You can use Group Policies (GPOs) to install and connect shared printers to specific users, computers, and groups in an Active Directory domain. In this article, we’ll look at how to automatically connect a shared printer for a domain user when they log on to a Windows computer.
Consider the following configuration: there are 3 departments in the organization. Users of each department must print documents on their own color network printer. As an administrator, you have to configure the automatic deployment of shared printers for users depending on their department.
Deploying Printers to Domain Users via Group Policy
Create three new security groups in AD (SharedPrinter_Sales, SharedPrinter_IT, SharedPrinter _Managers) and add the department users to them (you can automatically add users to domain groups by following the article “Creating a Dynamic Group in Active Directory”). You can create groups in the Active Directory Users and Computers console (dsa.msc, ADUC) or using the New-ADGroup cmdlet:
New-ADGroup "SharedPrinter_Sales" -path 'OU=Groups,OU=Paris,DC=woshub,DC=com' -GroupScope Global –PassThru
- Run the domain Group Policy editor (
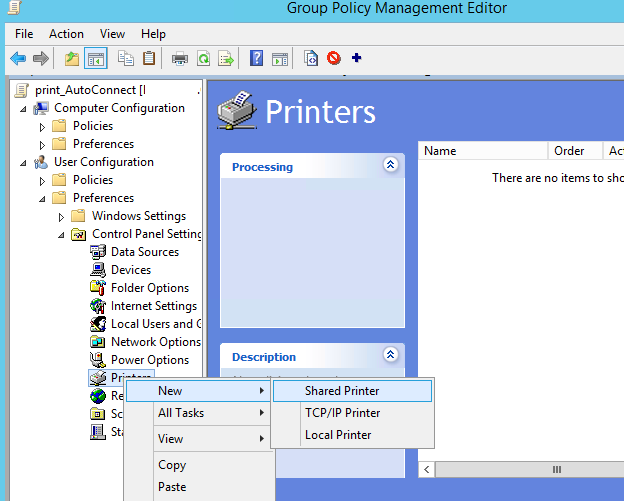
GPMC.msc), create a new policy print_AutoConnect and link it to the OU with the target users;If you have a small number of shared network printers in your domain (up to 30-50), you can configure them using a single GPO. If you have a complex domain structure with AD sites, Organizational Units (OUs) and delegate some AD administration tasks to branch administrators, it is better to create multiple printer deployment policies. For example, one policy for each AD site or Organizational Unit (OU). - Switch to the policy-editing mode and expand the User Configuration -> Preferences -> Control Panel Setting -> Printers. Create a new policy item by selecting New -> Shared Printer; If you want to connect a network printer by its IP address (directly, without a print server), select TCP/IP Printer.
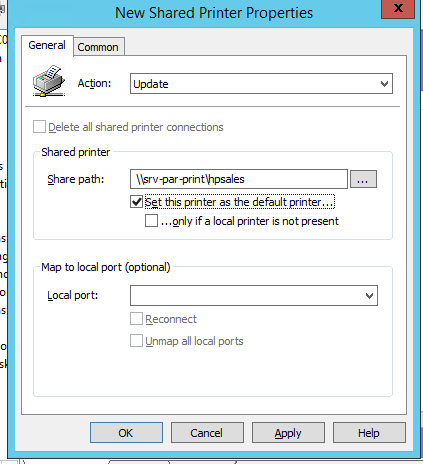
- Specify Update as an action. In the Shared Path field, enter the UNC address of your shared printer, for example,
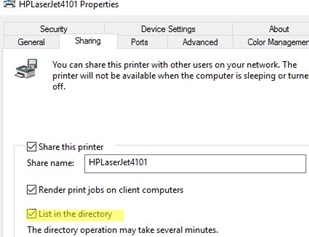
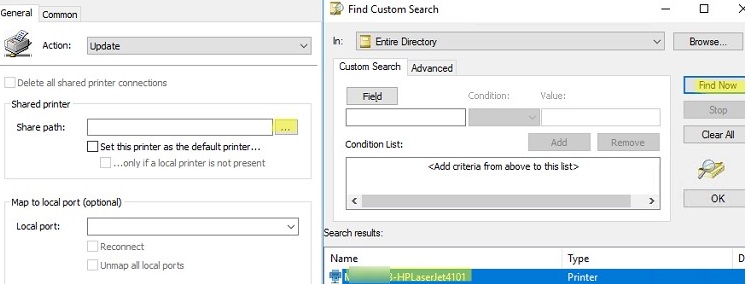
\\srv-par-print\hpsales(in my case all printers are connected to the print server\\srv-par-print). Here you can specify whether to set this printer as the default printer;You can publish your shared printers in Active Directory. To do this, enable the List in the Directory option in the printer settings on the Sharing tab.In this case, you can find your printer by searching AD (no need to enter the printer name manually). Just click the three dots button when you select your printer, click the Find now button, and select the dots printer name from the list.
