In this article we will look at how to find out the date a user was created in Active Directory; how to use PowerShell to get information from the domain controller’s event logs about who created the user account and when the user last logged on to the domain. These tasks often occur when auditing user accounts in Active Directory, finding and deleting inactive AD objects, or collecting statistics.
AD User Accounts Creation Date
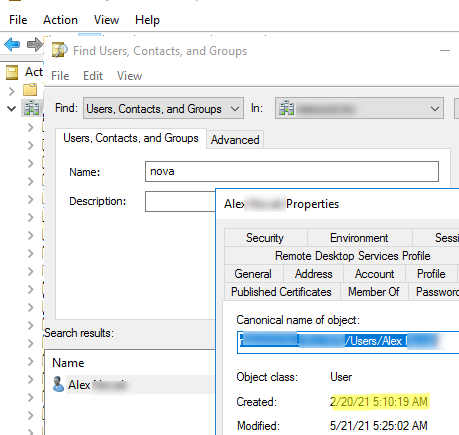
You can get the creation date of any Active Directory object (user, computer, or group) through the ADUC (dsa.msc) graphical snap-in (be sure to enable the Advanced Features option in the View menu).
- Find the required user in the ADUC tree manually or by using the AD search function;
- Open the user’s properties and select the Object tab;
- The date the object was created in the Active Directory is specified in the Created field.
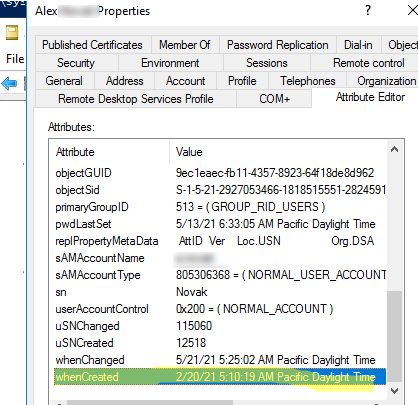
The same value can be obtained with the built-in AD attribute editor (whenCreated attribute).
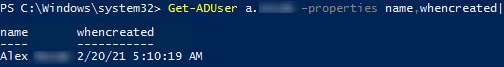
Also, you can use the Get-ADUser cmdlet from the AD PowerShell module to get the creation date of a user account:
Get-ADUser a.brion –properties name,whencreated|select name,whencreated
Finding Recently Created Active Directory Accounts with PowerShell
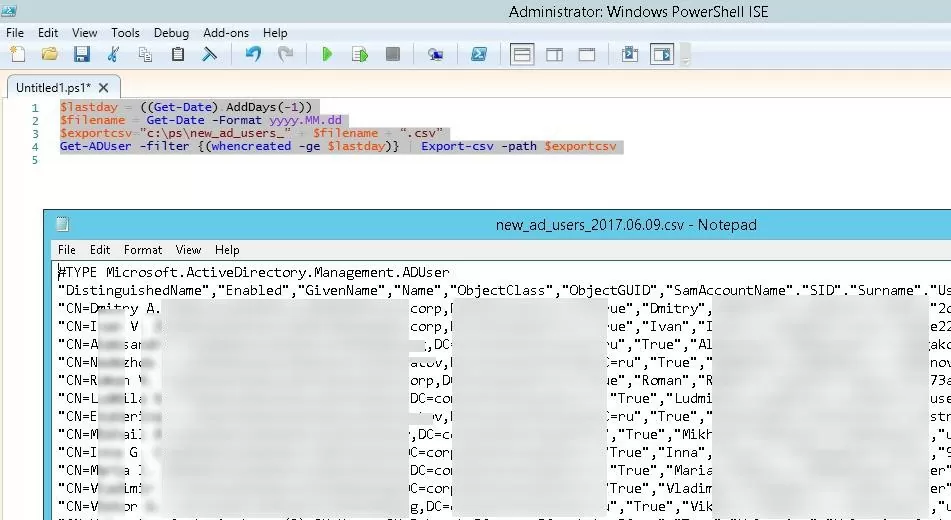
With a simple PowerShell script, you can list user accounts recently created in Active Directory. To do this, use the Get-ADUser cmdlet to select all users and filter them by the value of the whencreated user attribute. For example, the following PowerShell script will list users created in Active Directory in the last 24 hours:
$lastday = ((Get-Date).AddDays(-1))
$filename = Get-Date -Format yyyy.MM.dd
$exportcsv=”c:\ps\new_ad_users_” + $filename + “.csv”
Get-ADUser -filter {(whencreated -ge $lastday)} –properties whencreated | Select-Object Name, UserPrincipalName, SamAccountName, whencreated | Export-csv -path $exportcsv
In this example, the list of AD accounts is saved to a file with the current date as its name. You can make this script to run daily via Windows Task Scheduler. As a result, the files containing the information about the date of creation of new accounts will be saved in the directory you specified. You can add any other attributes of Active Directory users to your report (see the article on using the Get-ADUser cmdlet).
