Many administrators usually use the netstat console tool or graphic TCPView to display information about active TCP/IP connections and open TCP ports in Windows. Instead of netstat, you can use the Get-NetTCPConnection cmdlet in PowerShell to get information about active network connections in Windows, open TCP ports, and run processes that are using the TCP/IP protocol. PowerShell makes it easy to write complex scripts to get information and monitor open TCP ports, processes, and established network connections.
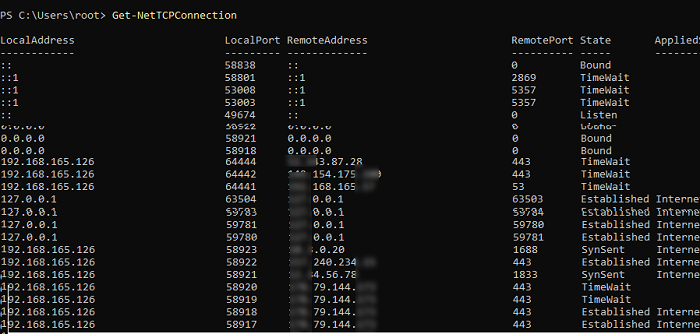
Try to run the Get-NetTCPConnection command without any options.
Like netstat, the command has displayed the list of all active connections with local and remote IP addresses, ports, connection state (Listen, Established Internet, TimeWait, Bound, CloseWait, SynReceived, SynSent), and process ID (PID) that is using this TCP connection.
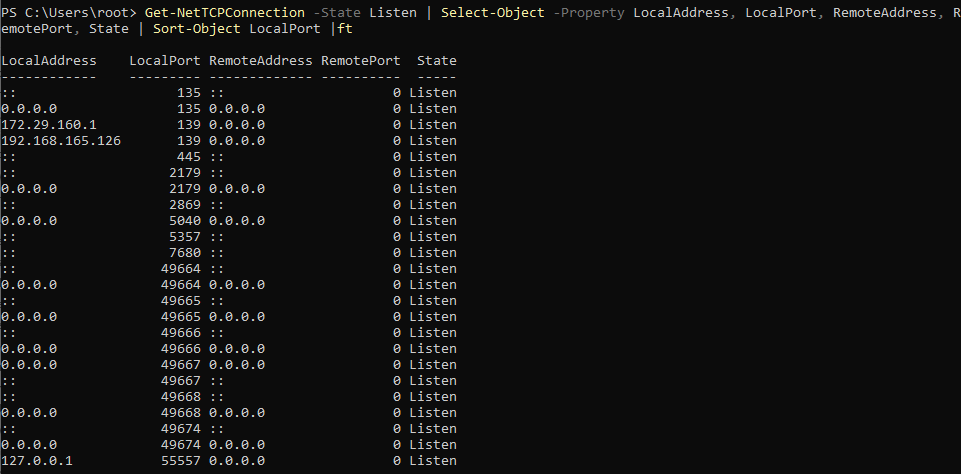
You can display a list of open (listening) ports on your local computer:
Get-NetTCPConnection -State Listen | Select-Object -Property LocalAddress, LocalPort, RemoteAddress, RemotePort, State | Sort-Object LocalPort |ft
Get-NetUDPEndpoint cmdlet is used to get information about UDP ports.You can display external (Internet) connections only:
Get-NetTCPConnection -AppliedSetting Internet
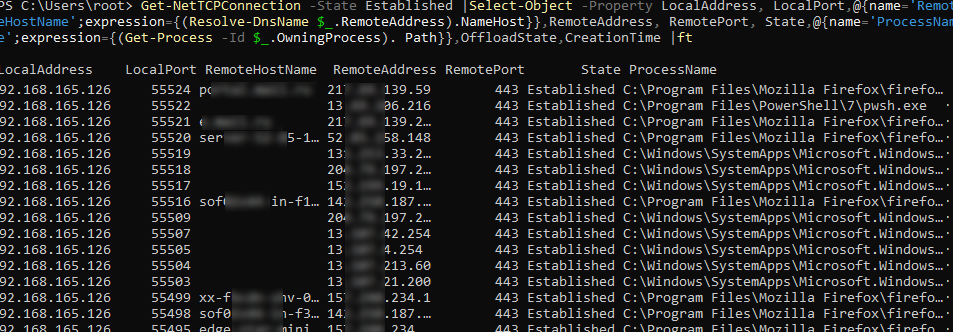
You can display DNS names of remote hosts and process names for TCP connections:
Get-NetTCPConnection -State Established |Select-Object -Property LocalAddress, LocalPort,@{name='RemoteHostName';expression={(Resolve-DnsName $_.RemoteAddress).NameHost}},RemoteAddress, RemotePort, State,@{name='ProcessName';expression={(Get-Process -Id $_.OwningProcess). Path}},OffloadState,CreationTime |ft
This PowerShell script resolved all host IP addresses to DNS names and specified process names for all connections.
