Group Policies allow centrally configuring Windows Update settings that determine how updates are received and installed on workstations and servers in a domain network. In this article, we’ll look at the basic GPO options that you can use to manage Windows Update settings on computers that receive updates from an intranet WSUS server or directly from Windows Update servers on the Internet.
Configure Windows Update GPO Settings for WSUS Clients
Once you have installed the local Windows Server Update Services (WSUS) host, configure the workstations and servers in your Active Directory to receive updates from it (instead of from Microsoft Update servers over the Internet).
In our example, we want to create two different update installation policies for workstations and servers. To do this, open the WSUS management console (wsus.msc) on the server and create two computer groups under the Computers -> All Computers section.
- Workstations
- Servers
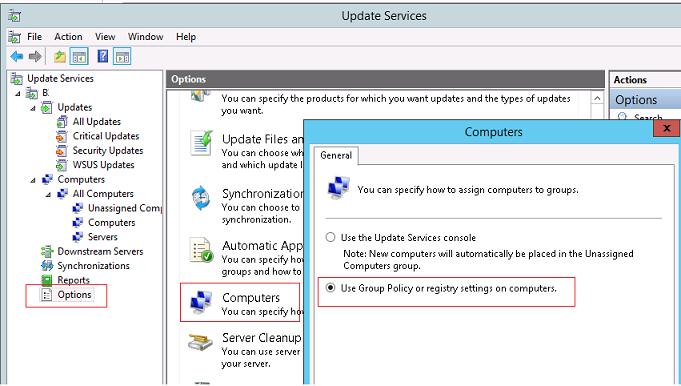
Then open the WSUS Options and in the Computers parameter, change the value to Use Group Policy or registry setting on computers.
Then open the Group Policy Management console (gpmc.msc) and create two new GPOs: ServerWSUSPolicy and WorkstationWSUSPolicy.
Let’s start with the description of the server update policy, named ServerWSUSPolicy.
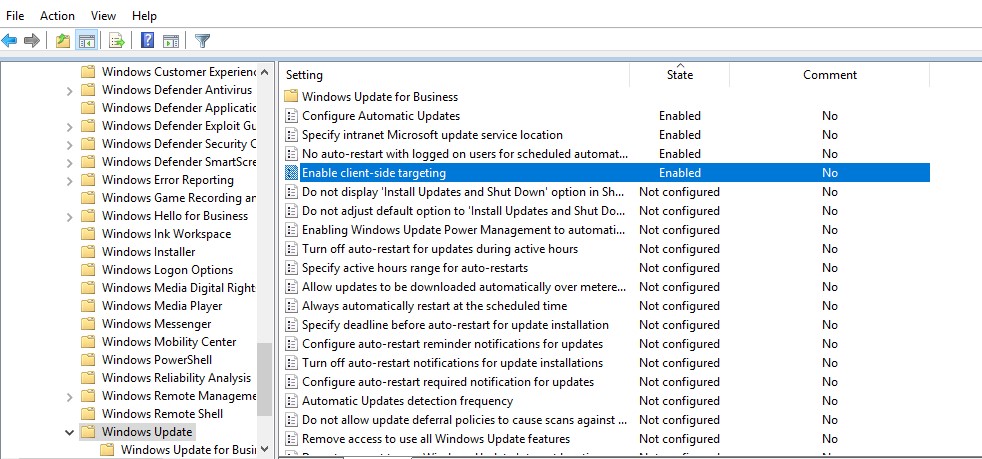
The settings for the Windows Update service are located in this GPO section: Computer Configuration -> Policies –> Administrative Templates -> Windows Component-> Windows Update.
The server update policy should prevent production servers from automatically installing updates or restarting without the administrator’s approval. Let’s configure the GPO so that the servers automatically download available updates, but do not install them. During scheduled maintenance windows, administrators can manually initiate the installation of updates (from the Settings app or using the PSWindowsUpdate module).
