In some cases, the administrator needs to find out which process (program) or user has changed the NTFS permissions on a specific folder or file on a Windows file server. This article shows how to track NTFS permissions changes made to file system objects using audit policy, PowerShell scripts, and the ProcMon tool.
You need to configure an audit policy to track changes to NTFS permissions on Windows file system objects.
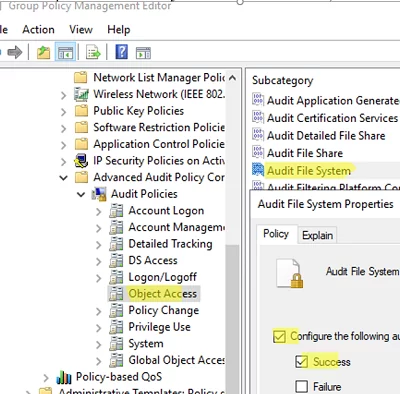
- Open the Group Policy Editor. If you want to configure the audit file system audit policy on a particular server, open the Local Group Policy Editor console (
gpedit.msc). If you want to enable auditing on multiple devices in a domain (for example, all file servers), you need to create a separate GPO using the Group Policy Management console (gpmc.msc); - Navigate to Computer Configuration -> Policies -> Windows Settings -> Security Settings -> Advanced Audit Policy Configuration -> Audit Policies -> Object Access;
- Enable the option Audit File System and select Success;
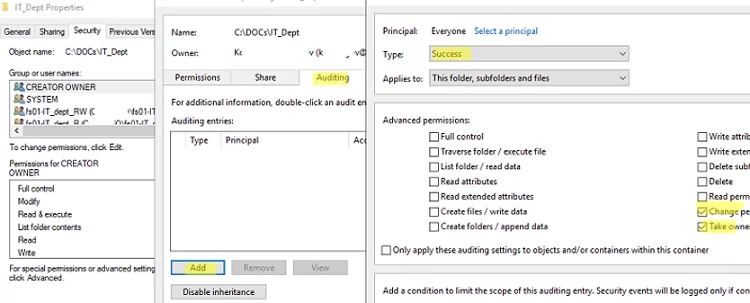
- Now you need to enable auditing in the properties of the directory in which you want to track permission changes. Open the folder properties -> go to Security tab -> Advanced -> Auditing tab -> Continue -> click Add and add a group (select a principal) whose activities you want to track. We have specified Everyone here;Previously, we showed you how to use file system auditing to find the user who deleted a file or folder on a Windows file server.
- Select Type=Success and enable the Change Permissions and Take Ownership options in Advanced Permissions:
- Don’t forget to update the Group Policy settings on the host:
gpupdate /force
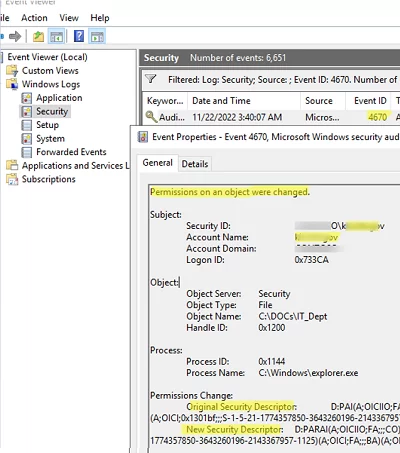
Now, if someone has changed NTFS permissions on items in the specified folder, an event with event ID 4670 will appear in the Security log.
Open the Event Viewer console (eventvwr.msc) -> Windows Logs -> Security. Filter the event list by the EventID 4670 (Permissions on an object were changed) and open the latest event.
You will see the name of the user who changed the permission (Account Name:) and the process name ( C:\Windows\explorer.exe ) in the event description. It also contains information about the previous ACL (Original Security Descriptor) and the new permission list (New Security Descriptor).
Please note that permissions are in DACL format and are difficult to understand. Fortunately, you can use the built-in PowerShell cmdlet ConvertFrom-SddlString to convert a Security Descriptor Definition Language string into a PSCustomObject.
