Domain users can change their password either via the Windows Security menu after logging in, or directly from the Windows login screen if their password has expired. If a user forgets their password or their account is compromised, a domain administrator or a member of the Account Operators group can reset the password. This article will cover the main tools used to reset an Active Directory user’s password.
Resetting a User’s Password in Active Directory (GUI)
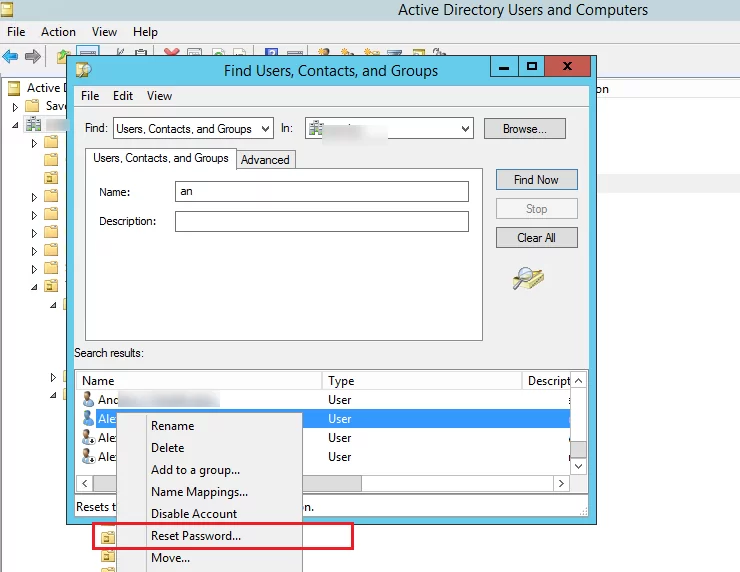
The domain user passwords can be reset by using the Active Directory Users and Computers graphical snap-in (ADUC). This is the simplest and most intuitive graphical tool for changing a domain user’s password.
- Open the
dsa.msc(ADUC) snap-in - Search for the AD user account whose password you want to change.
- Right-click on it and select Reset password
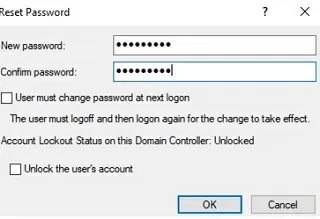
Enter a new password (twice). Here you can enable two options:
- User must change password at next logon – if you want users to set new passwords the next time they logon to the domain
- Unlock user’s account – enable this option if you want to unlock the AD user (use this option if the account has been locked by the AD security policy due to failed login attempts. Learn more about finding the source of a user lockout in Active Directory).
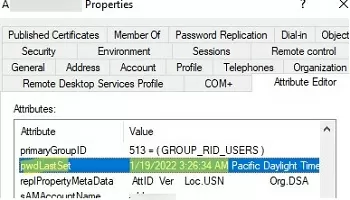
The date of the last password change can be found in the user properties on the AD attribute editor tab. This value is stored in the pwdLastSet user attribute.
To reset a domain user’s password, your account must have the necessary privileges in the Active Directory (AD) domain. By default, non-admin regular AD users cannot reset the passwords of other accounts. These permissions are granted by default only to members of the Domain Admins and Account Operators groups. With Active Directory delegation, you can grant other user groups the right to reset user passwords in specific Organizational Units (OUs). The post at the link explains how to delegate password reset and user unlock permissions to the HelpDesk group.
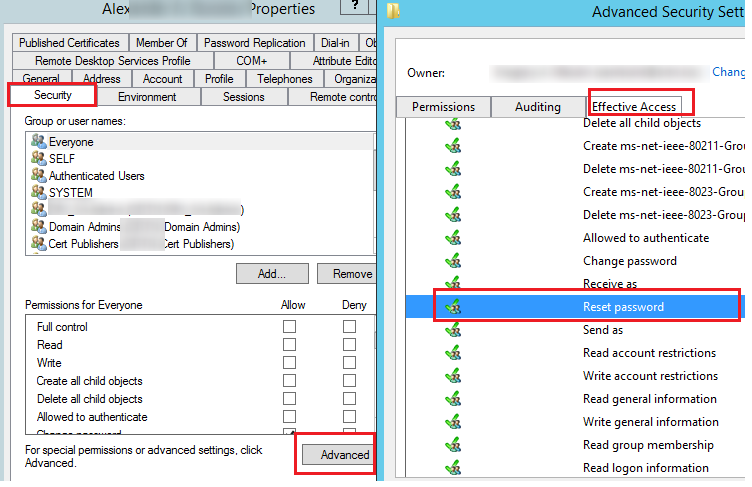
To verify that your account has permission to reset a specific AD user’s password, open its properties in the ADUC console, go to the Security tab -> Advanced -> Effective Access. Specify the name of your account -> make sure that you have the ‘Reset Password’ permission.