Configure the following policy options:
- Configure Automatic Updates:
Enable.3 – Auto download and notify for install– client automatically downloads new updates and notifies about them; - Specify Intranet Microsoft update service location:
Enable. Set the intranet update service for detecting updates:http://hq-wsus.woshub.com:8530, Set the intranet statistics server:http://hq-wsus.woshub.com:8530– set the address of the local WSUS server and the statistics server (they are usually the same) - No auto-restart with logged on users for scheduled automatic updates installations:
Enable– disable the automatic restart if there are active user sessions - Enable client-side targeting:
Enable. Target group name for this computer:Servers– assign clients to the Servers group in the WSUS console.
For workstations, we want to enable Windows Update to automatically download and install new updates as they become available. Users’ computers should be automatically rebooted (with user notification) after installing updates during non-working hours.
Configure the following settings in the WorkstationWSUSPolicy GPO:
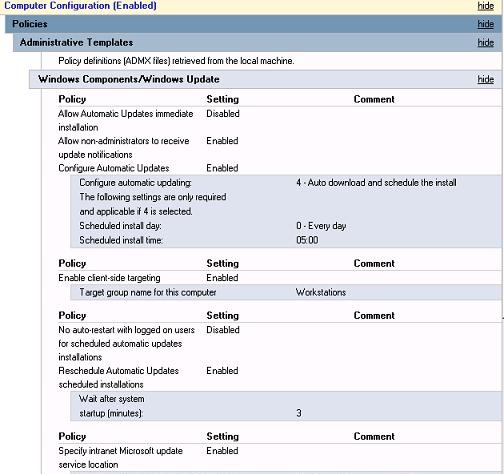
- Allow Automatic Updates immediate installation
Disabled—prevent updates from being installed as soon as they are received; - Allow non-administrators to receive update notifications
Enabled— show non-admin users a notification about new updates and allow manual installation; - Configure auto-restart reminder notifications for updates and Configure auto-restart warning notifications schedule for updates:
Enabled– display reboot notifications to users - Configure Automatic Updates:
Enabled. Configure automatic updating:4 — Auto download and schedule the install. Scheduled install day:0 — Every day. Scheduled install time:05:00AM– client downloads new updates and schedules them to install automatically at 5:00 am; - Enable client-side targeting:
Workstations– this will assign the client to the Workstations group in the WSUS console; - No auto-restart with logged on users for scheduled automatic update installations:
Disabled - Specify Intranet Microsoft update service location:
Enabled. Set the intranet update service for detecting updates:http://hq-wsus.woshub.com:8530, Set the intranet statistics server:http://hq-wsus.woshub.com:8530</emcode– is the address of the internal WSUS server. - Enable Do not allow update deferral policies to cause scans against Windows Update (so-called Dual Scan) and Do not connect to any Windows Update Internet locations. This prevents the client from contacting Windows Update servers on the Internet.
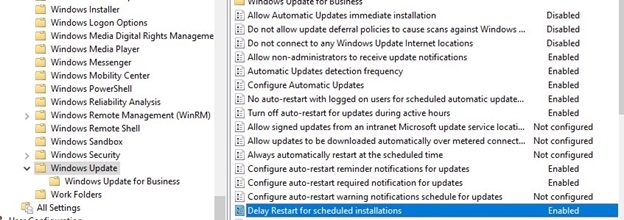
- Turn off auto-restart for updates during active hours –
EnabledDisable automatic restart after installing updates during working hours (set the working time interval in theActive Hours StartandActive Hours Endoptions. For example, from 8 AM to 5 PM
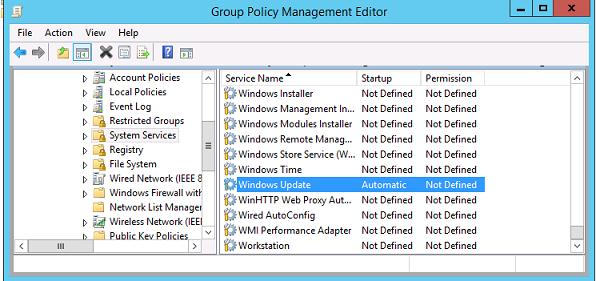
Force the Windows Update service (wuauserv) to start automatically on domain computers in both GPOs. To do this, go to Computer Configuration -> Policies-> Windows Settings -> Security Settings -> System Services, find the Windows Update service, and set it to start automatically.
