The WPAD (Web Proxy Auto-Discovery) protocol allows you to easily configure the proxy settings on the clients in your network. The idea behind WPAD is that a client can use DHCP and/or DNS to find a web server on your network that has a PAC configuration file with proxy settings (http://yourdomain/wpad.dat).
Create Proxy Auto-Discovery File (wpad.dat)
A special PAC (Proxy Auto Configuration) file describes the rules for using a proxy. The PAC file predefined name is wpad.dat. This file contains rules that determine whether the client must use a proxy server when connecting to a specific resource (HTTP, HTTPS, or FTP) or access it directly.
Javascript syntax is used in the wpad.dat file. You can set a default proxy server address, as well as different exceptions and rules for when a client should (or should not) use a proxy for connections.
Let’s look at a simple example of wpad.dat syntax:
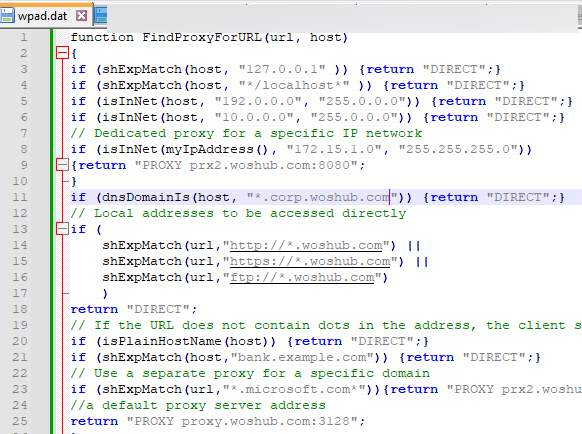
function FindProxyForURL(url, host)
{
if (shExpMatch(host, "127.0.0.1" )) {return "DIRECT";}
if (shExpMatch(host, "*/localhost*" )) {return "DIRECT";}
if (isInNet(host, "192.0.0.0", "255.0.0.0")) {return "DIRECT";}
if (isInNet(host, "10.0.0.0", "255.0.0.0")) {return "DIRECT";}
// Dedicated proxy for a specific IP network
if (isInNet(myIpAddress(), "172.15.1.0", "255.255.255.0"))
{return "PROXY prx2.woshub.com:8080";}
if (dnsDomainIs(host, "*.corp.woshub.com")) {return "DIRECT";}
// Local addresses to be accessed directly
if (
shExpMatch(url,"http://*.woshub.com") ||
shExpMatch(url,"https://*.woshub.com") ||
shExpMatch(url,"ftp://*.woshub.com")
)
return "DIRECT";
// If the URL does not contain dots in the address, the client should access it directly.
if (isPlainHostName(host)) {return "DIRECT";}
if (shExpMatch(host,"bank.example.com")) {return "DIRECT";}
// Use a separate proxy server to access a specific wildcard domain
if (shExpMatch(url,"*.microsoft.com*")){return "PROXY prx2.woshub.com:8080";}
//a default proxy server address
return "PROXY proxy.woshub.com:3128";
}
A PAC file typically consists of a single FindProxyForURL function that returns the proxy address to the client based on the requested URL. In this case, the return “DIRECT” directive indicates that a direct connection (without a proxy) should be used to access these IP addresses and domains. If the website a client is accessing doesn’t match any of the rules in the WPAD file, the default proxy server (PROXY proxy.woshub.com:3128) is used to access it.
You can use the PAC file as a simple means of content filtering to deny access to certain websites or to prevent access to domains with advertisements.
proxy_empty = "PROXY 127.0.0.1:3128"; // a link to an non-existing proxy
if ( shExpMatch(url,"*://twitter.com/*")) { return proxy_empty; }
if ( shExpMatch(url,"*://spam.*")) { return proxy_empty; }
if ( shExpMatch(url,"*doubleclick.net/*")) { return proxy_empty; }
Put wpad.dat on an HTTP web server in your local network and allow all users to read it. You can use a Linux-based (nginx, apache, lighttpd) or Windows-based (IIS or a simple HTTP server based on PowerShell) web server.
In this example, I will publish wpad.dat on an IIS web server on a domain controller. Copy wpad.dat to C:\inetpub\wwwroot.
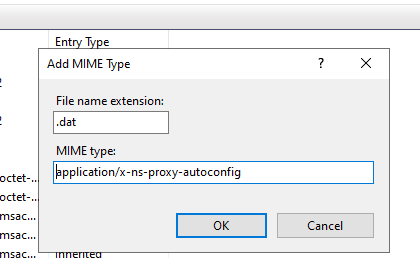
Open the IIS Manager (inetmgr), select MIME Types in the IIS website settings, and add a new type:
- File name extension:
.dat - MIME type:
application/x-ns-proxy-autoconfig
Restart IIS.
Configuring WPAD Records in DHCP or DNS
Now you need to configure DHCP servers or DNS records for clients to discover the PAC file.