To see which access groups have been changed in the object’s NTFS permissions, compare the old and the new security descriptors (copy the SDDL values from event 4670):
$oldperm=ConvertFrom-SddlString "D:PAI(A;OICIIO;FA;;;CO)(A;OICI;FA;;;SY)(A;OICI;FA;;;BA)(A;OICI;0x1200a9;;;S-1-5-21-1774357850-3643260196-2143367957-1125)(A;OICI;0x1301bf;;;S-1-5-21-1774357850-3643260196-2143367957-1124)"
$newperm=ConvertFrom-SddlString "D:PARAI(A;OICIIO;FA;;;CO)(A;OICI;FA;;;SY)(A;OICI;0x1301bf;;;S-1-5-21-1774357850-3643260196-2143367957-1124)(A;OICI;0x1200a9;;;S-1-5-21-1774357850-3643260196-2143367957-1125)(A;OICI;FA;;;BA)(A;OICI;0x1200a9;;;BU)"
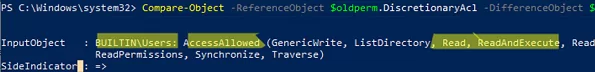
Compare-Object -ReferenceObject $oldperm.DiscretionaryAcl -DifferenceObject $newperm.DiscretionaryAcl|FL
In this example, you can see that the new ACL grants read permissions to the Builtin\Users group.
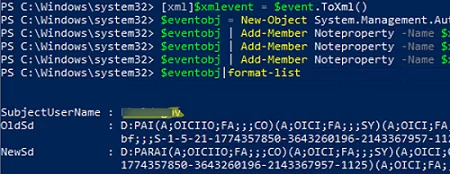
You can use the Get-WinEvent PowerShell cmdlet to search the Windows Event Log. For instance, you may use the following code to find events with Event ID 4670 and get OldSD and NewSD values from the script:
$event=Get-WinEvent -FilterHashtable @{logname='Security';id=4670} -MaxEvents 1
[xml]$xmlevent = $event.ToXml()
$eventobj = New-Object System.Management.Automation.PSObject
$eventobj | Add-Member Noteproperty -Name $xmlevent.Event.EventData.Data[1].name -Value $xmlevent.Event.EventData.Data[1].'#text'
$eventobj | Add-Member Noteproperty -Name $xmlevent.Event.EventData.Data[8].name -Value $xmlevent.Event.EventData.Data[8].'#text'
$eventobj | Add-Member Noteproperty -Name $xmlevent.Event.EventData.Data[9].name -Value $xmlevent.Event.EventData.Data[9].'#text'
$eventobj|format-list
icacls.exe tool or the Get-ACL PowerShell cmdlet to back up the current NTFS permissions of a directory.If you need to understand which process and user are changing NTFS permissions on a folder, you can use the Process Monitor utility. (https://learn.microsoft.com/en-us/sysinternals/downloads/procmon). It allows you to locate the source of permission changes to file system objects in real time.
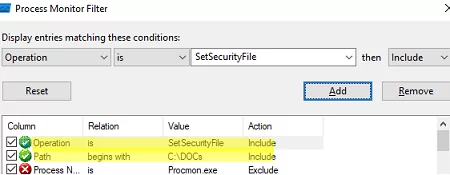
- Download and run procmon64.exe;
- Configure the filter: Filter-> Filter (
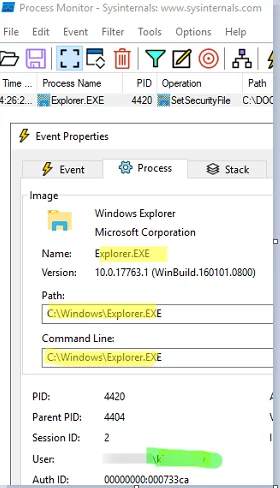
CTRL+S)Path -> begin with ->Specify the folder path->IncludeOperation -> is ->SetSecurityFile-> Include ; - From now on, if someone changes NTFS permissions on any object in that folder, you will see a new event in the ProcMon window. Here, it shows the process (explorer.exe) and the name of the user who changed the permissions.