Windows LAPS (Local Administrator Password Solution) allows you to centrally manage the passwords for the local administrators on the computers in your AD domain. The current local administrator password is stored in the protected attributes of computer objects in Active Directory, is automatically changed regularly, and can be viewed by authorized users.
In this guide, we’ll show you how to configure and use Windows LAPS to manage the local administrator password on computers joined to an AD domain.
Until April 2023, you should manually download the LAPS MSI installation file, deploy the administrator or client components to computers, install ADMX GPO templates for LAPS, and extend the AD schema
Updates adding native support for the new version of LAPS in Windows were released in April 2023. You no longer need to manually download and install the MSI package to use LAPS.
New Built-in Windows LAPS Overview
The following cumulative updates in April 2023 added native support for Windows LAPS:
- Windows 11 22H2 – KB5025239
- Windows 11 21H2 – KB5025224
- Windows 10 22H2 — KB5025221
- Windows Server 2022 – KB5025230
- Windows Server 2019 – KB5025229
What’s new in Windows LAPS?
- All the components of the new LAPS are part of Windows;
- Allows storing administrator passwords in on-premises Active Directory or in Azure AD;
- DSRM (Directory Services Restore Mode) password management on AD domain controllers;
- Support for password encryption;
- Password history;
- Allow the local administrator password to be automatically changed after it has been used to log on to the computer locally.
As we mentioned above, you no longer need to manually download and install the LAPS client or Group Policy client-side extension (CSE). All the necessary LAPS components are available in Windows after you install the April updates.
The following Windows LAPS management tools are available:
- New ADMX group policy file;
- A separate LAPS tab in computer properties in Active Directory Users and Computers (ADUC) console;
- Windows LAPS PowerShell module;
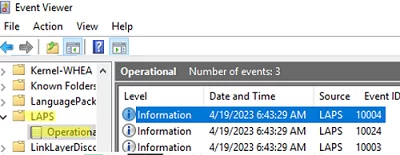
- Separate log in the Event Viewer: Application and Service Logs -> Microsoft -> Windows -> LAPS -> Operational.
Microsoft notes that you must disable the Group Policies and remove the settings from the previous version of LAPS (legacy MSI) before deploying the new LAPS GPO. To do this, stop new installations of legacy LAPS and remove all settings in the following registry key HKLM\Software\Microsoft\Windows\CurrentVersion\LAPS\State.
Events with the following Event IDs will appear in the Event Viewer if the legacy version of LAPS is not removed:
- Event ID 10033, LAPS — The machine is configured with legacy LAPS policy settings, but legacy LAPS product appears to be installed. The configured account’s password will not be managed by Windows until the legacy product is uninstalled. Alternatively, you may consider configuring the newer LAPS policy settings.
- Event 10031, LAPS — LAPS blocked an external request that tried to modify the password of the current manager account.
Deploying Local Administrator Password Solution in Active Directory Domain
You can start deploying the new version of LAPS after you have installed the new updates on all domain controllers.
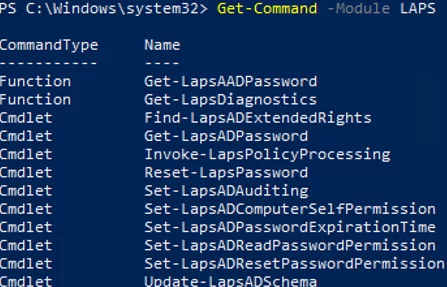
To manage the Local Administrator Password Solution, use the PowerShell cmdlets from the LAPS module. You can use the following commands:
Get-Command -Module LAPS
- Get-LapsAADPassword
- Get-LapsDiagnostics
- Find-LapsADExtendedRights
- Get-LapsADPassword
- Invoke-LapsPolicyProcessing
- Reset-LapsPassword
- Set-LapsADAuditing
- Set-LapsADComputerSelfPermission
- Set-LapsADPasswordExpirationTime
- Set-LapsADReadPasswordPermission
- Set-LapsADResetPasswordPermission
- Update-LapsADSchema
After installing updates on DCs and clients, you must perform an AD schema update. This will add new attributes. Run the command:
Update-LapsADSchema
Update-LapsADSchema : A local error occurred.
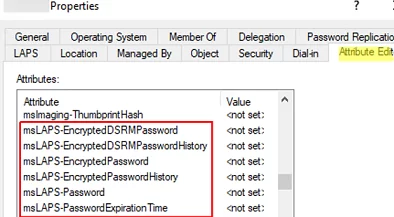
The following attributes will be added to the AD schema:
- msLAPS-PasswordExpirationTime
- msLAPS-Password
- msLAPS-EncryptedPassword
- msLAPS-EncryptedPasswordHistory
- msLAPS-EncryptedDSRMPassword
- msLAPS-EncryptedDSRMPasswordHistory
Open the ADUC console (dsa.msc), select any computer in AD, and go to the AD object Attribute Editor tab. Check that the object now has new attributes available.
