When connecting to a shared network printer, users may receive a ‘Windows can’t connect to the printer’ error with codes 0x0000011b or 0x00000002. This post explains common ways to fix shared printer connection errors in Windows.
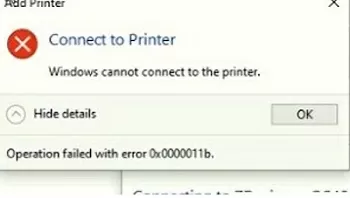
Error 0x0000011b: Windows Cannot Connect to the Printer
In 2021, Microsoft released a series of security patches to fix the PrintNightmare vulnerability in the Print Spooler service. After installing these updates, Windows users may receive error 0x0000011b when connecting shared network printers.
Connect to Printer Windows cannot connect to the printer. Operation failed with error 0x0000011b.
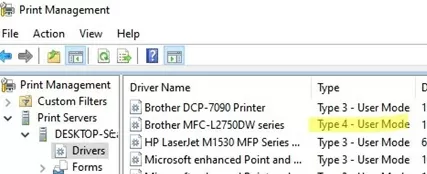
Microsoft recommends using only Type 4 User Mode printer drivers on the print server. (the computer sharing the printer). These drivers do not require client-side administrative permissions to install. Update your printer drivers to Type 4.
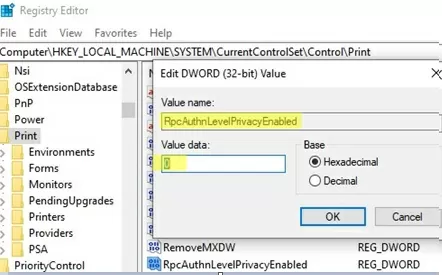
If only Type 3 drivers are available for your printer, you can reduce the security level on the print server by creating the RpcAuthnLevelPrivacyEnabled registry entry with a value of 0:
REG ADD "HKLM\System\CurrentControlSet\Control\Print" /v RpcAuthnLevelPrivacyEnabled /t REG_DWORD /d 0 /f
Restart the print spooler service on a host computer:
Restart-Service Spooler -Force
Then try connecting the shared network printer on the client computer again.
After connecting the shared printer to the client, set RpcAuthnLevelPrivacyEnabled =1 on the server to protect against the vulnerability.
reg add "HKLM\Software\Policies\Microsoft\Windows NT\Printers\PointAndPrint" /v RestrictDriverInstallationToAdministrators /t REG_DWORD /d 0 /f
Set RestrictDriverInstallationToAdministrators back to 1 after connecting the shared printer.
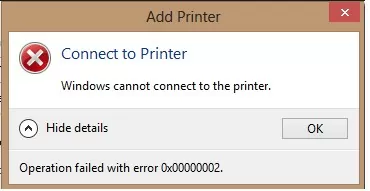
0x00000002: Unable to Connect Shared Printer, Operation Failed
0x00000002 is another common shared printer connection error. This error can occur when you trying to connect a shared printer using a UNC path (using the format \\computername).
Connect to Printer Windows cannot connect to the printer. Operation failed with error 0x00000002.
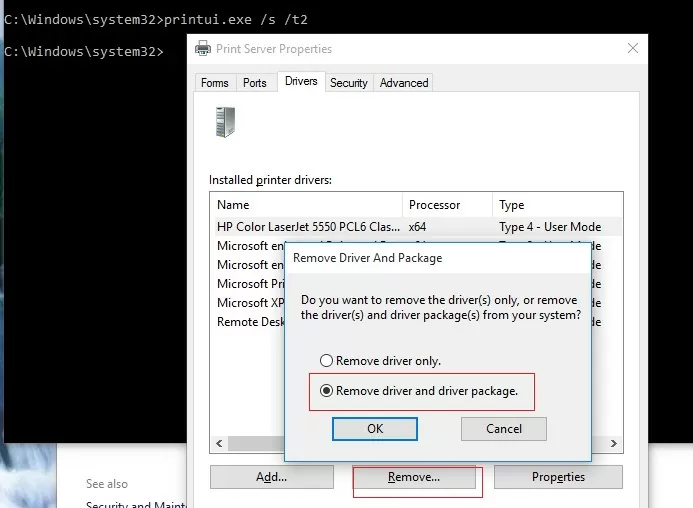
Error 0x00000002 usually indicates that the driver installed on the computer for this printer is corrupt. Remove this driver from the driver store. Open the list of installed printer drivers:
printui.exe /s /t2
Find the printer driver you are trying to install and remove it (Remove -> Remove driver and driver package).
Remove-PrinterDriver -Name "HP Universal Printing PCL 5"
If any printers use this driver, you will also need to remove such printers first.
Restart the spooler (net stop spooler & net start spooler) and try connecting your shared printer again.