If you use a DHCP server, you can set a WPAD address for clients using option 252. In this example for DHCP running on Windows Server:
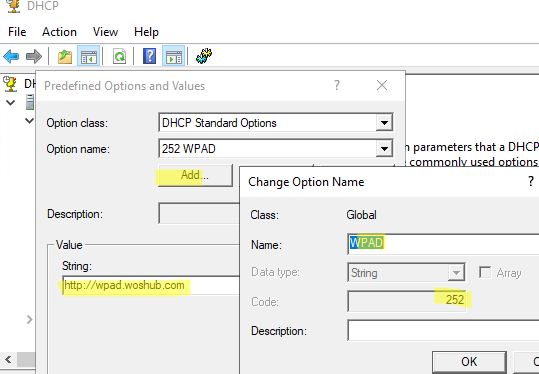
- Open the DHCP console (
dhcpmgmt.msc), click the IPv4 section, and select Set Predefined Options; - Click Add and add an entry with the following options:
Name:WPAD
Data type:string
Code:252 - Click OK and specify the address of your WPAD host (
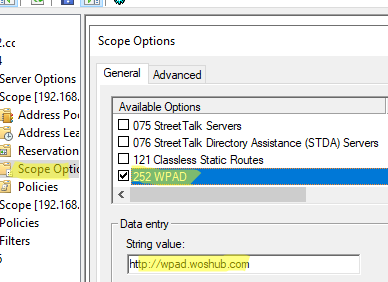
http://wpad.woshub.com). - Then open the Scope Options and enable the 252 WPAD option for it (or configure the setting in the Server Options section).
Then create A or CNAME DNS records for wpad name in your domain.
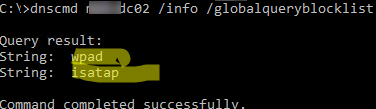
If you are using Active Directory, note that by default the Microsoft DNS server blocks the use of wpad and isatap names. You can check this by running the command::
dnscmd mun-dc02 /info /globalqueryblocklist
To allow these names to be used in DNS, run this command:
dnscmd mun-dc02 /config /enableglobalqueryblocklist 0
dnscmd /config /globalqueryblocklist
And add a record for isatap:
dnscmd /config /globalqueryblocklist isatap
Make the same changes to all DNS servers.
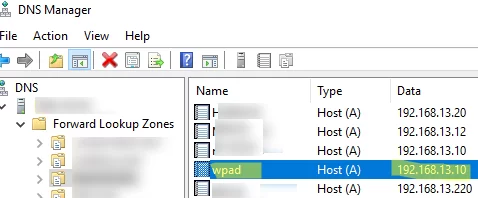
Then create an A record with the name wpad that points to your web server where the WPAD file is located. You can create an A record manually in the DNS Manager (dnsmgmt.msc) or by using the Add-DnsServerResourceRecordA PowerShell cmdlet:
Add-DnsServerResourceRecordA -Name wpad -IPv4Address 192.168.13.10 -ZoneName woshub.loc -TimeToLive 01:00:00
How to Configure Browsers for WPAD
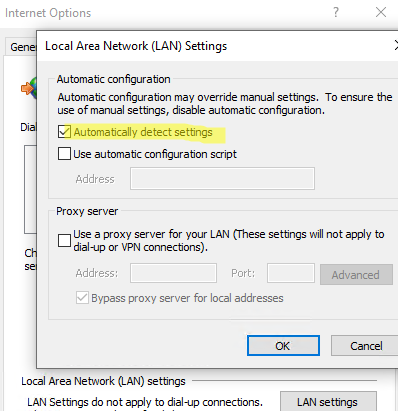
Now you need to configure your browsers to automatically receive a PAC file on startup. To do it, enable the Automatic Detect Settings option (Tools > Internet Options > Connections > LAN Settings) in the IE settings or in the Windows proxy settings in the Settings (MS-Settings quick URI command: ms-settings:network-proxy).
You can enable this option centrally using the Group Policy option User Configuration -> Preferences -> Control Panel Settings -> Internet Settings –> New ->Internet Explorer 10.
Now the browsers on the client devices will look for a wpad entry in the DNS (or get it from DHCP) when they are loaded. If a host with WPAD is discovered in the network, a client will download file http://wpad.%domain%/wpad.dat, run the JavaScript code, and apply the proxy-server rules from the PAC file.
For example, Windows searches the wpad name in DNS first, then through Link-Local Multicast Name Resolution (LLMNR), and after that using NetBIOS (NBNS). If LLMNR and NetBIOS protocols are disabled, only DNS search is used.
You can check whether the browser uses the PAC file when accessing the Internet (for Chromium-based web browsers: Google Chrome, Opera, Microsoft Edge):
- Open a browser and go to
chrome://net-export/ - Select Strip private information and click Start Logging to Disk;
- Then specify the JSON file name to save data;
- Click Stop Logging;
- Open your JSON file in any text editor and search for
proxySettings. In this example, you can see that the browser is using the proxy settings from wpad.dat:
"proxySettings":{"effective":{"pac_url":"http://wpad/wpad.dat"},"original":{"auto_detect":true,"from_system":true}}
If you want to deny the use of WPAD on a Windows computer, create a DWORD parameter called DisableWpad with a value of 1 in the registry key HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\WinHttp\.
Configuring proxy settings using the WPAD (PAC) file provides additional flexibility that cannot be achieved by setting the proxy through the Windows GPO. WPAD is also supported on Windows, Linux, MacOS, and other operating systems as well as mobile devices.