The password policy in an Active Directory domain specifies basic security requirements for user account passwords, such as password complexity, length, frequency of password changes, and so on. A strong AD password policy will reduce the possibility of attacks on a user’s password, such as brute force, sniffing, or stealing.
Configuring Password Settings in the Default Domain Policy
The user password policy settings in the AD domain are set by the Default Domain Policy GPO. You can view and change the password policy settings in your domain using the Group Policy Manage Management console.
- Open the
gpmc.mscconsole and select the Default Domain Policy that is linked to the root of the domain;; - Right-click this GPO and select Edit;
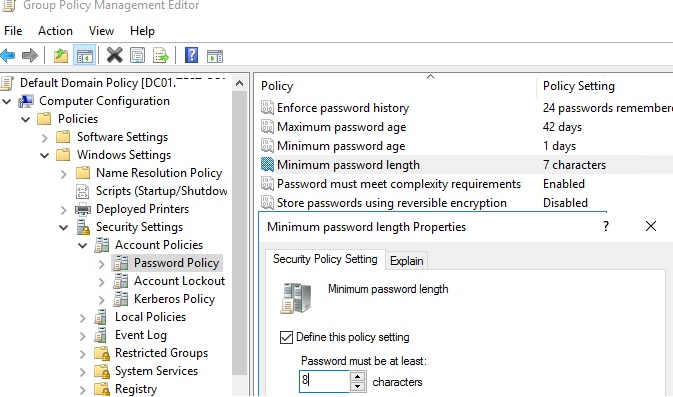
- Expand Computer configuration -> Policies -> Windows Settings -> Security Settings -> Account Policies -> Password Policy;
- There are six password policy settings in this section (described below);
- To change the password parameter settings, double-click it. To enable the policy, select the Define this policy settings checkbox and specify the required setting. In the example shown in the screenshot, I have set the minimum length of the user’s password to 8 characters. Save the changes;
- New password policy settings apply to all domain users after updating GPO settings on a domain controller with the PDC Emulator FSMO role;
Password Policy Settings in an Active Directory Domain
There are six Windows password policy settings that you can configure with the GPO:
- Enforce password history – set the number of old passwords stored in AD. Users cannot reuse old passwords. However, the account can be manually reset to the old password by a domain administrator or a user delegated to reset passwords in AD;
- Maximum password age – sets the password expiration in days. When a password expires, Windows prompts the user to change it. It makes sure that users change their password regularly;
- Minimum password length – it is recommended that passwords contain at least 8 characters (if you specify 0 here, the password is not required);
- Minimum password age – sets how often users can change their passwords. This option prevents the user from changing the password several times in a row and then reverting to the old password by overwriting the AD Password History. As a general rule, it is worth leaving this setting for 1 day so that the user can change the password on their own if it is compromised;
- Password must meet complexity requirements – if this option is enabled, a user cannot use their account name in a password (no more than 2 characters of a
usernameorFirstnamein a row). The password must also contain 3 types of characters from the following list: numbers (0–9), uppercase letters, lowercase letters, and special characters ($, #, %, etc.).To prevent users from using weak passwords (from popular password dictionaries), it is recommended that you regularly audit user passwords in the AD domain. - Store passwords using reversible encryption – user passwords are stored encrypted in the AD database, but sometimes you need to grant some apps to access the password. If this policy setting is enabled, passwords are less protected (almost plain text), which is not secure (an attacker can get access to the password database if the DC is compromised). If you enable this option, you must additionally protect the passwords of privileged users at remote sites by implementing Read-Only Domain Controllers (RODCs).
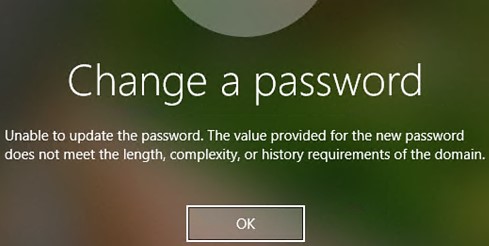
If a user attempts to change a password that does not match the password policy in the domain, the error message is displayed:
Unable to update the password. The value provided for the new password does not meet the length, complexity, or history requirements of the domain.
The default settings for the Active Directory domain password policy are listed in the table below:
| Policy | Default value |
| Enforce password history | 24 passwords |
| Maximum password age | 42 days |
| Minimum password age | 1 day |
| Minimum password length | 7 |
| Password must meet complexity requirements | Enabled |
| Store passwords using reversible encryption | Disabled |
| Account lockout duration | Not set |
| Account lockout threshold | 0 |
| Reset account lockout counter after | Not set |
Typically, in addition to a password policy, you need to configure settings to lock user accounts if they enter an incorrect password. These settings can be found under the Account Lockout Password GPO section:
- Account Lockout Threshold – the number of failed sign-in attempts (with an incorrect password) before the user’s account is locked;
- Account Lockout Duration – the duration of the account lock, during which the user will not be able to log into the domain;
- Reset account lockout counter after – the number of minutes after which the Account Lockout Threshold counter will be reset.
Managing AD Password Policy with PowerShell
You can use PowerShell cmdlets from the Active Directory module to view settings and change the settings of the default password policy in AD.
