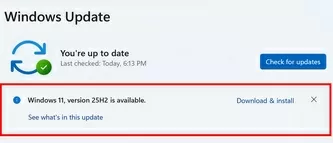
In addition to monthly security and cumulative updates for Windows, Microsoft releases major Feature Updates every six months (or annually), each of which is assigned a version (build) number (23H2, 24H2, 25H2). For example, “25H2” means this feature update was released in the second half of 2025. Windows Feature Updates are installed automatically on compatible user devices via Windows Update, with mass deployment occurring in waves to ensure a smooth rollout process.
If you don’t want the Feature Update to be installed on your computers, you can disable automatic upgrading to the next Windows builds.
Set Target Windows Feature Update Version (Build) to Stay On
To prevent automatic upgrades beyond a specific version, you can set the target Feature Update version (build number) for Windows on your computer. For example, if you set the target version for your computer to Windows 11 24H2, it will remain on that build until October 13, 2026, which is its end of service date. After the end-of-life date for the pinned Windows build, you must set a new target build; otherwise, Windows will automatically update to the latest available build within 60 days.
You can pin the target Windows build on your computer that you want to stay on or update to via GPO or through the registry:
- Open the Local Group Policy Editor (
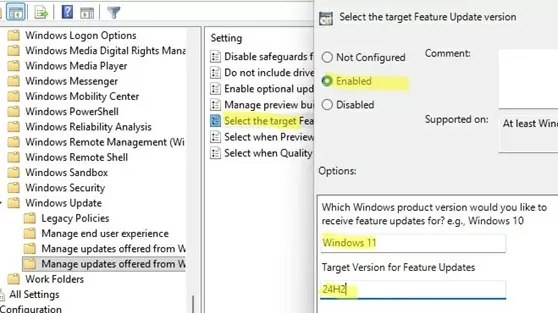
gpedit.msc); - Go to Computer Configuration -> Administrative Templates -> Windows Components -> Windows Update -> Manage Updates offered from Windows Update
- Enable the option Select the target Feature Update version. Specify the target Windows version and the build number you want to stay on.
- Enter
Windows 11in Which Windows product version would you like to receive feature updates for; - Set a target Windows 11 build number in Target Version for Feature Updates. For example,
24H2Specifying a newer version of Windows than what you currently have will automatically update the system to the target build. If the target version is no longer supported or is earlier than the current one, the value of this policy will be ignored. - Save the changes and restart your computer to update the GPO settings.
You can prevent your computer from updating to the next Windows build by setting the target build version in the registry. You can create these registry parameters manually with regedit.exe, deploy registry keys to domain computers using GPO, or create them using PowerShell:
if(!(Test-Path 'HKLM:\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate')){New-Item 'HKLM:\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate'}
Set-ItemProperty -Path 'HKLM:\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate' -Name TargetReleaseVersion -value '00000001' -Type DWord –Force
Set-ItemProperty -Path 'HKLM:\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate' -Name "ProductVersion" -value 'Windows 11' -Type String -Force
Set-ItemProperty -Path 'HKLM:\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate' -Name TargetReleaseVersionInfo -value '24H2' -Type String -Force
Your computer will now prevent automatic updates to the next Windows 11 build.
To allow future updates and put your computer on the standard release upgrade cycle, delete these registry keys using the following commands:
Remove-ItemProperty -Path 'HKLM:\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate' -Name ProductVersion
Remove-ItemProperty -Path 'HKLM:\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate' -Name TargetReleaseVersionInfo
Remove-ItemProperty -Path 'HKLM:\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate' -Name TargetReleaseVersion
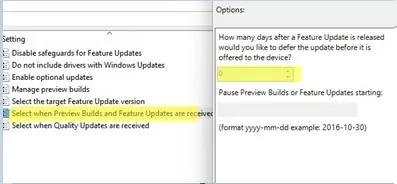
Another policy in this GPO section, called Select when Preview Builds and Feature Updates are received, allows you to defer installing a new feature update for up to 365 days after it becomes available in the general availability (GA) channel.