If the printer connection error occurs again, delete the old driver entries from the registry:
Otherwise, try the following:
- Run the regiedit.exe and remove the registry key: HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager\PendingFileRenameOperations;
- If there are any subfolders with names from 1 to 499 in
c:\Windows\System32\spool\prtprocs\x64, directory, delete all of them except winprint.dll; - Delete all Print Processors and drivers (except winprint) from the reg key HKLM\SYSTEM\CurrentControlSet\Control\Print\Environments;
- Restart your computer and connect to the shared printer.
Connect a Shared Printer via a Local Port Using the UNC Name
A workaround for most shared printer connection errors is to try connecting the printer using a local port with a UNC path.
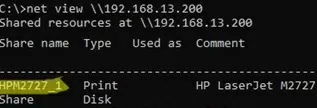
To do this, you need to know the UNC name of the shared printer. Open a command prompt and list the shared printers on the remote computer using the command:
net view \\192.168.13.200
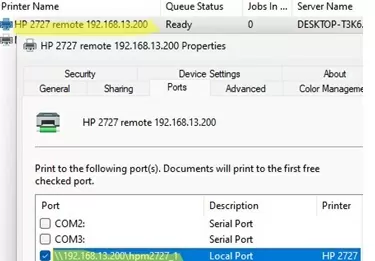
In this example, the shared printer’s UNC name is \\192.168.13.200\HPM2727_1 (instead of the IP address, you can use the computer name).
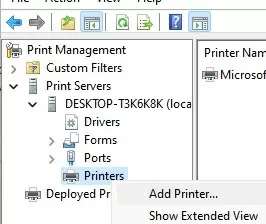
Install the Printer Management snap-in in Windows:
dism /Online /add-Capability /CapabilityName:Print.Management.Console~~~~0.0.1.0
Open the print management console (printmanagement.msc) and navigate to Print Servers -> Printers. Create a new printer.
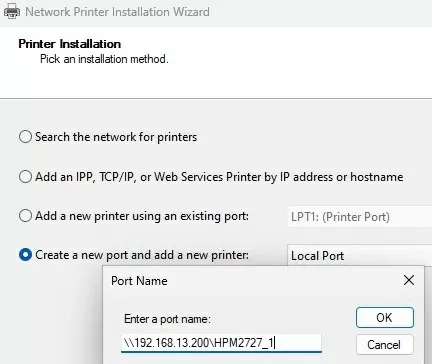
Select Local Port as the port type and enter the UNC path to the shared printer as the port name..
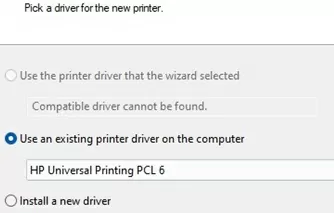
Continue installation. Select (or install) a printer driver.
Set the printer’s name.
Check you can print to a shared remote printer.
41 comments
thanks it’s done
thanks a lot
done
is this command removes the driver from the localhost or from the print server?
This command is applied on your computer (localhost).
Simple and efective. Job done
Thanks!! Finally!
Similar issue in Active Directory domain
Print server windows 2016 Core, Windows 10 clients
Printers can’t be connected, set as default or installed on client computers
Removing KB5005573 from print server solved the 0x0000011b problem.
I have a shared printer on Win 10 PC and Win 10 laptop. All was fine until I installed this latest Windows update on PC.
Then I try to print a test page it gives me a 0x0000011b error on laptop. Printing from the local desktop works fine.
I same error on Win 10, then Uninstall KB5005565, it’s ok now
If you deploy printers via GPO to the computers rather than the user, it works as the computer policy installs the print driver with SYSTEM permissions.
There are three updates released recently KB5005565, KB5005613, KB5005627, and KB5005563. They are addressed to correct an exploit vulnerability in printer driver injection (called PrintNightmare)
Thank you very much, my problem (Error 0x0000011b) solved.
I have a shared printer on Win 10 PC and Win 10 laptop. All was fine until I installed this latest Windows update on PC.
Then I try to print a test page it gives me a 0x0000011b error on the laptop. Printing from the local desktop works fine.
You can add the following registry parameter on the print server in order not to remove the latest security updates:
[HKEY_LOCAL_MACHINE\System\CurrentControlSet\Control\Print]
“RpcAuthnLevelPrivacyEnabled”=dword:00000000
Do we need to reboot the print server after adding the following regkey on it?
[HKEY_LOCAL_MACHINE\System\CurrentControlSet\Control\Print]
“RpcAuthnLevelPrivacyEnabled”=dword:00000000
most likely yes
Thank you so much for all your great tutorials learning a lot
KB5006670 caused the same issue— uninstalled and it worked like charm.. thanks for sharing this valuable info.
Thanks Romeo It worked for Me Also.
Have a Print Server with 2016 and it has the latest patches as of today and don’t see the patches mentioned above to be removed. Have they removed them and replaced with newer patches causing the same problems such as requesting Admin credentials?