How to Find Out Who Created a User Account in Active Directory?
If there are multiple administrators in your Active Directory domain, or you have delegated the permissions to create and edit user accounts to other non-admin users (for example, to HR staff), you may interested in the information about the name of the user who created the specific account in Active Directory. This information can be found in the security logs of Active Directory domain controllers.
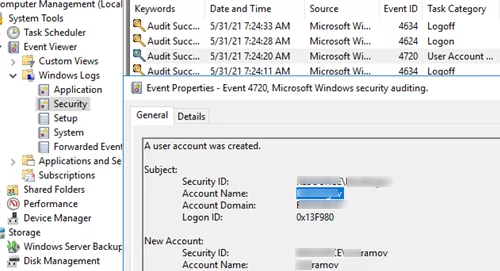
When you create a new user in the domain, an event with the EventID 4720 from the User Account Management source appears in the security log of the domain controller (only on the DC, on which the account has been created). The Audit User Account Management policy must be enabled in Default Domain Controller GPO.
The description of this event contains the string: A user account was created. The Subject field contains the account under which the new AD user account was created (highlighted in the screenshot below). The new username is specified in the New Account field.
You need to collect 4720 events from all domain controllers. You can get a list of DCs using the Get-ADDomainController cmdlet. Then it remains to check the events with ID 4720 on each of them and create a resulting report. The script for getting all account creation events from the domain controller logs for the last 24 hours can look like this:
$Report = @()
$time = (get-date) - (new-timespan -hour 24)
$AllDCs = Get-ADDomainController -Filter *
ForEach($DC in $AllDCs)
{
Get-WinEvent -ComputerName $dc.Name -FilterHashtable @{LogName="Security";ID=4720;StartTime=$Time}| Foreach {
$event = [xml]$_.ToXml()
if($event)
{
$Time = Get-Date $_.TimeCreated -UFormat "%Y-%m-%d %H:%M:%S"
$CreatorUser = $event.Event.EventData.Data[4]."#text"
$NewUser = $event.Event.EventData.Data[0]."#text"
$objReport = [PSCustomObject]@{
User = $NewUser
Creator = $CreatorUser
DC = $event.Event.System.computer
CreationDate = $Time
}
}
$Report += $objReport
}
}
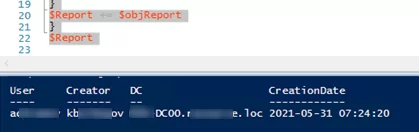
$Report
As a result, you have a $Report object containing information about who created the AD user, when, and on which domain controller.
You can export a report to a CSV file:
$filename = Get-Date -Format yyyy.MM.dd
$exportcsv=”c:\ps\ad_users_creators” + $filename + “.csv”
$Report | Export-Csv $exportcsv -append -NoTypeInformation -Delimiter ","
1 comment
Lovely guide, thank you !!