Disable Safeguard Holds for Feature Updates on Windows 11
Microsoft uses Safeguard Holds in Windows Update to temporarily block the delivery of new Feature Updates to devices when compatibility issues with the new build are detected. Microsoft can use safeguard holds to disable upgrades to the next Windows build for specific hardware configurations while engineers investigate bugs and develop fixes.
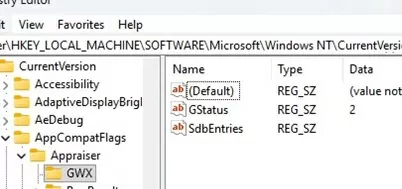
If a computer doesn’t automatically upgrade to the next build via Windows Update, check to see if Safeguard Hold is enabled. Open the registry editor and go to HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\AppCompatFlags\Appraiser\GWX . Check the value of the GStatus parameter:
2– the safeguard hold is not enabled for this device0– the build upgrade on a computer is blocked via a safeguard hold (in this case, the GatedBlockId and GatedBlockReason parameters will contain information about the problem ID and its description).
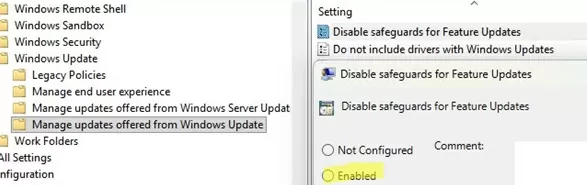
There is a Group Policy option Disable safeguard for Feature Updates that allows you to remove the block on delivering new Windows 11 builds caused by safeguard holds due to compatibility issues (under Computer Configuration -> Administrative Templates -> Windows Components -> Windows Update -> Manage update offered from Windows Update). If the policy is Enabled, it allows new Feature Updates to be delivered and installed through Windows Update despite an active safeguard hold.
You can enable this option via the registry:
reg add "HKLM\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate" /v DisableWUfBSafeguards /t REG_DWORD /d 1 /f
This policy allows your computer to download a new Windows build, but doesn’t guarantee that the installation will be successful.
As an alternative, you can manually upgrade the Windows build using the setup.exe command from the installation ISO image.
1 comment
🛑 Buggy Windows Update starts automatically ‘upgrading’ Windows 2022 servers to Windows Server 2025
Some enterprise customers have experienced their Windows Server 2022 servers being automatically upgraded to Windows Server 2025 without the necessary license or approval from system administrators.
☑️ KB5044284, if incorrectly targeted on Windows Server 2019 or 2022 machines, will result in an unwanted OS upgrade to the recently released Windows Server 2025. After upgrading to WS2025, the OS license status changes to “System not activated”. Uninstalling the update will not roll back to a previous version of the operating system. The previous OS version can only be restored from a backup.
☑️ This issue has been experienced by customers who use third-party solutions to automate the process of installing Windows security updates and patches (including when using WSUS).
🎯 To prevent unauthorized upgrades to Windows Server 2025, block the automatic installation of the KB5044284 update on hosts that are running Windows Server. It is also recommended to set the ProductVersion and TargetReleaseVersionInfo registry parameters to prevent further unwanted OS upgrades on server systems.
This method is used to prevent an automatic upgrade from Windows 10 to Windows 11.
✅ For example, to lock the current version on Windows Server 2022 host and prevent it from being upgraded, run the following command:
reg add HKLM\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate /f /v TargetReleaseVersion /t REG_DWORD /d 1
reg add HKLM\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate /f /v ProductVersion /t REG_SZ /d “Windows Server 2022”
reg add HKLM\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate /f /v TargetReleaseVersionInfo /t REG_SZ /d “21H2”
For Windows Server 2019, specify the correct version and build number 1809.
🤦♂️ This issue occurs because the Windows Server 2025 Feature Update (KB5044284) is misclassified by Microsoft as a security update, which causes it to be automatically installed by patch management tools.