Assign the Windows Update GPOs to the WSUS Clients
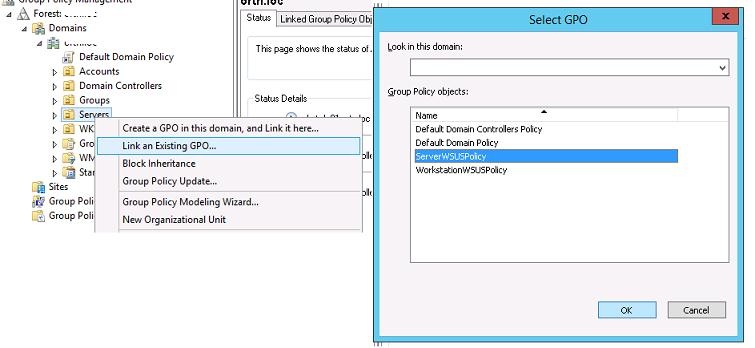
Then link the policies you have created to the appropriate containers (OUs) in the GPO management console (It is assumed that separate Organizational Units are created in AD for server and workstation objects).
In the Group Policy Management console, click on the required OU, select Link an Existing GPO, and select ServerWSUSpolicy.
Similarly, assign the Workstation Update policy to the OU containing the users’ computers.
Applying Windows Update Group Policy to Client Computers
Wait for the new GPO settings to be applied to the clients, or update them manually:
gpupdate /force
To force the clients to check in and report their status to the WSUS server, run:
$updateSession = new-object -com "Microsoft.Update.Session"; $updates=$updateSession.CreateupdateSearcher().Search($criteria).Updates
wuauclt /reportnow
wuauclt /detectnow /resetAuthorization
Completely reset the Windows Update agent settings on a computer.
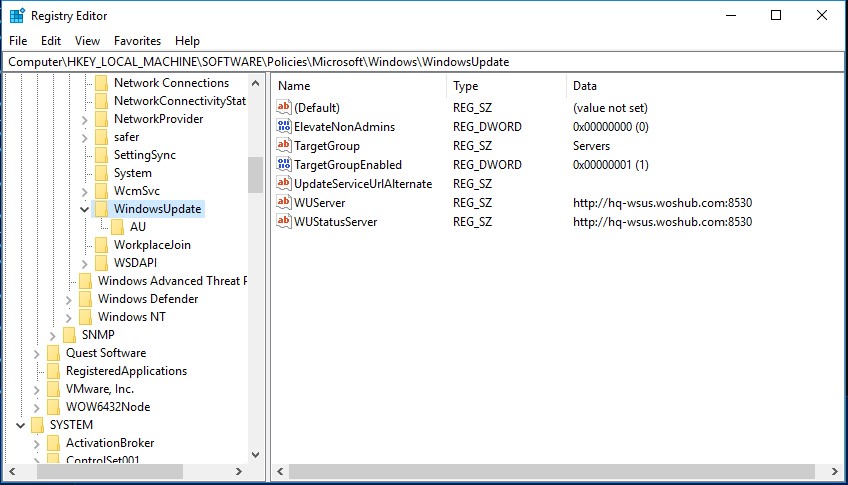
Any Windows Update settings set through Group Policy should appear on the client in the registry key HKLM\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate. This reg key can be exported to a REG file and used to apply WSUS update settings to other computers that cannot be configured via GPO (computers in workgroups, isolated segments, DMZ, etc.)