The msLAPS* attributes are not yet populated.
You must now allow computers in the specified Organizational Unit (OU) to update msLAPS* attributes in their AD account properties.
For example, I want to allow computers in a MUN container to update passwords stored in AD attributes.
Set-LapsADComputerSelfPermission -Identity "OU=Computers,OU=MUN,OU=DE,DC=woshub,DC=com"
Let’s use PowerShell to create a domain security group that can view local administrator passwords on computers in this OU:
New-ADGroup MUN-LAPS-Admins -path 'OU=Groups,OU=MUN,OU=DE,DC=woshub,DC=com' -GroupScope local -PassThru –Verbose
Add-AdGroupMember -Identity MUN-LAPS-Admins -Members a.morgan,b.krauz
We will allow this group to view and reset the local admin password:
$ComputerOU = "OU=Computers,OU=MUN,OU=DE,DC=woshub,DC=com"
Set-LapsADReadPasswordPermission –Identity $ComputerOU –AllowedPrincipals MUN-LAPS-Admins
Set-LapsADResetPasswordPermission -Identity $ComputerOU -AllowedPrincipals MUN-LAPS-Admins
Use the Find-LapsADExtendedRights command to check the current permissions to LAPS attributes in an OU.
Configure GPO to Change Local Administrator Passwords
A new set of administrative templates for managing the LAPS configuration via GPO will appear when you install the latest updates on Windows (%systemroot%\PolicyDefinitions\laps.admx).
Copy LAPS.admx to the following location if you are using a Central GPO store for the ADMX templates: \\woshub.com\SysVol\woshub.com\Policies\PolicyDefinitions .
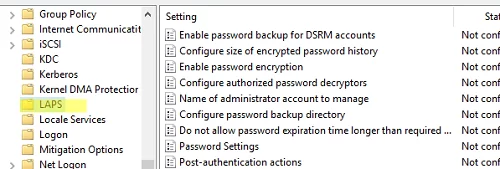
The next GPO section contains the LAPS options: Computer Configuration -> Policies -> Administrative Templates -> System -> LAPS. The following LAPS group policy options are available here:
- Enable password backup for DSRM accounts
- Configure size of encrypted password history
- Enable password encryption
- Configure authorized password descriptors
- Name of administrator account to manage
- Configure password backup directory
- Do not allow password expiration time longer than required by policy
- Password Settings
- Post-authentication actions
Let’s try to enable the minimum Group Policy LAPS settings for the Active Directory domain
- Open the Group Policy Management console (
gpmc.msc), create a new GPO and link it to the OU containing the computers; - Open a new GPO and navigate to the section that contains the LAPS options;
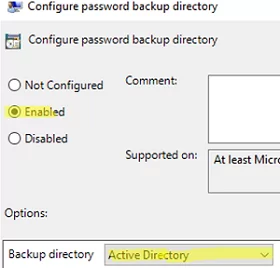
- Enable the Configure password backup directory policy and set Active Directory here. This policy allows the administrator password to be stored in the computer account attribute in the on-premises Active Directory;Windows LAPS also allows you to store passwords in the Azure Active Directory (AAD) instead of in the local ADDS.
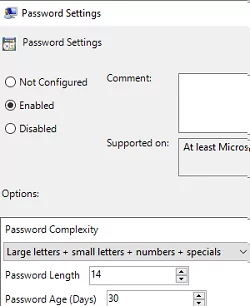
- Then enable the Password Settings option. Here you must specify the password complexity, length, and change frequency parameters;The following LAPS password settings are enabled by default: password complexity, 14-character password length, and password change every 30 days.
Specify the name of the local administrator account whose password you want to change in Name of administrator account to manage. If you are using the built-in Windows Administrator, type Administrator here.
The LAPS GPO does not create any local administrator accounts. If you want to use another administrator account, create it on computers using GPO or PowerShell.- Restart your computer to apply the new GPO settings.
LAPS: Get a Local Administrator Password on Windows
After implementing LAPS group policies, Windows changes the local administrator password at startup and then writes it to the msLAPS-Password protected attribute on the computer object in AD. You can get the current password for the computer in the ADUC console or by using PowerShell.
Open the ADUC console and search for the computer for which you want to find out the current password of the local administrator. A new LAPS tab has appeared in the Computer object properties.
