In PowerShell, you can use the Test-NetConnection cmdlet to check whether a port is available (open) on a remote computer. You can use this cmdlet to check the response and availability of a remote server or a network service, test whether the TCP port is blocked by a firewall, check ICMP availability, and routing. In fact, Test-NetConnection replaces several popular network admin tools such as ping, tracert, telnet, pathping, TCP port scanner, etc.
Check for Open TCP Port with Test-NetConnection
You can use the Test-NetConnection cmdlet to check only TCP ports. For example, to check that TCP port 25 (the SMTP protocol) is open on the remote mail server:
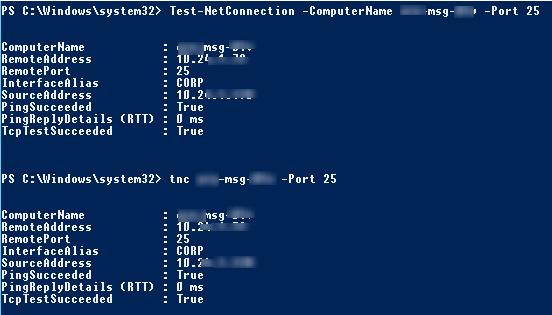
Test-NetConnection -ComputerName ny-msg01 -Port 25
The Test-NetConnection command has the alias TNC. The shortened version of the same command looks like this:
TNC ny-msg01 -Port 25
Let’s look at the result of the command:
ComputerName : ny-msg01 RemoteAddress : 10.20.1.7 RemotePort : 25 InterfaceAlias : CORP SourceAddress : 10.20.1.79 PingSucceeded : True PingReplyDetails (RTT) : 0 ms TcpTestSucceeded : True
As you can see, the cmdlet resolves the server name to an IP address, checks the ICMP response (similar to ping), and checks the response from the TCP port (port availability). The specified server responds via ICMP (PingSucceeded = True) and the TCP Port 25 is open (RemotePort=25, TcpTestSucceeded= True).
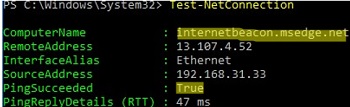
If you run the Test-NetConnection without parameters, it will check if the computer is connected to the Internet (checks for the availability of the internetbeacon.msedge.nethost).
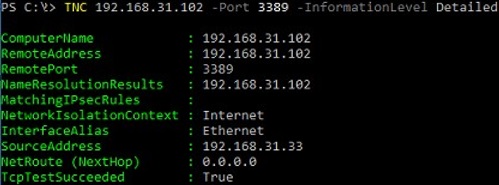
You can add the –InformationLevel Detailed option to display detailed information when checking a remote TCP port:
TNC 192.168.32.101 -Port 3389 -InformationLevel Detailed
The cmdlet has a special parameter –CommonTCPPort, which allows you to specify the name of a known network protocol (HTTP, RDP, SMB, WINRM).
For example, to check the availability of an HTTP web server you can use the command:
Test-NetConnection -ComputerName woshub.com -CommonTCPPort HTTP
Or check the availability of a default RDP port (TCP/3389):
Test-NetConnection ny-rds1 –CommonTCPPort RDP
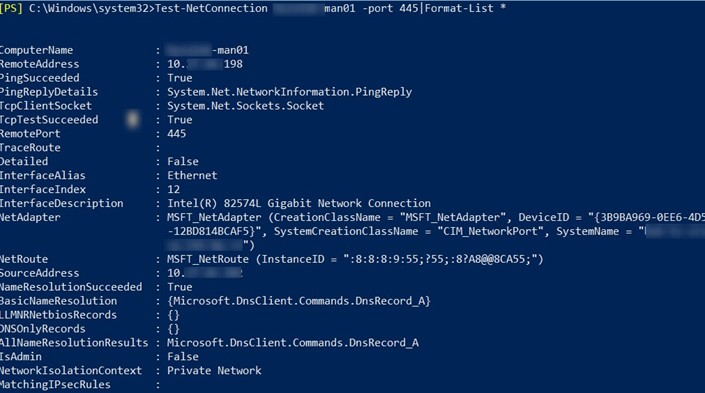
You can list all of the parameters that the Test-NetConnection cmdlet returns:
Test-NetConnection ny-man01 -port 445|Format-List *
If you only need to see if the port is available, it can be checked more quickly:
TNC ny-msg1 -Port 25 -InformationLevel Quiet
The cmdlet returns True, which means that the remote TCP port is open.
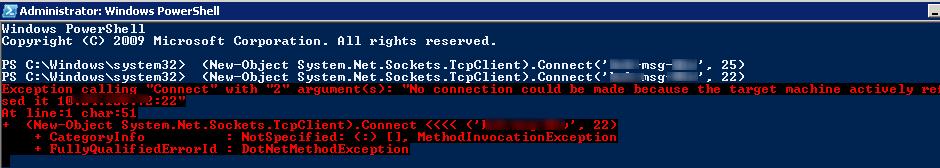
(New-Object System.Net.Sockets.TcpClient).Connect('ny-msg01', 25)
You can use the Test-NetConnection cmdlet to trace a route to a remote server by using the –TraceRoute parameter (similar to the built-in tracert command in Windows). You can limit the maximum number of hops during the route check by using the -Hops parameter.