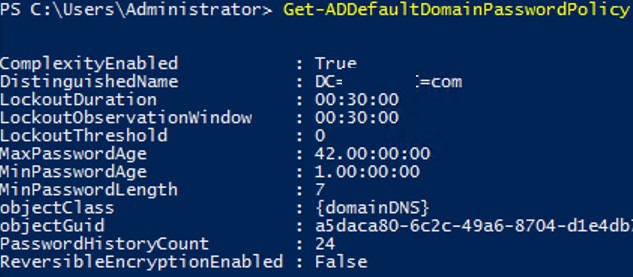
List the default password policy settings for the current domain:
Get-ADDefaultDomainPasswordPolicy
ComplexityEnabled: True
DistinguishedName: DC=woshub,DC=com
LockoutDuration: 00:20:00
LockoutObservationWindow: 00:30:00
LockoutThreshold: 0
MaxPasswordAge: 60.00:00:00
MinPasswordAge: 1.00:00:00
MinPasswordLength: 8
objectClas : {domainDNS}
PasswordHistoryCount: 24
ReversibleEncryptionEnabled: FalseOr with the command:
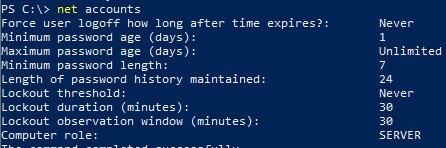
net accounts
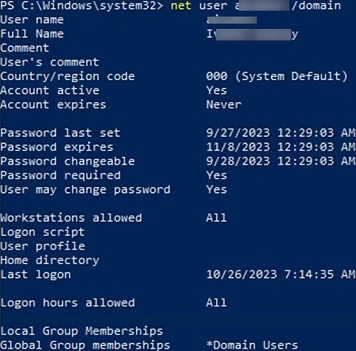
View information about when the user last changed their password and when their password expires:
net user s.wolf /domain
You can change the settings of the default AD password policy with the command:
Set-ADDefaultDomainPasswordPolicy -Identity woshub.com -MinPasswordLength 10 -LockoutThreshold 3.
How to Enable Multiple Password Policies for Active Directory Users
When you use AD Group Policies, you can only assign a single policy to a domain, and this policy will be applied to all users with no exceptions. Even if you create a custom GPO with different password settings and apply it to an OU, those settings won’t be applied to users.
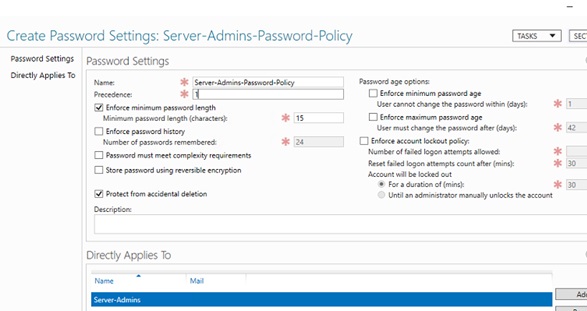
Starting with Active Directory in Windows Server 2008, you can use Fine-Grained Password Policies (FGPP) to create multiple customized password policy settings for different users and groups. For example, you may want to require users in the Server Admins group to use passwords that are at least 15 characters in length.
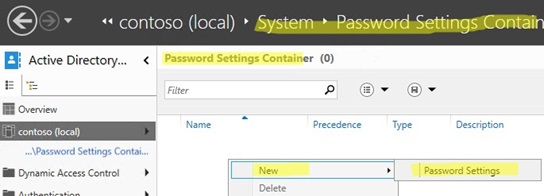
- Open the Active Directory Administrative Center console (
dsac.exe); - Navigate to System -> Password Settings Container and create a new PSO (Password Settings Object);
- Specify the name of the password policy and its priority. Enable and configure the password settings you want to apply. Add groups or users to which you want to apply specific password policy settings in the ‘Directly Applies To‘ section.
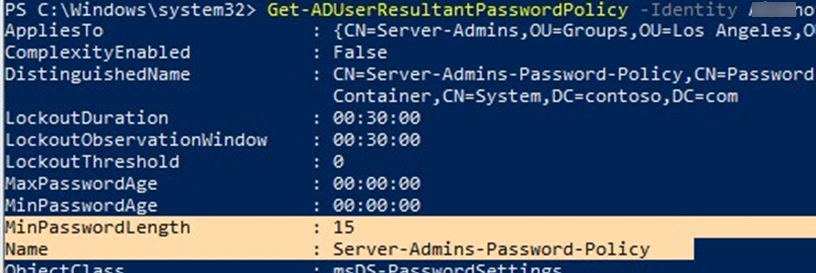
To check whether a custom password policy applies to a particular user, run the command:
Get-ADUserResultantPasswordPolicy -Identity s.wolf
The command displays the resulting password policy settings for the specified user account.
4 comments
NOT – Computer configuration-> Windows Settings->Security Settings -> Account Policies -> Password Policy;
BUT – Computer configuration-> Policies-> Windows Settings->Security Settings -> Account Policies -> Password Policy;
You are right, here I need to specify the path in the domain, and not in the local GPO.
Affordable way to get way more options and flexibility is ActivePasswords. Target security groups or OU’s, fine-tune (multiple) password requirements in detail and get logging. Controlled through group policy. Small and easy to setup.
default password policy not only applies to User objects, it also applies to Local accounts on domain joined machines.