By the name of a parent process PID, you can display the list of related Windows services that are using the network:
Get-WmiObject Win32_Service | Where-Object -Property ProcessId -In (Get-NetTCPConnection).OwningProcess | Where-Object -Property State -eq Running | Format-Table ProcessId, Name, Caption, StartMode, State, Status, PathName
You can view only network connections initiated by the specific process. To do it, you can use the following PowerShell script:
$TrackProcessName = "*chrome*"
$EstablishedConnections = Get-NetTCPConnection -State Established |Select-Object -Property LocalAddress, LocalPort,@{name='RemoteHostName';expression={(Resolve-DnsName $_.RemoteAddress).NameHost}},RemoteAddress, RemotePort, State,@{name='ProcessName';expression={(Get-Process -Id $_.OwningProcess). Path}}, OffloadState,CreationTime
Foreach ($Connection in $EstablishedConnections)
{
If ($Connection.ProcessName -like $TrackProcessName)
{
$Connection|ft
}
}
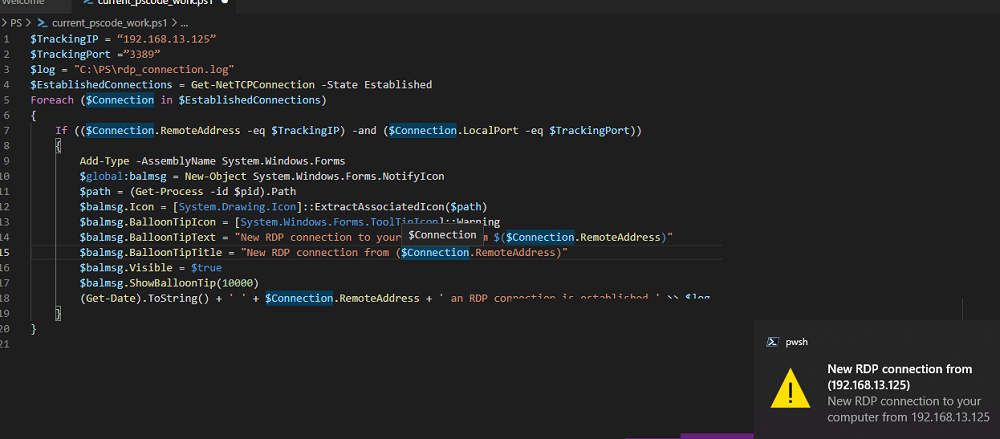
You can use the Get-NetTCPConnection cmdlet in various scenarios. For example, you can create a simple PowerShell script to track if the connection is established from the specific IP address to the specified local port and display a pop-up notification to the administrator.
In the following example, a PowerShell script checks if a connection from the specified IP address appears on the default RDP port 3389. If the connection appears, the script will display a pop-up notification and log the date and time of the connection to a text file:
$SourceIP = “192.168.13.125”
$TargetPort =”3389”
$log = "C:\PS\rdp_connection_log.txt"
$EstablishedConnections = Get-NetTCPConnection -State Established
Foreach ($Connection in $EstablishedConnections)
{
If (($Connection.RemoteAddress -eq $SourceIP) -and ($Connection.LocalPort -eq $TargetPort))
{
Add-Type -AssemblyName System.Windows.Forms
$global:balmsg = New-Object System.Windows.Forms.NotifyIcon
$path = (Get-Process -id $pid).Path
$balmsg.Icon = [System.Drawing.Icon]::ExtractAssociatedIcon($path)
$balmsg.BalloonTipIcon = [System.Windows.Forms.ToolTipIcon]::Warning
$balmsg.BalloonTipText = "New RDP connection to your computer from $($Connection.RemoteAddress)"
$balmsg.BalloonTipTitle = "New RDP connection from ($Connection.RemoteAddress)"
$balmsg.Visible = $true
$balmsg.ShowBalloonTip(10000)
(Get-Date).ToString() + ' ' + $Connection.RemoteAddress + ' an RDP connection is established ' >> $log
}
}
In the same way, you can monitor and log network connections over any other protocol, like SSH, SMB, FTP, SMTP, etc. This PowerShell script may be converted into a Windows service that will start automatically.
You can get a list of open TCP ports and connections on remote computers using PowerShell remoting cmdlets (Enter-PSSession and Invoke-Command).
Invoke-Command -ComputerName be-dc01 {Get-NetTCPConnection -State Established}
The Get-NetTCPConnection cmdlet (as well as Test-NetConnection) may be very useful for tracking and diagnosing network connections in Windows.
2 comments
Thanks for the article. Very useful.
One suggestion.
Insted of:
Foreach ($Connection in $EstablishedConnections)
{
If ($Connection.ProcessName -like $TrackProcessName)
{
$Connection|ft
}
}
Use:
$EstablishedConnections | Where-Object ProcessName -Like $TrackProcessName | Select-Object * | Format-Table
the command Get-NetTCPConnection show wrong IP addresses for some connections, eg in my case it shows:
0.0.0.0 49425 0.0.0.0 0 Bound – local address and remote address as 0.0.0.0 for port 49425 when command ‘netstat -ano’ and ‘resource monitor’ app shows 192.168.68.114 as local address and 40.113.103.199 as remote address:
TCP 192.168.68.114:49425 40.113.103.199:443 ESTABLISHED 6096