The following info is displayed on this tab:
- Current LAPS password expiration
- LAPS local admin account name
- LAPS local admin account password
You can also use PowerShell to get the computer’s current administrator password:
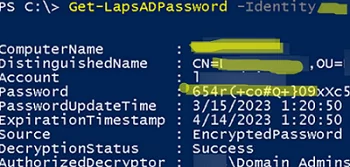
Get-LapsADPassword mun-pc221 -AsPlainText
ComputerName : mun-pc221 DistinguishedName : CN=mun-pc221,OU=… Account : administrator Password : 3f!lD1.23!l32 PasswordUpdateTime : 4/24/2023 11:14:26 AM ExpirationTimestamp : 5/24/2023 11:14:26 AM Source : EncryptedPassword DecryptionStatus : Success AuthorizedDecryptor : WOSHUB\Domain Admins
Use this password to log on locally to this computer as an administrator.
To immediately rotate the LAPS password for the local admin account, run the command:
Reset-LapsPassword
This will force an immediate password change for the currently logged local administrator account and write the new password to AD.
Windows Local Administrator Password Solution is a simple, built-in feature that allows you to improve the security of using local administrator accounts on domain computers. LAPS stores the current administrator password in a secure AD attribute and changes it on all computers regularly.
 Specify the name of the local administrator account whose password you want to change in Name of administrator account to manage. If you are using the
Specify the name of the local administrator account whose password you want to change in Name of administrator account to manage. If you are using the 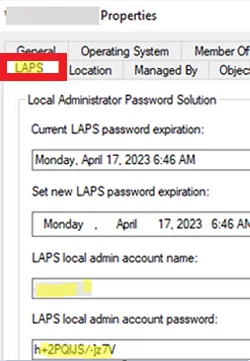
15 comments
does Laps management tool has to be installed in Domain controller or it can be on any management server. if i install Laps management tool on other server what port it uses for communication between AD server and Laps Management server
You can install LAPS management tool on any domain computer. There is no dedicated LAPS management server all LAPS data stored in the AD database. So, you don’t need to open any additional network ports to the your DCs to manage and view LAPS data.
Can LAPS help me with local admins which their user name is not “Administrator”?
I have an organization that I manage with domain, but through the time many users made themselves local admins on computers.
Can LAPS can change all those local users’ passwords randomly ?
No. LAPS focus on the default local admin and by default LAPS will target this account by checking the well-knows SID of the local admin. If you want to manage the other local accounts, I suggest use some scheduled tasks which will identify the local admin accounts and rotate their password after or you can use any PAM solution.
Hi,
I install LAPS and do to “Find-AdmPwdExtendedRights -Identity Desktops | Format-Table ExtendedRightHolders” step.
After i reset the AD server, now i can not login with any administrator password.
Could you help me solve this?
Hi,
Is there a procedure to recover the password for a deleted computer account?
Thank you.
Restore the deleted computer object from the AD Recycle Bin. It will include LAPS attributes
https://woshub.com/restore-deleted-active-directory-objects-users/
“At least Windows Server 2016 domain functional level is required for the new version of Windows LAPS.”
Where does the documentation say so? It’s working just fine here in our DFL 2012 domain.
The only thing that requires DFL 2016 is encryption of the passwords.
Hello, all my domain controllers are 2012R2 (DFL2012) . I don’t have new powerhell cmdlet like update-lapsadschema on these servers. But on any domains servers 2019 is ok. Can I update my ad schema from these servers or I absolutly need DC 2016 or 2019? thanks
PS: English is not my native english so sorry for the spelling and grammar 😀
Wondering if you ever got an answer to this?
The Windows Server Active Directory schema must be updated prior to using Windows LAPS. This action is performed by using the Update-LapsADSchema cmdlet. This operation can be performed on a Windows Server 2022/2016 DCupdated with Windows LAPS, but may also be performed on a non-domain-controller as long as it supports the Windows LAPS PowerShell module.
_https://learn.microsoft.com/en-us/windows-server/identity/laps/laps-scenarios-windows-server-active-directory
Hello, only one question.
The New version of LAPS work only on 2019/2022 – Windows 11 21H1 above and 10 22H2 ?
That’s right.
Windows LAPS is now available on the following OS platforms with the specified update or later installed:
Windows 11 22H2 – April 11 2023 Update
Windows 11 21H2 – April 11 2023 Update
Windows 10 – April 11 2023 Update
Windows Server 2022 – April 11 2023 Update
Windows Server 2019 – April 11 2023 Update
_https://learn.microsoft.com/en-us/windows-server/identity/laps/laps-overview
The legacy legacy Microsoft LAPS product is deprecated as of Windows 11 23 H2 and later.
Creating a LAPS GPO and back up server passwords to local AD, and back up workstation password to Entra via Intune – wouldn’t that be possible?