Most Windows administrators, who are familiar with PKI, know about the MakeCert.exetool, which allows to create self-signed certificates. This tool is part of the Microsoft .NET Framework SDK and Microsoft Windows SDK. You can create a self-signed certificate using the built-in PowerShell cmdlet New-SelfSignedCertificate without using additional tools.
- New-SelfSignedCertificate: Creating a Self-Signed Certificate with PowerShell
- Create a Certificate with the Subject Alternative Name (SAN) Using PowerShell
- How to Export a Self-Signed Certificate on Windows?
- Generating a Self-Signed Certificate for Code Signing on Windows
- Creating SHA-256 Self-Signed SSL Certificate in IIS on Windows Server
New-SelfSignedCertificate: Creating a Self-Signed Certificate with PowerShell
To create a self-signed certificate with PowerShell, you can use the built-in New-SelfSignedCertificate cmdlet, which is a part of the PowerShell PKI (Public Key Infrastructure) module:
To list all available cmdlets in the PKI module, run the command:
Get-Command -Module PKI
It is recommended to use self-signed certificates for testing/developing tasks or to provide certificates for internal Intranet services (IIS, Exchange, Web Application Proxy, LDAPS, ADRMS, DirectAccess, etc.) if you cannot deploy PKI/CA infrastructure or purchase a trusted certificate from an external provider.
To create a certificate, you have to specify the values of –DnsName (name of a server, the name may be arbitrary and even different from the current hostname) and -CertStoreLocation (a local certificate store in which the generated certificate will be placed).
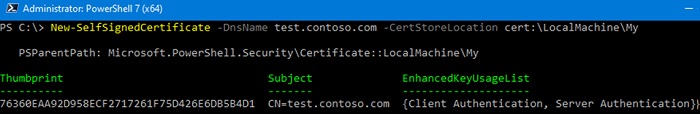
To create a new SSL certificate (with the default SSLServerAuthentication type) for the DNS name test.contoso.com (use an FQDN name) and place it to the personal certificates on a computer, run the following command:
New-SelfSignedCertificate -DnsName test.contoso.com -CertStoreLocation cert:\LocalMachine\My
The command will return the Thumbprint, Subject, and EnhancedKeyUsageList of the new certificate. By default, such a certificate can be used for Client Authentication (1.3.6.1.5.5.7.3.2) or Server Authentication (1.3.6.1.5.5.7.3.1).
New-SelfSignedCertificate : CertEnroll::CX509Enrollment::_CreateRequest: Access denied. 0x80090010 (-2146893808 NTE_PERM)
If you have specified a non-standard cryptographic provider (CSP) ( for example, using the -KeyAlgorithm "ECDSA_secP256r1" -Provider "Microsoft Smart Card Key Storage Provider"parameters), make sure it is installed on your computer (the default is Microsoft Enhanced Cryptographic Provider). Otherwise, an error will appear:
New-SelfSignedCertificate: CertEnroll::CX509Enrollment::_CreateRequest: Provider type not defined. 0x80090017 (-2146893801 NTE_PROV_TYPE_NOT_DEF).
By default, a self-signed certificate is generated with the following settings:
- Cryptographic algorithm: RSA;
- Key length: 2048 bit;
- Acceptable key usage: Client Authentication and Server Authentication;
- The certificate can be used for: Digital Signature, Key Encipherment;
- Certificate validity period: 1 year;
- Crypto provider: Microsoft Software Key Storage Provider.