Windows Registry Editor Version 5.00
[HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate]
"WUServer"="http://hq-wsus.woshub.com:8530"
"WUStatusServer"="http://hq-wsus.woshub.com:8530"
"UpdateServiceUrlAlternate"=""
"TargetGroupEnabled"=dword:00000001
"TargetGroup"="Servers"
"ElevateNonAdmins"=dword:00000000
[HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate\AU]
"NoAutoUpdate"=dword:00000000 –
"AUOptions"=dword:00000003
"ScheduledInstallDay"=dword:00000000
"ScheduledInstallTime"=dword:00000003
"ScheduledInstallEveryWeek"=dword:00000001
"UseWUServer"=dword:00000001
"NoAutoRebootWithLoggedOnUsers"=dword:00000001
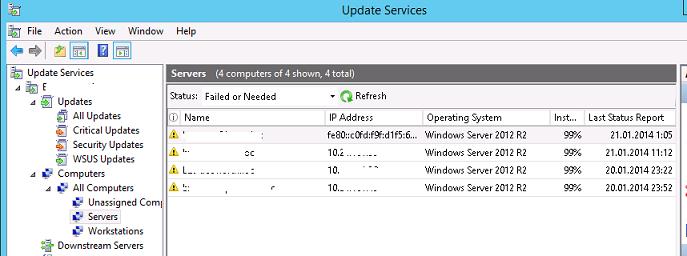
After a while, clients will appear in their assigned computer groups in the WSUS console. Here you can see computer names, IP addresses, OS versions, the percentage of assigned patches they have installed, and the date of the last scan.
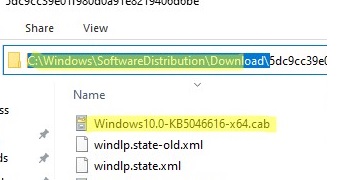
Client computers download the CAB update files to the %windir%\SoftwareDistribution\Download directory. The WindowsUpdate.log files provide detailed logs of how the client scans for updates against WSUS, downloads, and installs them.
Configure Clients to Receive Updates from the Internet via GPO
Suppose you don’t have an intranet WSUS server. In that case, you can use the GPO settings discussed above to configure the settings for automatically receiving and installing updates on client computers from the Internet (from Windows Update servers).
In this case, set any GPO parameters that set receiving updates from WSUS to Not Configured:
- Specify Intranet Microsoft update service location:
Not Configured - Target group name for this computer:
Not Configured - Do not allow update deferral policies to cause scans against Windows Update:
Disabled - Do not connect to any Windows Update Internet locations:
Disabled
These GPO settings control how your domain computers download and install Windows updates from Microsoft Internet Update servers.
5 comments
What are the configuration need to be done on WSUS server, like Pre-approved / Auto Approve updates.
If we don’t approve update on WSUS will it get downloaded on clientt machine?
hello.
i am trying your solution, but when i run the powershell command: get-windowsupdatelog.
the clients are getting the correct target group. but the servers goes to the unassigned computers group.
how come?
Check the following:
1) The option “Use Group Policy or registry settings on computers” should be enabled in the WSUS settings,
2) Check the resulting Group Policy settings on the client using
rsop.msc. Make sure that the GPO sets the value for the “Target group name for this computer” parameter on the client. If not, check why your GPO is not applied (https://woshub.com/group-policy-not-applied-troubleshooting/)how to work in the subgroups to implement the policies
I have the following structure
canada —> information_technology —> infrastructure
but if I apply policies to the two subgroups information_technology and infrastructure I only see the information_technology equipment the infrastructure equipment is grouped in unassigned computers.
If I delete or disable the information_technology gpo then I see the computers in infrastructure but for obvious reasons to be disabled the gpo in information_technology no longer show computers.
Translated with DeepL.com (free version)
Changing the GPO priority (Link processing order) in the Infrastructure OU can fix this.
The GPO with the lowest link order will be processed last. This should be the Infrastructure GPO in your case.