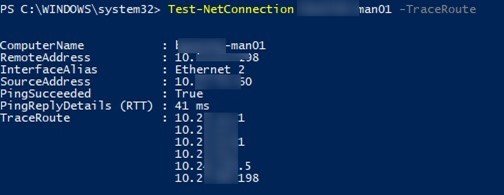
Test-NetConnection ny-man01 –TraceRoute
Cmdlet returned a summary network access delay in milliseconds (PingReplyDetails (RTT): 41 ms) as well as all the IP addresses of the routers on the way to the destination host.
PowerShell: Check for Open Ports on Multiple Hosts
You can use PowerShell to check for the availability of a specific port on a number of remote computers. Save the list of hostnames or IP addresses in a plain text file with the name servers.txt.
For example, your task is to find hosts where the TCP/25 port is not responding or is closed on a list of servers:
Get-Content c:\PS\list_servers.txt | where { -NOT (Test-Netconnection $_ -Port 25 -InformationLevel Quiet)}| Format-Table -AutoSize
You can use a simple monitoring PowerShell script that checks the availability of remote servers and displays a pop-up notification if any of the servers are unavailable.
For example, you can check the availability of basic services on all domain controllers during an AD health check (a DC list can be obtained with the Get-ADDomainController cmdlet). Let’s check the following services on the DC (there is a similar ‘Domain and trusts‘ rule in the PortQry tool):
- RPC – TCP/135
- LDAP – TCP/389
- LDAP – TCP/3268
- DNS – TCP/53
- Kerberos – TCP/88
- SMB – TCP/445
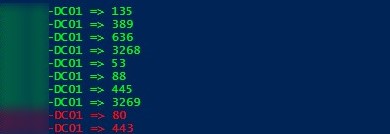
$Ports = "135","389","636","3268","53","88","445","3269", "80", "443"
$AllDCs = Get-ADDomainController -Filter * | Select-Object Hostname,Ipv4address
ForEach($DC in $AllDCs){
Foreach ($P in $Ports){
$check=Test-NetConnection $DC.Ipv4address -Port $P -WarningAction SilentlyContinue
If ($check.tcpTestSucceeded -eq $true)
{Write-Host $DC.hostname $P -ForegroundColor Green -Separator " => "}
else
{Write-Host $DC.hostname $P -Separator " => " -ForegroundColor Red}
}
}
The script checks the specified TCP ports on the domain controllers, and if any of the ports are unavailable, it highlights them in red (you can run this PowerShell script as a Windows service).
Simple TCP/IP Port Scanner in PowerShell
You can use PowerShell to implement a simple IP scanner that scans remote hosts or IP subnets for open/closed TCP ports.
To scan the range of IP addresses between 192.168.1.100 and 192.168.1.150 and display computers that have port 3389 open:
foreach ($ip in 100..150) {Test-NetConnection -Port 3389 -InformationLevel "Detailed" 192.168.1.$ip}
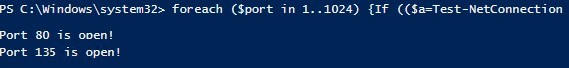
Scan a range of TCP ports (from 1 to 1024) on a remote host:
foreach ($port in 1..1024) {If (($a=Test-NetConnection srvfs01 -Port $port -WarningAction SilentlyContinue).tcpTestSucceeded -eq $true){ "TCP port $port is open!"}}
How to List Open Ports on Windows with PowerShell
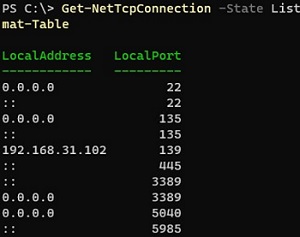
Use the Get-NetTCPConnection cmdlet to list the ports that are open on the local computer (this is the PowerShell equivalent of NETSTAT). A list of all open TCP ports on the computer can be viewed as follows:
Get-NetTcpConnection -State Listen | Select-Object LocalAddress,LocalPort| Sort-Object -Property LocalPort | Format-Table
If you want to find out which program (process) is listening on a specific port on your computer, use the following command (where 443 is a port number you want to check):
Get-Process -Id (Get-NetTCPConnection -LocalPort 443).OwningProcess | ft Id, ProcessName, UserName, Path
3 comments
blurred hostname in imagery, kept in it write-up… :
Of course, hostnames are replaced with arbitrary values in the text.
#Small update for looping variables:
$Ports = “135”,”389″,”636″,”3268″,”53″,”88″,”445″,”3269″, “80”, “443”
$AllDCs = Get-ADDomainController -Filter * | Select-Object Hostname,Ipv4address,isGlobalCatalog,Site,Forest,OperatingSystem
ForEach($DC in $AllDCs)
{
Foreach ($P in $Ports){
$check=Test-NetConnection $DC.Ipv4address -Port $P -WarningAction SilentlyContinue
If ($check.tcpTestSucceeded -eq $true)
{Write-Host $DC.Hostname $P -ForegroundColor Green -Separator ” => “}
else
{Write-Host $DC.Hostname $P -Separator ” => ” -ForegroundColor Red}
}
}