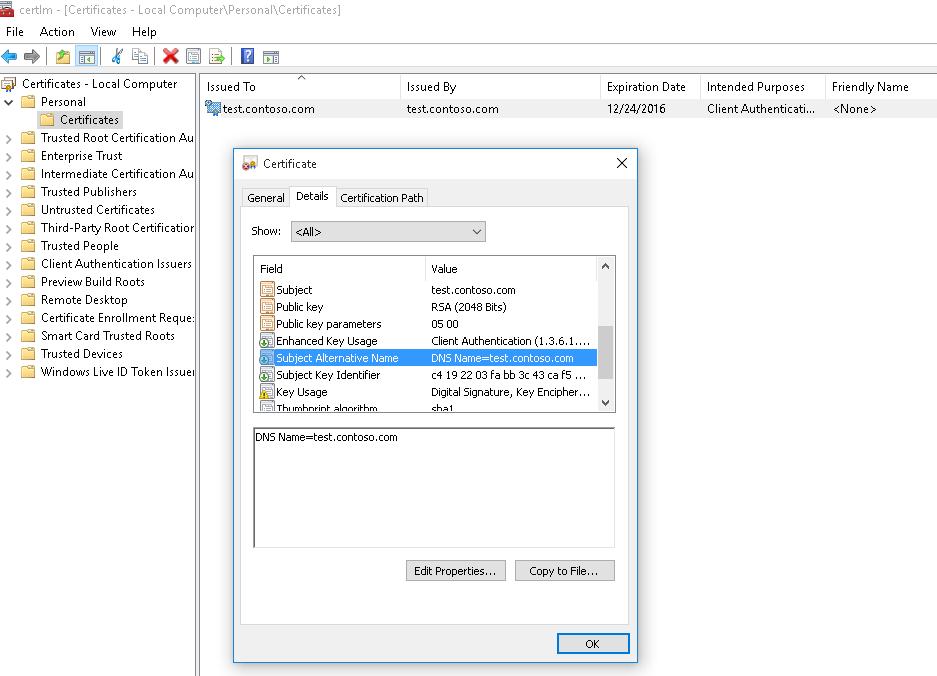
This command creates a new certificate and imports it into the computer’s personal certificate store. Open the certlm.msc MMC snap-in and make sure that a new certificate appears in the Personal section of the computer’s certificate store.
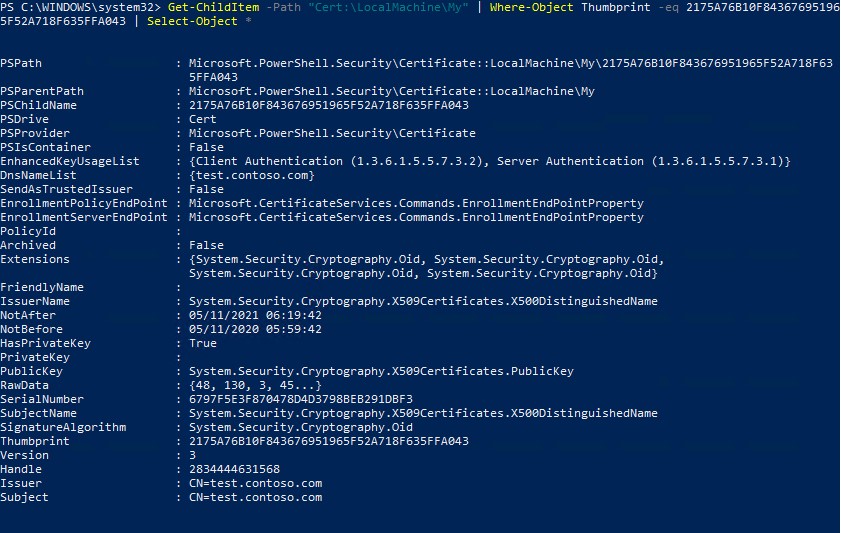
Using the Get-ChildItem cmdlet, you can display all the parameters of the created certificate by its Thumbprint:
Get-ChildItem -Path "Cert:\LocalMachine\My" | Where-Object Thumbprint -eq 2175A76B10F843676951965F52A718F635FFA043 | Select-Object *
PSPath : Microsoft.PowerShell.Security\Certificate::LocalMachine\My\2175A76B10F843676951965F52A718F635FFA043
PSParentPath : Microsoft.PowerShell.Security\Certificate::LocalMachine\My
PSChildName : 2175A76B10F843676951965F52A718F635FFA043
PSDrive : Cert
PSProvider : Microsoft.PowerShell.Security\Certificate
PSIsContainer : False
EnhancedKeyUsageList : {Client Authentication (1.3.6.1.5.5.7.3.2), Server Authentication (1.3.6.1.5.5.7.3.1)}
DnsNameList : {test.contoso.com}
SendAsTrustedIssuer : False
EnrollmentPolicyEndPoint : Microsoft.CertificateServices.Commands.EnrollmentEndPointProperty
EnrollmentServerEndPoint : Microsoft.CertificateServices.Commands.EnrollmentEndPointProperty
PolicyId :
Archived : False
Extensions : {System.Security.Cryptography.Oid, System.Security.Cryptography.Oid,
System.Security.Cryptography.Oid, System.Security.Cryptography.Oid}
FriendlyName :
IssuerName : System.Security.Cryptography.X509Certificates.X500DistinguishedName
NotAfter : 12/4/2023 5:35:15 PM
NotBefore : 12/4/2022 5:15:15 PM
HasPrivateKey : True
PrivateKey :
PublicKey : System.Security.Cryptography.X509Certificates.PublicKey
RawData : {48, 130, 3, 45...}
SerialNumber : 6797F5E3F870478D4D3798BEB291DBF3
SubjectName : System.Security.Cryptography.X509Certificates.X500DistinguishedName
SignatureAlgorithm : System.Security.Cryptography.Oid
Thumbprint : 2175A76B10F843676951965F52A718F635FFA043
Version : 3
Handle : 2834444631568
Issuer : CN=test.contoso.com
