If your company has several system administrators, sometimes you may want to know who rebooted the server. In this article. I will show you how to identify a user who restarted or shutdown a computer/server running Windows by the event logs.
Information about the user account that sent the restart command is stored in Windows Event Log.
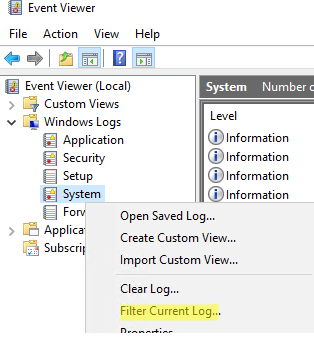
- Open the Event Viewer console (
eventvwr.msc) and go to Windows Logs -> System; - Use the Event Log filter by clicking Filter Current Log in the context menu;
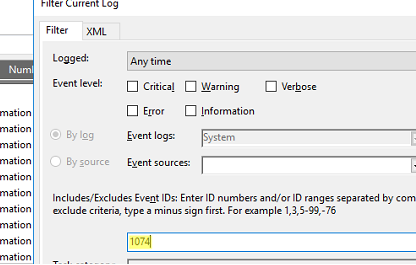
- In the filter box, enter the EventID 1074 and click OK;
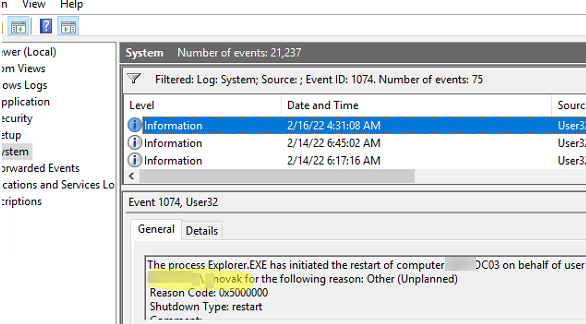
- Only shutdown (reboot) events will be left in the log list. Open the last event;
- The event with User32 as a source shows a user who initiated a Windows restart. In this example, it is user
novak;
The process C:\Windows\Explorer.EXE has initiated the restart of computer MUN-DC03 on behalf of user WOSHUB\novak for the following reason: Other (Unplanned) Reason Code: 0x5000000 Shutdown Type: restart Comment:
Let’s look at more examples of Windows restart/shutdown events. You may see NT AUTHORITY\SYSTEM as a user who restarted an operating system.
This means that the restart was initiated by a Windows service or program run as a SYSTEM. For example, it may be a wuauserv service process that completed updating Windows and restarted a computer according to the configured Windows Update GPO settings or using a task of the PSWindowsUpdate module.
The process C:\Windows\uus\AMD64\MoUsoCoreWorker.exe has initiated the restart of computer MUN-DC03 on behalf of user NT AUTHORITY\SYSTEM for the following reason: Operating System: Service pack (Planned) Reason Code: 0x80020010 Shutdown Type: restart Comment:
If your Windows guest is running in a VMware virtual machine and you run Restart Guest in the VMware management console, the shutdown event looks as follows:
The process C:\Program Files\VMware\VMware Tools\vmtoolsd.exe has initiated the shutdown of computer MUN-DC03 on behalf of user NT AUTHORITY\SYSTEM for the following reason: Legacy API shutdown Reason Code: 0x80070000 Shutdown Type: shutdown
In this case, Windows shutdown is also initiated by NT AUTHORITY\SYSTEM, since VMware Tools integration services are run on behalf of the System.
You can get information about restart events using PowerShell. The following command displays all events with the EventID 1074:
Get-WinEvent -FilterHashtable @{logname=’System’;id=1074}|ft TimeCreated,Id,Message
The command returned the descriptions of all Windows restart and shutdown events.
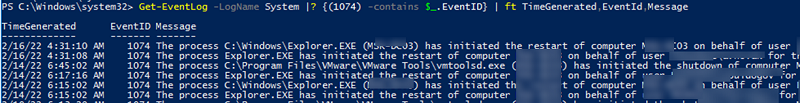
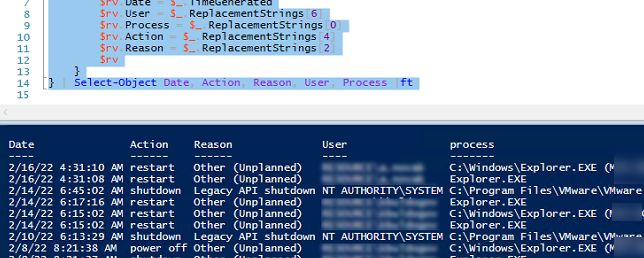
You can use the following PowerShell script that returns a list of the last ten events with the names of users or processes initiated server restart/shutdown.
Get-EventLog -LogName System |
where {$_.EventId -eq 1074} |select-object -first 10 |
ForEach-Object {
$rv = New-Object PSObject | Select-Object Date, User, Action, process, Reason, ReasonCode
if ($_.ReplacementStrings[4]) {
$rv.Date = $_.TimeGenerated
$rv.User = $_.ReplacementStrings[6]
$rv.Process = $_.ReplacementStrings[0]
$rv.Action = $_.ReplacementStrings[4]
$rv.Reason = $_.ReplacementStrings[2]
$rv
}
} | Select-Object Date, Action, Reason, User, Process |ft
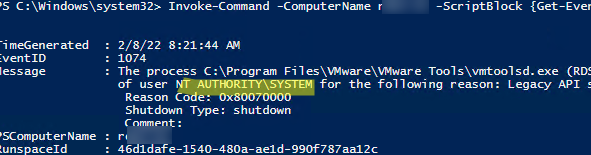
You can use PowerShell to get the name of the user who restarted a remote computer. You can access the Event Log on a remote host using Get-EventLog -ComputerName command or connect to the computer using the Invoke-Command cmdlet and PSRemoting:
Invoke-Command -ComputerName mun-dc03 -ScriptBlock {Get-WinEvent -FilterHashtable @{logname=’System’;id=1074} |select-object TimeCreated,Id,Message -first 1}
By the Event ID 1074, you can find only the reasons for correct server reboots. If Windows was restarted due to an emergency situation (for example, if a power failure or a BSOD appears), you have to search for an EventID 6008.
The previous system shutdown at 3:24:29 AM on 9/17/2022 was unexpected.
Of course, you won’t be able to find out who restarted Windows if the event logs have been cleared or if more recent events have been overwritten by earlier ones (it is recommended to increase the max size of event logs using GPO in the domain).