Reset Active Directory User Passwords with PowerShell
Use the PowerShell command Set-ADAccountPassword to reset a domain user’s password. In order to use this cmdlet, the Active Directory for Windows PowerShell module must be installed on a computer. In desktop Windows versions, this module is part of RSAT. In Windows Server, it is installed as a separate option of AD DS Snap-Ins and Command-Line Tools.
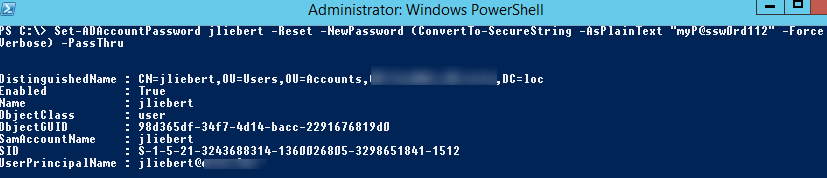
To reset a password for user jliebert and set a new password myP@ssw0rd112, run this command:
Set-ADAccountPassword jliebert -Reset -NewPassword (ConvertTo-SecureString -AsPlainText "myP@ssw0rd112" -Force -Verbose) –PassThru
By default, the cmdlet returns the object and displays nothing in the console. Add the -PassThru option to display information about the user object in AD.
You can specify a username as sAMAccountName (as in our case), objectGUID, the user’s SID, or a DN (Distinguished Name, e. g., CN=jliebert,OU=Users,DC=woshub,DC=com).
If you do not specify the -Reset option when changing a user password, you will have to input the old account password first.
Set-ADAccountPassword: The password does not meet the length, complexity, or history requirement of the domain.
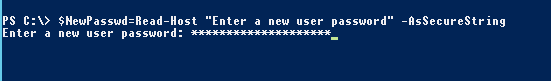
If you have PowerShell command history enabled and want to avoid displaying passwords as plain text in the console, convert the password into a secure string in the same way as when creating a new user account:
$NewPasswd=Read-Host "Enter a new user password" –AsSecureString
You can now set a new password for the user:
Set-ADAccountPassword jliebert -Reset –NewPassword $NewPasswd –PassThru
The additional useful commands often used when resetting a password are listed below:
- Unlock the user account in Active Directory:
Unlock-ADAccount –Identity jliebert - Require users to change their temporary passwords the next time they logon (this is achieved by enabling the ChangePasswordAtLogon flag in the userAccountControl object attribute):
Set-ADuser –Identity jliebert -ChangePasswordAtLogon $True
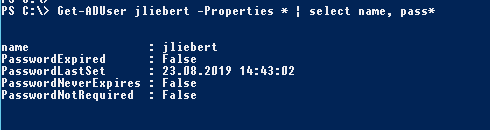
Use the Get-ADUser cmdlet to verify that the user’s password has been successfully reset and to display the last password change date.
Get-ADUser jliebert -Properties * | select name, pass*
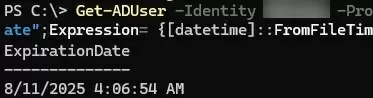
Get-ADUser -Identity simonecole -Properties msDS-UserPasswordExpiryTimeComputed | select-object @{Name="ExpirationDate";Expression= {[datetime]::FromFileTime($_."msDS-UserPasswordExpiryTimeComputed") }}
You can extend the password expiration date for an Active Directory user as follows.
Bulk User Password Change in AD with PowerShell
Sometimes, an administrator needs to change or reset the passwords of multiple users in a domain at once.
For example, the following command will set the same password for all Sales department employees and require them to change it at logon.
Get-ADuser -filter "department -eq 'Sales Dept' -AND enabled -eq 'True'" | Set-ADAccountPassword -NewPassword $NewPasswd -Reset -PassThru | Set-ADuser -ChangePasswordAtLogon $True
Another password reset scenario can be implemented. Suppose you have a CSV or Excel file containing a list of users whose passwords need to be reset, each with a unique password. The format of the users.csv file is as follows:
sAMAccountName;NewPassword acidicjustine;Pa$$w0r1 josephomoore;N$isory01 simonecole;k@32d3!2
The following PowerShell script imports from a CSV file a list of users and their new passwords and resets each user’s password.
Import-Csv users.csv -Delimiter ";" | Foreach {
$NewPass = ConvertTo-SecureString -AsPlainText $_.NewPassword -Force
Set-ADAccountPassword -Identity $_.sAMAccountName -NewPassword $NewPass -Reset -PassThru | Set-ADUser -ChangePasswordAtLogon $false
}
Executing this code will set a new, unique password for all Active Directory users in the CSV file.
