=<SQL Server Name>;Trusted_Connection=Yes;APP=Remote Desktop Services Connection Broker;DATABASE=<DB Name>In this example, SQL Server Name is the name of the SQL server you want to create a database on, and DB Name is the name of your new database:DRIVER=SQL Server Native Client 11.0;SERVER=srv-rds2.woshub.com;Trusted_Connection=Yes;APP=Remote Desktop Services Connection Broker;DATABASE=RDCB_DB
Click Configure in the next step.
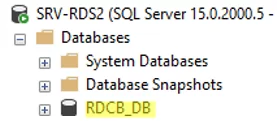
Then connect to your SQL Server instance using SQL Management Studio and make sure that the new database RDCB_DB has been created.
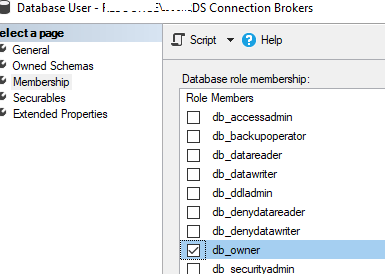
Grant both RD Connection Broker servers write permissions to the database. Open Database -> RDCB_DB -> Security -> Users -> New user.
Create two new users: BUILTIN\RDS Management Servers and woshub\MUN_RD_Connection_Brokers. Grant both db_owner and public privileges.
To provide high availability in case the first server fails, add a second RD Connection Broker server to the current configuration.
Click the RD Connection Broker icon and select Add RD Connection Broker Server.
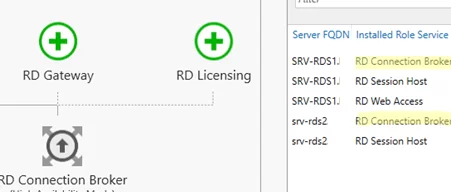
Enter the name of the second server you want to install the Connection Broker role on and click Next. Then two servers with the RDCB role will appear in the list of RDS farm hosts. You will also see the RD Connection Broker (High Available Mode) message.
This completes the High Availability configuration of the Remote Desktop Connection Broker.
Configuring SQL Server Failover Configuration for RD Connection Broker HA
Then set up a failover configuration of your SQL database. Meanwhile, it is running on one server only. Place your RD Connection Broker database in the SQL cluster. It may be either a classic Microsoft Failover Cluster or an SQL Server Always On high availability group.
Basic Always On configuration in SQL Server 2019 is described in this article. We will show only the main steps here:
- Install the Failover Clustering role and build an SQL-RDS cluster of two RDCB hosts with a witness and quorum on any file server (it is described in the article on Always On mentioned above);
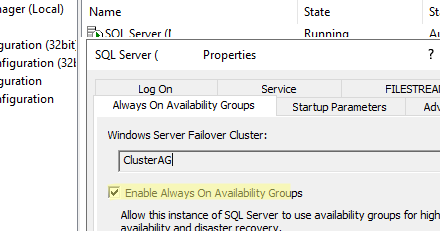
- Enable the option Enable Always On Availability Groups in the SQL Server Configuration Manager settings on both servers;
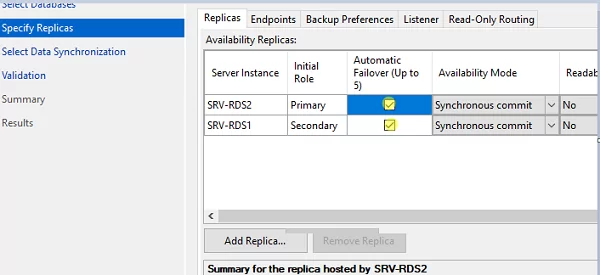
- Run the New Availability Group Wizard;
- Enter the name of the Availability Group (SQL-RDS);
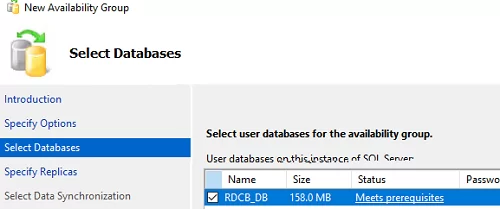
- Select a database you want to place in your high availability group (RDCB_DB);
- Add the second SQL server to the high availability group and check the Automatic Failover option;
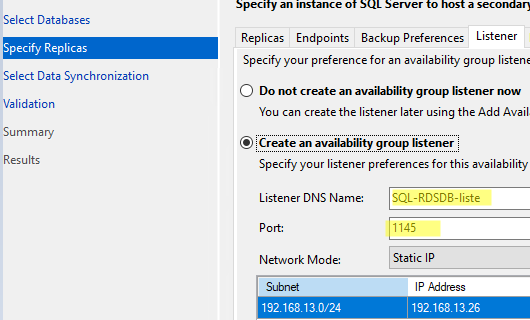
- On the Listener tab, enter the name and IP address that clients will use to connect to the database in your Always On group (SQL-RDSDB-liste);
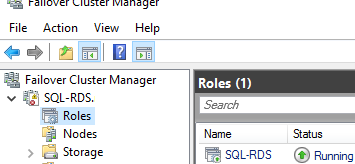
- Open the Failover Cluster Manager snap-in (
FailoverClusters.SnapInHelper.msc) and make sure that the new resource has appeared in the list of roles.
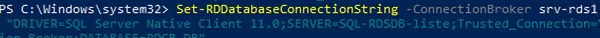
Then change the connection string for the SQL server with the RDCB database in the Connection Broker settings. You can only change the RDCB connection string via PowerShell:
Set-RDDatabaseConnectionString [-DatabaseConnectionString] <String> [[-ConnectionBroker] <String>] [ <CommonParameters>]
In my example, the command to switch the RDCB farm to the SQL database High Availability group looks like this:
Set-RDDatabaseConnectionString -ConnectionBroker srv-rds1.woshub.com -DatabaseConnectionString "DRIVER=SQL Server Native Client 11.0;SERVER=SQL-RDSDB-liste;Trusted_Connection=Yes;APP=Remote Desktop Services Connection Broker;DATABASE=RDCB_DB"
If the command returns no error, then everything is OK. Now your RDS Connection Broker cluster is configured to use SQL Always On availability group.
Open your RDS farm settings and make sure that a new connection string is used for HA (Tasks -> Edit Deployment Properties).
So, we have created a high-availability RDS Connection Broker service on Windows Server 2022/2019. You can test RDCB’s high availability by shutting down one of the hosts in the RDS farm.
Then you can go on with the configuration of your RDS farm, deploy an RDS licensing server, add RDSH servers, set up RDS collections, publish RemoteApps, enable HTML5 web client for RDS, etc.