Subject : CN=test.contoso.com
$todaydt = Get-Date
$3years = $todaydt.AddYears(3)
New-SelfSignedCertificate -dnsname test.contoso.com -notafter $3years -CertStoreLocation cert:\LocalMachine\My
You can create a certificate chain. First, a root certificate (CA) is created. Then based on it, an SSL server certificate is generated:
$rootCert = New-SelfSignedCertificate -Subject 'CN=TestRootCA,O=TestRootCA,OU=TestRootCA' -KeyExportPolicy Exportable -KeyUsage CertSign,CRLSign,DigitalSignature -KeyLength 2048 -KeyUsageProperty All -KeyAlgorithm 'RSA' -HashAlgorithm 'SHA256' -Provider 'Microsoft Enhanced RSA and AES Cryptographic Provider'
New-SelfSignedCertificate -CertStoreLocation cert:\LocalMachine\My -DnsName "test2.contoso.com" -Signer $rootCert -KeyUsage KeyEncipherment,DigitalSignature
To change the certificate key length and encryption algorithm, you need to use the -KeyAlgorithm, -KeyLength, and -HashAlgorithm options. For example:
New-SelfSignedCertificate -KeyAlgorithm RSA -KeyLength 2048 -HashAlgorithm "SHA256" …
The Microsoft Platform Crypto Provider allows you to use the device’s Trusted Platform Module chip (TPM 2.0) to protect the key.
New-SelfSignedCertificate -Type Custom -Provider "Microsoft Platform Crypto Provider" ...
You can generate a document encryption certificate to protect your document and email. Use the DocumentEncryptionCert type when creating a cert:
$Params = @{
"DnsName" = "myhostname"
"CertStoreLocation" = "Cert:\\CurrentUser\\My"
"KeyUsage" = "KeyEncipherment","DataEncipherment","KeyAgreement"
"Type" = "DocumentEncryptionCert"
}
$doccert=New-SelfSignedCertificate @Params
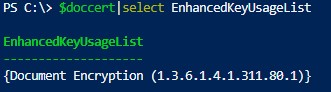
Check the certificate EnhancedKeyUsageList value:
$doccert|select EnhancedKeyUsageList
{Document Encryption (1.3.6.1.4.1.311.80.1)}Create a Certificate with the Subject Alternative Name (SAN) Using PowerShell
The New-SelfSignedCertificate cmdlet allows you to create a certificate with several different Subject Alternative Names (SANs).
