Many Linux services (apache, nginx, etc.) can use keytab files for Kerberos authentication in Active Directory without entering a password. The keytab file keeps the names of Kerberos principals and the corresponding encrypted keys (obtained from Kerberos passwords). In this article we will show how to create a keytab file for the SPN of a linked Active Directory account using ktpass tool.
The most often, a separate Active Directory user account is created for a service that requires using a keytab file. However, you can also use a computer object to do it. Then the service name is bound to the account (ServicePrincipalName — SPN). SPN is used by Kerberos authentication to map a service instance to an AD account (this is why apps may authenticate as services even if they do not know a user name).
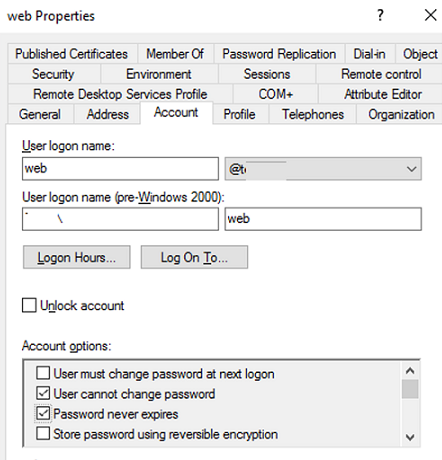
First, create a service account in AD and set a known password for it. You can create an account from the graphic ADUC console (dsa.msc) or using New-ADUser cmdlet in PowerShell (from PowerShell Active Directory module):
New-ADUser -Name "web" -GivenName "nginx web app" -SamAccountName "web" -UserPrincipalName "[email protected]" -Path "OU=Services,OU=Munich,OU=DE,DC=test,DC=com" –AccountPassword (ConvertTo-SecureString “Sup6r!Pa$s” -AsPlainText -force) -Enabled $true
Enable “User cannot change password” and “Password never expires“ options for the service account in the graphic console or in PowerShell:
Get-ADUser web|Set-ADUser -PasswordNeverExpires:$True -CannotChangePassword:$true
In the next step bind a service principal name (SPN) to the user account. You don’t need to perform this step separately, since ktpass does it automatically when creating a keytab file (I will do it to let you understand the process better).
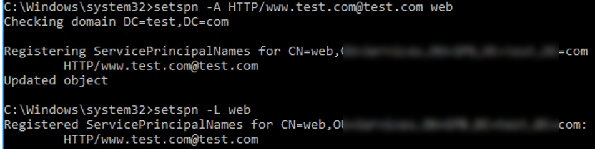
Bind the following SPN record to the web account:
setspn -A HTTP/[email protected] web
Display the list of SPN records associated with the AD user:
setspn -L web
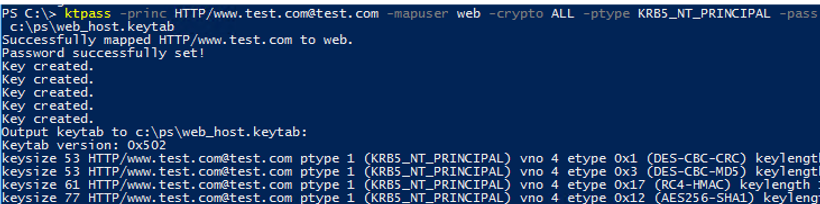
To create a keytab file, the following command is used:
ktpass -princ HTTP/[email protected] -mapuser web -crypto ALL -ptype KRB5_NT_PRINCIPAL -pass Sup6r!Pa$s -target mundc01.test.com -out c:\share\web.keytab
Successfully mapped HTTP/www.test.com to web. Password successfully set! Key created. Output keytab to c:\share\webt.keytab: Keytab version: 0x502 keysize 53 HTTP/[email protected] ptype 1 (KRB5_NT_PRINCIPAL) vno 4 etype 0x1 (DES-CBC-CRC) keylength 8 (0x73f868856e046449)
The command has created a keytab file (c:\share\webt.keytab) for the SPN record of the HTTP/[email protected] service. The SPN record is bound to the web account with the specified password.
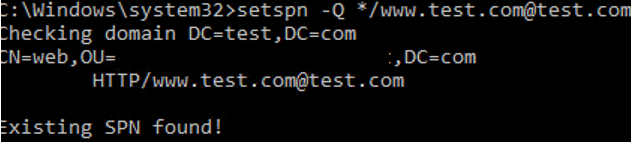
Make sure that the SPN record for the service has been successfully created (if you did not create it manually):
setspn -Q */[email protected]
You can see that the SPN record has been found (Existing SPN found!). It is bound to the web account.
Windows does not have built-in tools to view the contents of the keytab file. But if Java JRE is installed on your computer, you can use klist.exe included in the Java distribution package.
cd "c:\Program Files\Java\jre1.8.0_181\bin"
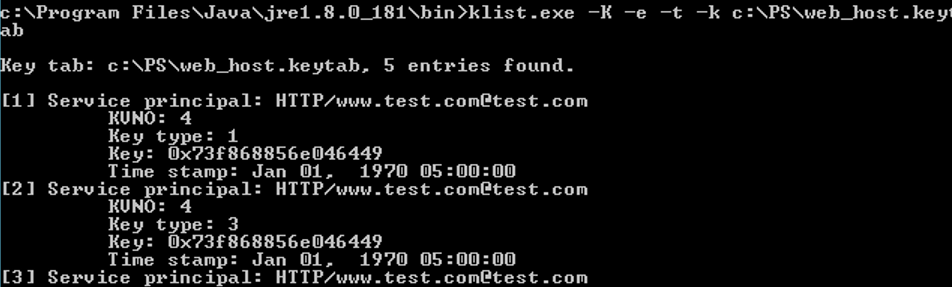
klist.exe -K -e -t -k c:\PS\web_host.keytab
Key tab: c:\PS\web_host.keytab, 5 entries found.
Let’s view the contents of the keytab file. SPNs, keys, timestamps, an encryption algorithm and a key version (KVNO — key version number) are specified here.
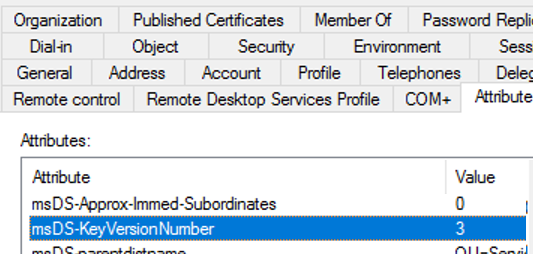
When creating a keytab file, ktpass increments the msDS-KeyVersionNumber attribute value of the user account (you can see it in the AD Attribute Editor) and uses the value as a KVNO in the keytab table.
If you change the account password, the attribute value is increased by one, and ll keytab entries with the previous KVNO become invalid (even if a new password completely matches the old one). If a user password in AD changes, you will have to generate a keytab file again.
A keytab file may keep keys of different SPNs. Additional SPNs and keys are added to the keytab file using ktpass parameters (-in,-setupn,-setpass).
A further use of the keytab file you have got depends on the service it is applied to. For example, you can use a keytab file for a transparent SSO user authentication in Zabbix. Also, don’t forget about keeping your keytab files secure (anybody who is able to read the contents of the keytab file will be able to use any keys from it).