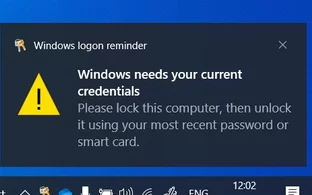
After signing into an Active Directory or Azure AD domain-joined computer running Windows 10/11, the user may see the following pop-up message in the lower right corner of the desktop:
Windows needs your current credentials. Please lock this computer, then unlock it using your most recent password or smart card.
You may try to lock the computer screen (press Win+L) and enter the password/PIN for your account, but the pop-up message will reappear after a while.
If the issue occurs when you sign in to a computer with a Microsoft (or Azure AD) account with a Windows Hello configured PIN, the most likely reason is that your current PIN was created based on your previous password. To resolve the issue, try creating a new PIN for your account.
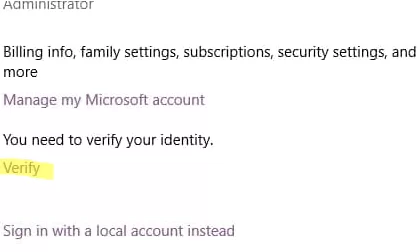
- Go to Settings -> Accounts -> You info (use a Settings URI shortcut command:
ms-settings:yourinfo) and click Verify;If you are logged in with a Microsoft account, this option should be available. If not, click “Sign in with a Microsoft Account instead”. - Sign in to your Microsoft account and restart your computer. Once that’s done, Windows should stop asking you for credentials.
If you’re signed in to a computer with an Azure account and the device has network drives mapped under a local Active Directory account, Windows may require you to verify your AD credentials. If this is the case, you need to remove all mapped network drives using the command:
net use * /delete
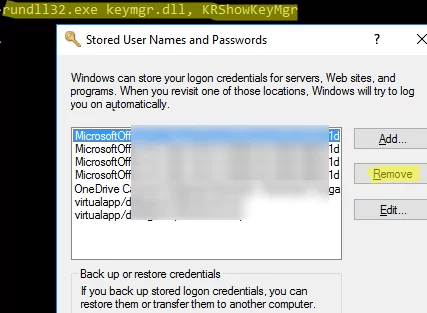
Another recommendation is to clear saved credentials in the Windows Credential Manager. For that, run the command rundll32.exe keymgr.dll, KRShowKeyMgr and remove all entries.
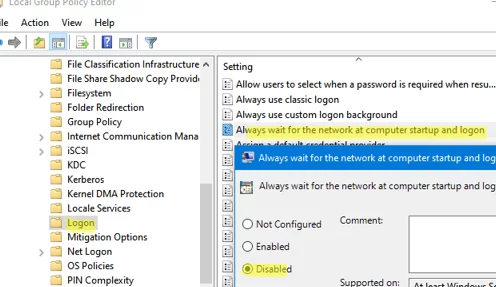
You can also disable the re-entry of credentials (not to be confused with Windows auto-login) on an Active Directory computer using a GPO:
- You can use either the local Group Policy editor on your computer (
gpedit.msc) or the domain Group Policy Management console (gpmc.msc); - Go to Computer Configuration -> Administrative Templets -> System -> Logon and find the option “Always wait for the network at computer startup and logon”;
- Set the policy on Disable and save the changes;
- Restart your computer to apply the new Group Policy settings.
$null = Set-ItemProperty -Path 'Registry::HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows NT\CurrentVersion\Winlogon' -Name 'SyncForegroundPolicy' -Value 0 -Type 'DWord'
One more thing to check on is to make sure the Logon Hours restrictions are not configured in the AD for this user’s account.
Sometimes users in an Active Directory domain get the credentials re-entry notification when the Kerberos ticket has expired. You can display information about a user’s Kerberos tickets with the command:
klist
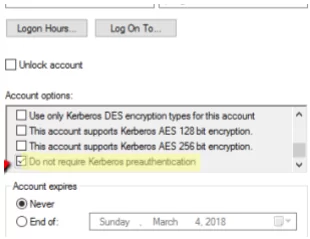
Enter your password to update your Kerberos ticket. This way, after the screen is locked and you re-enter your password, your Kerberos ticket will be updated and you will not be asked for your credentials again. If you want to be sure that your problem is related to Kerberos, open the AD Attribute Editor and enable the “Do not require Kerberos preauthentication” userAccountControl attribute. Once you turn it on, you will no longer receive Windows requests for your credentials. Still, leaving this setting enabled is not recommended for security reasons.
If your network uses hybrid authentication (both AAD and AD) or you are performing a cloud migration, you can get rid of the annoying request for credentials on computers in AAD by changing the DNS settings to external DNS servers instead of your local Active Directory name servers.
2 comments
Just thought I would mention that in your PowerShell command above, I believe the correct registry path should be HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon you had it as HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows NT\CurrentVersion\Winlogon which is an invalid path.
The registry parameters in the HKEY_LOCAL_MACHINE\SOFTWARE\Policies\… key match the settings set by the GPO. ( Per-machine as a policy).
The settings in HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\ are the per-machine settings.
So both options are possible.