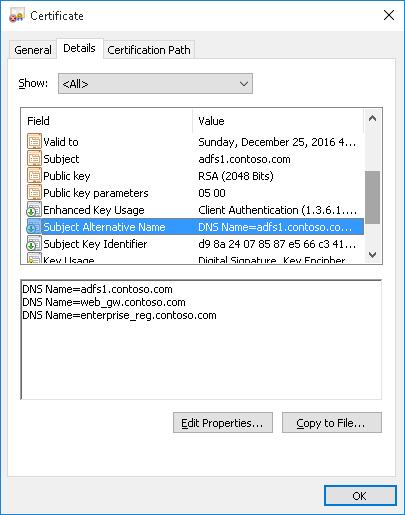
Makecert.exetool, unlike the New-SelfSignedCertificate cmdlet, cannot create SAN and Wildcard certificates.[/alert]If you want to create a certificate with multiple names, the first name of the DnsName parameter will be used as the CN (Common Name) of the certificate. For example, let’s create a self-signed SAN certificate with the following names:
- Subject Name (CN):
adfs1.contoso.com - Subject Alternative Name (DNS):
web_gw.contoso.com - Subject Alternative Name (DNS):
enterprise_reg.contoso.com
You can the following command to generate a certificate with different common names (or even for multiple domains):
New-SelfSignedCertificate -DnsName adfs1.contoso.com,web_gw.contoso.com,enterprise_reg.contoso.com -CertStoreLocation cert:\LocalMachine\My
Also, you can generate a wildcard certificate for the entire domain namespace by specifying *.contoso.com as the server name.
New-SelfSignedCertificate -certstorelocation cert:\localmachine\my -dnsname *.contoso.com
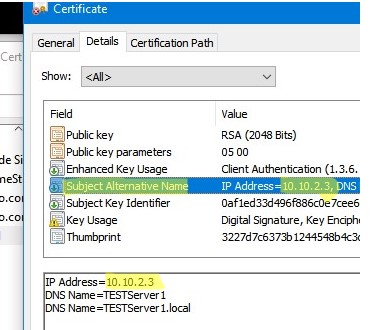
You can generate a self-signed certificate not only for a DNS hostname but also for an IP address. To do this, you need to use -TextExtension instead of the -DnsName parameter. For example:
New-SelfSignedCertificate -TextExtension @("2.5.29.17={text}IPAddress=10.1.2.3&DNS=TESTServer1&DNS=TESTServer1.local")
As you can see, the Subject Alternative Name field now contains the IP address of the host and its DNS names.
How to Export a Self-Signed Certificate on Windows?
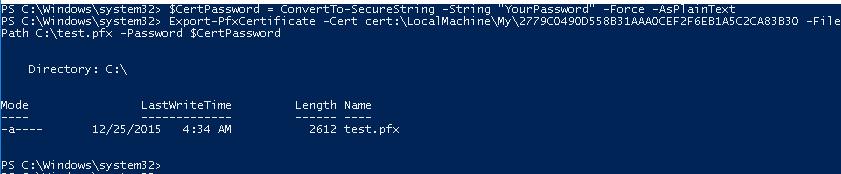
To export the generated certificate with a private key to a password-protected PFX file, you need to specify its Thumbprint. It can be copied from the results of the New-SelfSignedCertificate command. You also need to specify the certificate’s security password and convert it to a SecureString format:
$CertPassword = ConvertTo-SecureString -String “YourPassword” -Force –AsPlainText
Export-PfxCertificate -Cert cert:\LocalMachine\My\2779C7928D055B21AAA0Cfe2F6BE1A5C2CA83B30 -FilePath C:\test.pfx -Password $CertPassword
You can export the certificate public key as follows (the private key is not included in the export):
Export-Certificate -Cert Cert:\LocalMachine\My\2779C7928D055B21AAA0Cfe2F6BE1A5C2CA83B30 -FilePath C:\tstcert.cer
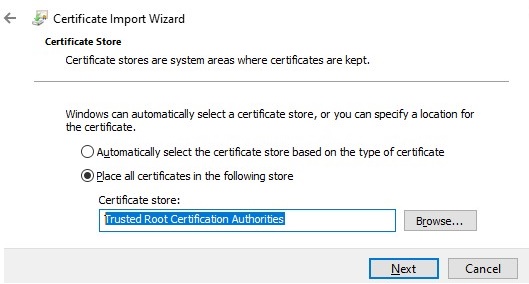
Make sure the *.CER (PFX) certificate file appears in the specified directory. If you right-click it and select the “Install Certificate” menu item, you can use the Certificate Import Wizard to add the certificate to the trusted root certificates on your computer.
