According to the official VMware documentation, reinstalling ESXi from scratch is the only supported way to reset the root password (https://kb.vmware.com/s/article/1317898). You can also reset your password using Host Profiles (vCenter and Enterprise Plus license required). However, your ESXi host configuration will be completely lost after a reinstall. Virtual machine data and configuration files remain on the VMFS/NFS datastore and can be quickly imported to the host after reinstallation.
Actually, you can reset the root password on VMware ESXi without reinstalling if you boot your host using any Linux boot/rescue disk. It’s not difficult.
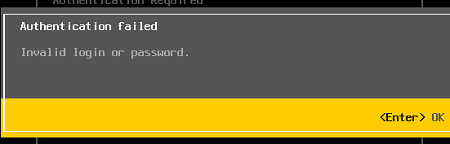
If you have forgotten your root password, you will not be able to authenticate as root using the DCUI or the VMware Host Client web interface:
Authentication failed Invalid login or password.
How to Reset ESXi Password Using Linux Live CD
ESXi stores user passwords (or rather their hashes) in the /etc/shadow file, which is stored in the local.tgz archive, which is archived in state.tgz. In theory, you could retrieve and decrypt the root password hash from this file, but this is only feasible for simple passwords. So it is better to set a blank current root password in the shadow file or replace it with the hash of a password you know.
Boot your ESXi host from any Linux LiveCD and open the console.
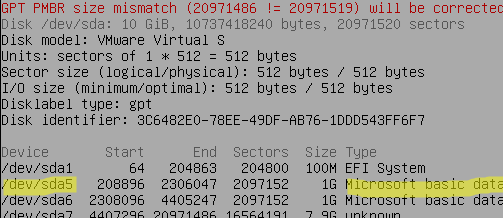
List disk partitions:
# fdisk –l
We need /dev/sda5 (in VMware terms, it is called bootbank) and /dev/sda6 (contains altrbootbank) partitions with the size of 1 GB in ESXi 7.x (in previous ESXi versions, the size of these partitions was 250 MB).
First, reset a password in the ESXi configuration in /dev/sda5. Create mount points and a directory for temporary files:
# mkdir /mnt/sda5
# mkdir /mnt/sda6
# mkdir /temp
Mount /dev/sda5:
# mount /dev/sda5 /mnt/sda5
Copy state.tgz file from sda5:
# cp /mnt/sda5/state.tgz /temp
# cd /temp
Unpack state.tgz:
# tar xzf state.tgz
There is another local.tgz archive inside, unpack it as well:
# tar xzf local.tgz
The etc folder appears in the current directory.
Edit the shadow file using any text editor:
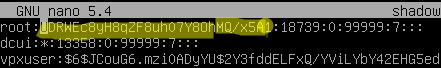
# nano /temp/etc/shadow
This file contains the password hashes of the local ESXi users.
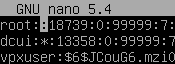
To remove the current password and set a blank password for root, clear the hash value. It should look like this:
Save your changes to the file, delete the old tgz archives, and repack them all:
# rm *.tgz
# tar czf local.tgz etc
# tar czf state.tgz local.tgz
Replace the state.tgz file on the sda5 ESXi partition:
# mv state.tgz /mnt/sda5
Unmount the partition:
# umount /mnt/sda5
In the same way, set a blank password in the passwd file on the sda6 partition (you should now be able to connect to ESXi with an empty root password).
Now you can restart your ESXi host and remove the bootable flash drive/image. You can connect to ESXi with an empty root password.
This password reset method works for all versions of ESXi (5.x, 6.x, 7.x, and 8.x) including the free VMware Hypervisor.
Reset ESXi Root Password Using VMware Host Profiles
If you have deployed vCenter and have installed vSphere Enterprise Plus licenses on hosts, you can reset the root password on any managed host using VMware Host Profiles. In this scenario, to apply VMware profile settings (and new root password) to an ESXi host, the vpxa privileged account is used, which is added when connecting a host to vCenter. This method allows you to reset the root password without rebooting the ESXi host.
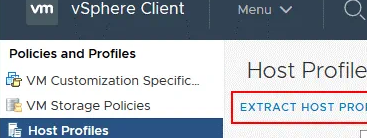
- Connect to your vCenter and go to Policies and Profiles -> Host Profiles -> Extract Host Profile;
- Select your ESXi host and specify the name of the profile you want to save the settings to;
- Click on the profile and select Edit Host Profile;
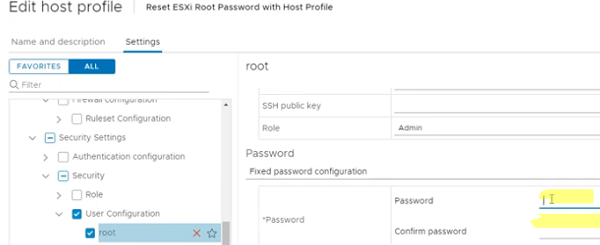
- Go to Security and Services -> Security Settings -> Security -> User Configuration -> root;
- Set a new root password in the Fixed password configuration;
- Then apply the profile to your ESXi host. It is recommended that you enable the maintenance mode for it (Maintenance Mode -> Enter Maintenance) and move all virtual machines to other hosts;
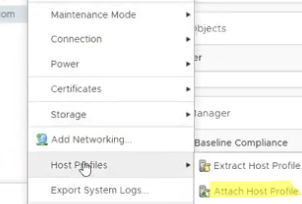
- Attach the profile to the host (Host profiles -> Attach Host Profile);
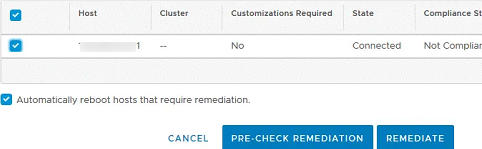
- Then go to Host Profiles, select your profile, and click Remediate;
- To apply profile settings (including the new password), click Remediate again;
- The root password on your ESXi host is reset and you can take the host out of maintenance mode.