Change a Domain User’s Password from the Command Line
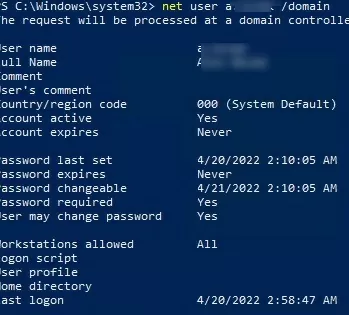
If you don’t have the ADUC console or the RSAT-AD-PowerShell module installed on a computer, you can reset the domain user password using the net use console command. To get information about a domain user, run the command:
net user jliebert /domain
The command line shows basic information about the user’s password properties in the domain:
Password last set 4/22/2022 2:15:15 AM Password expires Never Password changeable 4/23/2022 2:15:15 AM Password required Yes User may change password Yes Last logon 4/22/2022 2:48:12 AM Logon hours allowed All
The “net use” output also includes the date of the last password change and the date the user last logged in to the domain (see how to check a user’s logon history in Active Directory).
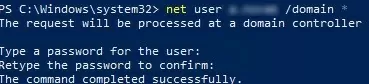
To reset this user’s password, run the command:
net user jliebert /domain *
Enter a new password and confirm it:
Type a password for the user: xxxx Retype the password to confirm: xxxx The command completed successfully.
How to Audit Who Reset a Password for an AD User
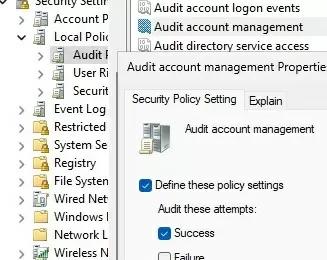
To identify which administrator reset a user’s password, enable auditing of password reset events via domain Group Policy (GPO).
- Open the Domain GPO Management Console (
gpmc.msc) - Edit the Default Domain Controller Policy and navigate to Computer Configuration -> Policies -> Windows Settings -> Security Settings -> Local Policies -> Audit Policy
- Enable the policy Audit User Account Management (Define these policy settings: Success)
- After updating the Group Policy settings on the domain controller, the password reset events will be logged in the Event Viewer.
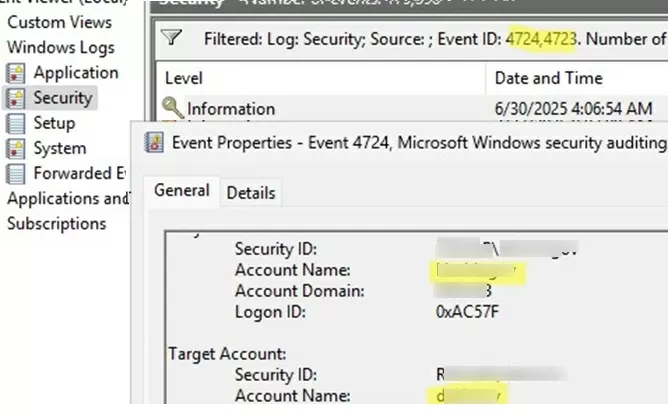
- Open the
eventvwr.mscconsole and filter the Security log with the following Event IDs 4724 (the password was reset by the administrator) and 4723 (the user changed their password). - The event description ‘An attempt was made to reset an account’s password’ contains the username for which the password was reset (Target Account), as well as the administrator account that made the change (Subject). To store more recent events in the Security log on a domain controller, you need to increase the maximum log size in Event Viewer.
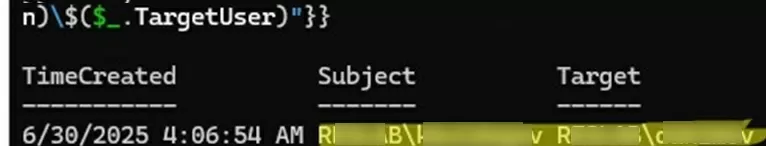
PowerShell can be used to list all password change events from the Event Viewer logs. For example, this script will show the names of the administrator and the users whose passwords were reset.
Get-WinEvent -FilterHashtable @{LogName='Security'; Id=4724} | ForEach-Object {
$xml = [xml]$_.ToXml()
$data = $xml.Event.EventData.Data
[PSCustomObject]@{
TimeCreated = $_.TimeCreated
SubjectUser = ($data | Where-Object Name -eq 'SubjectUserName').'#text'
SubjectDomain = ($data | Where-Object Name -eq 'SubjectDomainName').'#text'
TargetUser = ($data | Where-Object Name -eq 'TargetUserName').'#text'
TargetDomain = ($data | Where-Object Name -eq 'TargetDomainName').'#text'
}
} | Select TimeCreated, @{n='Subject';e={"$($_.SubjectDomain)\$($_.SubjectUser)"}}, @{n='Target';e={"$($_.TargetDomain)\$($_.TargetUser)"}}