Select Cert Store location -> Local Machine, Place all certificates in the following store -> Trusted Root Certification Authorities.
[alert]You can create a certificate and immediately import it into the Trusted Root Certificate store of the computer using the commands:
$SelfSignCert=New-SelfSignedCertificate …..
$certFile = Export-Certificate -Cert $SelfSignCert -FilePath C:\ps\export-certname.cer
Import-Certificate -CertStoreLocation Cert:\LocalMachine\AuthRoot -FilePath $certFile.FullName
You can deploy this public key or the certificate file itself on all user computers and servers in the Active Directory domain using GPO (How to deploy certificates to users with GPO?).
Generating a Self-Signed Certificate for Code Signing on Windows
In PowerShell 3.0, the New-SelfSifgnedCertificate cmdlet only generates SSL certificates which cannot be used to sign the driver code, application, or script (unlike the certificates generated by the MakeCert utility).
You can use the New-SelfSifgnedCertificate cmdlet to issue Code Signing certificates in PowerShell version 5.0 and newer.
To create a self-signed certificate for sign application code, run the command:
$cert = New-SelfSignedCertificate -Subject "My Code Signing Certificate” -Type CodeSigningCert -CertStoreLocation cert:\LocalMachine\My
Now you can sign your PowerShell script file with a self-signed certificate:
Set-AuthenticodeSignature -FilePath C:\PS\my_posh_script.ps1 -Certificate $cert
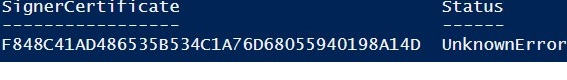
If you are receiving an UnknownError warning when executing the command, this means that the certificate is not trusted, because it is located in the user’s personal certificates store.
You need to move it to the Trusted Root Certificate store (don’t forget to periodically scan the Windows certificate root store for untrusted and suspicious certificates and update the lists of trusted root certificates).
Move-Item -Path $cert.PSPath -Destination "Cert:\CurrentUser\Root"
Now you can use this self-signed certificate to sign your PowerShell scripts, drivers, or applications.
Creating SHA-256 Self-Signed SSL Certificate in IIS on Windows Server
Please note that when creating a self-signed certificate for IIS through the Internet Information Manager console (using Create Self-Signed Certificate action menu item), an SSL certificate is created using the SHA-1 encryption algorithm. Such certificates are considered untrusted by many browsers and cannot be used to establish a secure connection (or you may see other SSL warnings and errors). The New-SelfSignedCertificate cmdlet allows you to create a more popular type of certificate using the SHA-256 encryption algorithm.
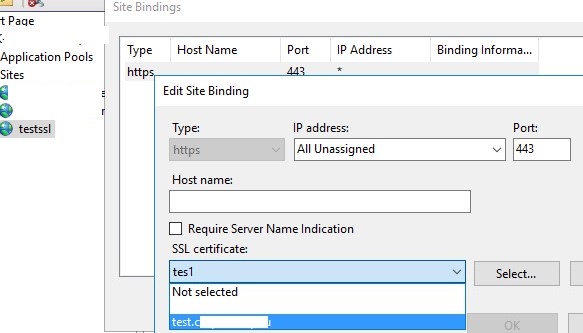
You can bind a self-signed SHA-256 certificate generated with PowerShell to an IIS site on Windows Server. If you create an SSL certificate using PowerShell and place it in the computer’s certificate store, it will automatically be available to IIS sites.
Open the IIS Manager console (inetmgr.exe), select your site, and then select the certificate you created in the Site Binding options. Save your changes.
You can also bind an SSL certificate by its thumbprint to an IIS site:
New-IISSiteBinding -Name "Default Web Site" -BindingInformation "*:443:" -CertificateThumbPrint $yourCert.Thumbprint -CertStoreLocation "Cert:\LocalMachine\My" -Protocol https
11 comments
Hi.
One sentence is not clear:
Note. Unlike MakeCert, New-SelfSifgnedCertificate cmdlet allows to issue only an SSL certificate, which can not be used to sign a driver or an application code.
