There are several ways to prevent certain Group Policy Object (GPO) settings from being applied to specific users and/or computers in Active Directory:
- Use GPO security filtering to control which AD objects can apply the policy (the easiest and most convenient option)
- Filtering the scope of the GPO using WMI filters
- Item-Level Targeting exceptions in Group Policy. This only applies to GPO settings configured through Group Policy Preferences.
Let’s consider a scenario where you need to prevent a Group Policy that configures Windows Update settings from applying to a specific computer. In this example, all computers are located in an OU called Workstations, to which the gpo_WSUS_workstations GPO has been assigned.
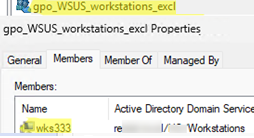
First, create a separate security group in AD (gpo_WSUS_workstations_excl) and add the computers or user accounts that you want to exclude from the Group Policy Object scope.
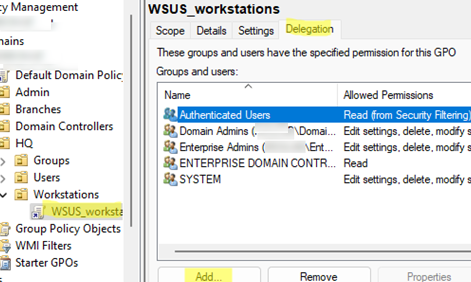
- Open the domain Group Policy management console (
gpmc.msc) - Select the required GPO, go to the Delegation tab, and click the Add button.
- By default, the GPO applies to all AD objects (Authenticated Users group)
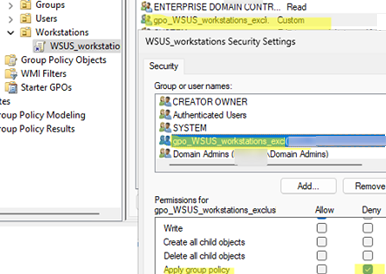
- Enter the name of the group, user, or computer that you want to exclude from the Group Policy
- Click the Advanced button and set the Deny for Apply Group Policy permission
- This will prevent these Group Policy settings from being applied to any of the AD objects in the specified group. Deny permissions take precedence over allow permissions. Therefore, even though the Authenticated Users group is allowed to apply the policy, the Deny permission takes higher priority.
Update the GPO settings on the client (preferably reboot the computer to refresh AD group membership). Next, open a command prompt and generate a report of the applied GPOs by running the following command:
gpresult /r
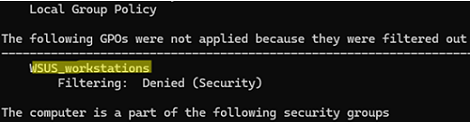
This report shows that the WSUS policy was not applied to this computer because security settings are preventing it:
The following GPOs were not applied because they were filtered out WSUS_workstations Filtering: Denied (Security)
To add another computer to the exclusions of this GPO, simply add its account to the gpo_WSUS_workstations_excl group and reboot the computer.
The downside of this method for creating exceptions for the GPO is that the administrator must manually add or remove users/computers from the group that needs to be excluded from the policy. If you want users or computers to be automatically added/removed from the policy scope based on some dynamic attributes, you can use the AD dynamic groups concept or the WMI GPO filters.
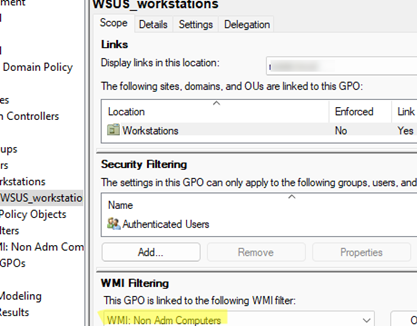
The idea behind a WMI filter is to create a WQL query to define which objects the policy applies to. For example, you might want the policy to exclude computers with the keyword ‘adm‘ in their hostname. This can be achieved by using the following WMI query:
SELECT * FROM Win32_ComputerSystem WHERE NOT (Name LIKE '%adm%')
Create this WMI filter in the GPMC console and link it to the GPO.
Now, each computer will check the WMI query at startup, and if it doesn’t match, the policy will not be applied.
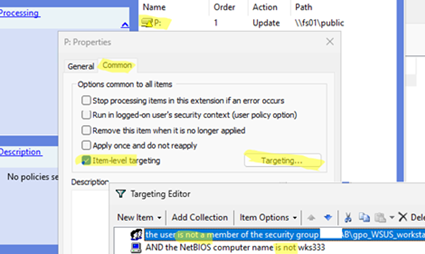
There is another way to create exceptions for specific users and computers in the GPO. If you are using GPO settings that are located in the Group Policy Preferences (GPP) section, you can make policy exceptions using Item-Level Targeting.
In the settings of any GPP item on the Common tab, you need to enable Item-level Targeting and configure IS-NOT rules to define exceptions for applying this GPO parameter. In this example, we have configured GPP exceptions for a specific AD group and computer.