Microsoft has added these changes in the next security update.
You will have to either uninstall the updates, or permanently enable the registry setting parameter RestrictDriverInstallationToAdministrators = 0
reg add "HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows NT\Printers\PointAndPrint" /v RestrictDriverInstallationToAdministrators /t REG_DWORD /d 0 /fSo far, only these two workarounds are known.
Hi – I a so pleased to have found this thread – thought I was going mad! I have a similar problem though a different Error number.
Setup is Win 7 Ultimate on a PC usb connection to Printer (Aged Brother DCP135C)
This works well. I also have a laptop with Win 10 (Enterprise N) This connects via wifi to the PC and after a few problems initially has been ok. Have had full access to files between the PC and laptop ( both ways) (This still works)
Since the recent Win 10 update I have been unable to send a print instruction from the laptop even though it can see the printer and appears to be connected.
The Printer troubleshooter finds no problems!!
When I try to print a test page however I get :
“Operation could not be completed (error 0x0000003a). The specified server cannot perform the requested operation.”
Trying to print from notepad or a pdf produces a similar message. This particular error number is not mentioned in this thread and am wondering if the fixes mentioned would work. I am not used to doing registry edits so dont want to mess it up even more.
Have tried restarting both machines and running sfc scannow on both. Am I correct in assuming I would make any changes on the laptop running Win 10
That’s right, you need to make changes on your Windows 10 host
Thanks- decided against making any changes and just uninstalled update KB5006670.
Printer now working again. Just need to stop it re installing it again LOL
Getting this error here:
windows cannot connect to the printer 0x000006e4
Have you tried anything to fix it? – are you using win10? if so is it just since the 6670 update? and if it is
have you tried uniinstallling the update?
Yea, uninstalled everything on the server end. Still working on client. So far no luck.
i can’t print now from shared printer. when i try to print print getting hang, keep on rounding. is it because of update installation . pls help me
As my reply above + do you just have 1 printer shared with 2 PCs – does it print from the other one?
NO, ITS NOT PRINTING FROM ANY PCY WHEN TRY TO PRINT ITS GET HANG
Is this a home setup or business- Is the printer connected to one pc with USB – on that pc can you do a test print?
Tried switching the printer off and on?
If you have not already – uninstall the last win10 update. If that corrects it you then need to “hide” it so it
doesnt reload. If it doesnt correct it then the problem lies elsewhere so you can re install it.
my pc is unable to connect to USB (not a network printer) shared printer.
“windows could not connect to the printer error 0x00000709”
please suggest the solution
Re Recent update
After installing this update, Windows print clients might encounter the following errors when connecting to a remote printer shared on a Windows print server:
0x000006e4 (RPC_S_CANNOT_SUPPORT)
0x0000007c (ERROR_INVALID_LEVEL)
0x00000709 (ERROR_INVALID_PRINTER_NAME)
Note The printer connection issues described in this issue are specific to print servers and are not commonly observed in devices designed for home use. Printing environments affected by this issue are more commonly found in enterprises and organizations.
For workarounds and the latest status for this issue, please see Windows release health:
OS Build 19041.1288
OS Build 19042.1288
OS Build 19043.1288
We are presently investigating and will provide an update in an upcoming release.
printer USB share problem.
For the record, setting the HKEY_LOCAL_MACHINE\System\CurrentControlSet\Control\Print\RpcAuthnLevelPrivacyEnabled registry key to 0 on the print server and then rebooting it solved the issue for me as well. Thank you so much for your assistance.
Error then connecting shared printer:
Connect to Printer
Windows cannot connect to the printer
Operation failed with error 0x00000057
This helped:
Remove printer driver:
printui.exe /s /t2
and re-install
Got an error:
Connect to Printer
A policy is in effect on your computer which prevents you from connecting to this print queue. Please contact your system administrator.
Check
1) if the driver is signed with the trusted digital signature
2) if the package-aware print driver installed (non-package-aware v3 printer drivers won’t be able to be installed in Point and Print Restrictions mode)
3) Deploy the certificate of the signing publisher to client computers: Local computer > Trusted publishers > Certificates
This way the driver can be installed because the publisher is trusted when using point and print.
In case an error:
Windows can’t open Add printer.
The local Print Spooler service is not running. Please restart the Spooler or restart the machine.
1) Enable auto start for the Print Spooler service;
2) On the Dependencies tab, verify that Print Spooler service depends on the following services: “Remote Procedure Control (RPC)” and “HTTP Service”. In order Print Spooler to work correctly, these services must be running. If the dependencies are not configured, you can restore them using the command: sc config spooler depend= RPCSS
In the line
After connecting the shared printer to the client, set RpcAuthnLevelPrivacyEnabled =0 on the server to protect against the vulnerability.
I believe you meant =1 on the server to protect against the vulnerability.
Certainly.
Fixed!
For me what worked was updating printer client win 10 to the last version of 22H2..