————————————————
Does this mean that if we are interested in code-signing, that PowerShell cannot be used to generate a certificate?
This is a mistake. New-SelfSignedCertificate cmdlet also can create a code-signing cert this way:
New-SelfSignedCertificate -DnsName dev1.contoso.com -Type CodeSigning
I have been unable to use the New-SelfSignedCertificate cmdlet to create a code-signing cert that can be used to sign Powershell scripts. Whenever I attempt to sign a PS script with my cert using Set-AuthenticodeSignature, it displays Status of UnknownError. However, the certs that I create using makecert work just fine. Has anyone ever attempted to sign a PS script with a cert created by New-SelfSignedCertificate?
Create a new selfsignet cert for code signing:
New-SelfSignedCertificate -DnsName dub-srv1 -Type CodeSigningAdd this cert to Trusted Root section of certmgr.msc console and sign your PS script using this cert:
Set-AuthenticodeSignature C:\Script\yourscript.ps1 @(gci Cert:\LocalMachine\My -DnsName dub-srv1 -codesigning)[0]I support enterprise level web-based applications Here’s what I use to create self-signed certificates on my virtual systems:
Windows 10 or Windows Server 2016
$cert=New-SelfSignedCertificate -DnsName *.TestDomainName.org,$env:COMPUTERNAME -CertStoreLocation Cert:\LocalMachine\My -NotAfter (Get-Date).AddYears(10) -FriendlyName WjhTestCert
$certFile = Export-Certificate -Cert $cert -FilePath C:\WjhTestCert.cer
Import-Certificate -CertStoreLocation Cert:\LocalMachine\AuthRoot -FilePath $certFile.FullName
Remove-Item $certFile.FullName
$ips = [System.Net.Dns]::GetHostAddresses(”).IPAddressToString -like ‘*.*’
Add-Content C:\Windows\System32\drivers\etc\hosts ” $ips *.TestDomainName.org”
Windows Server 2012 R2
$cert = New-SelfSignedCertificate -DnsName *.TestDomainName.org,$env:COMPUTERNAME -CertStoreLocation Cert:\LocalMachine\My
$certFile = Export-Certificate -Cert $cert -FilePath C:\WjhTestCert.cer
Import-Certificate -CertStoreLocation Cert:\LocalMachine\AuthRoot -FilePath $certFile.FullName
Remove-Item $certFile.FullName
$ips = [System.Net.Dns]::GetHostAddresses(”).IPAddressToString -like ‘*.*’
Add-Content C:\Windows\System32\drivers\etc\hosts ” $ips *.TestDomainName.org”
“New-SelfSignedCertificate -DnsName test.contoso.com -CertStoreLocation cert:\LocalMachine\My”
Worked for me with an elevated Powershell.
Thank you for posting this.
I’m a novice and spent many hours googling on how to create a simple IIS 10 test certificate. I ran the second PowerSheel command from this tutorial and I’ve got it in 10 seconds! Thanks a million.
Thank for your excellent tutorial. I am using this Cert to test VPN SSTP on Server 2008, so, I have some “rookie” questions for you. I used to create Self-Signed Certificate using SelfSSL7 tool, but this tool is obsolete (Sha1), so, I prefer to use a better option with Sha256. I have created a Self-Signed Certificate using your PowerShell steps successfully, but I have noticed two things that worries me:
a) the “Key Usage” has a yellow alert and it support only “Digital Signature and Key Encipherment”, but it does not include “Data Encipherment” as SelfSSL7 tool includes.
b) PowerShell Cert includes Client and Server authentication, and SelfSSL7 only includes Server authentication, so, I am not 100% sure if there is a PowerShell command to build the Self-Signed only for Server authentication. I know how to use uncheck in the Cert Client authentication, I just wondering if I can build the cert without the Client part, many thanks.
My powershell certs always seem to be created as 1024 bit. Tried specifying 2048 and still no luck any ideas?
can you specify specific template when issuing a new-selfsigned cert
it’s probably a stupid question but is it possible to choose the thumbprint of a certificate or change it to be a specific thumbprint?