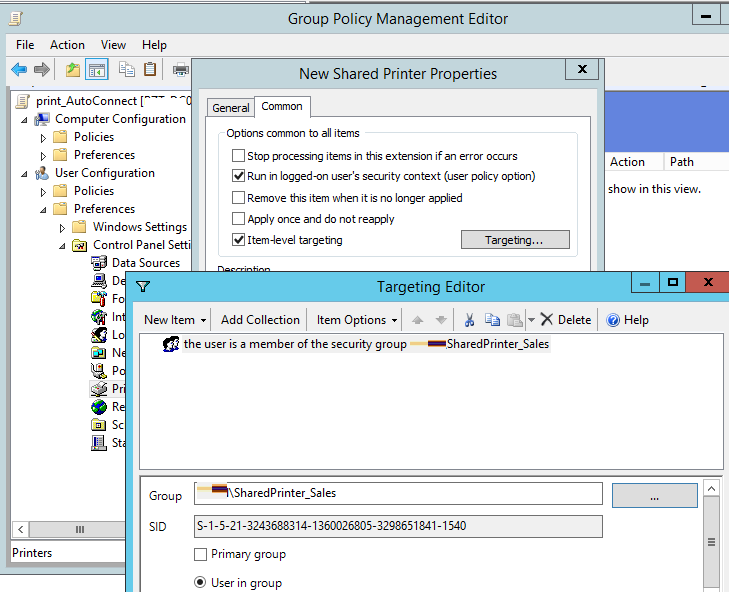
- Go to the Common tab and specify that the printer must be connected in the current user context (Run in logged-on user’s security context). Also, check the Item-level targeting option and click Targeting;
- Using GPP targeting, you need to specify this printer connection policy should only apply to SharedPrinter_Sales group members. To do it, go to New Item -> Security Group and enter SharedPrinter_Sales as a group name; Please note that this restriction doesn’t prevent a domain user from manually connecting this printer using File Explorer. To restrict access to the printer, you will have to change the printer security permissions on the print server and allow printing only for specific groups.
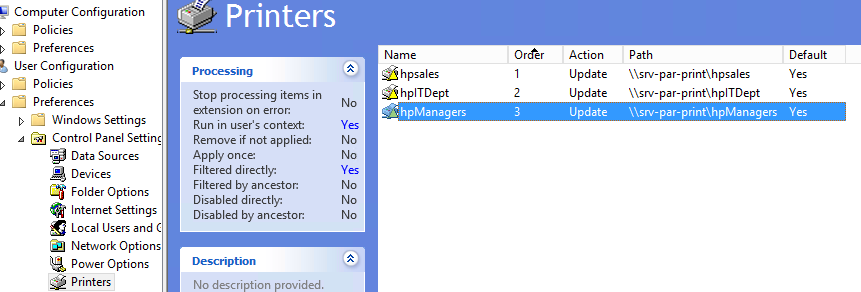
- Create network printer installation options for other user groups in the same way.
Check that shared network printers are now automatically connected when users log in to domain-joined Windows computers.
When using this Group Policy, new printers will only be installed for users if the appropriate print driver is already installed on their computers (drivers must be manually installed first or integrated directly into the Windows image).
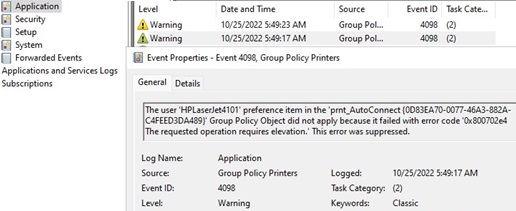
If no driver is installed for this printer, then the printer assigned via GPO will not be added to the user. In this case, an event with Event ID 4096 will appear in the Event Log -> Application log:
Source: Group Policy PrintersThe user 'HPLaserJet400' preference item in the 'prnt_AutoConnect}' Group Policy Object did not apply because it failed with error code '0x800702e4 The requested operation requires elevation.' This error was suppressed.
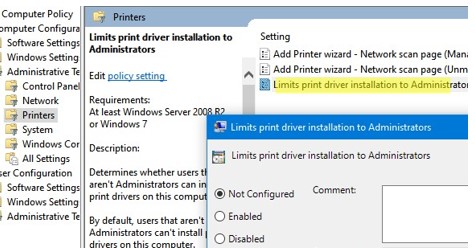
The fact is that now Windows users without administrator privileges cannot install a printer driver, even though the Point and Print Restriction policy is set.
Allow Non-Admin Users to Install Printer Drivers via GPO
In 2021, a critical vulnerability was discovered in the print spooler service, to fix which Microsoft changed the default behavior of Windows when installing print drivers (PrintNightmare CVE-2021-34527). Now users without administrator permissions cannot install printer drivers (KB5005033), including using the Point and Print Restriction GPO option. Windows drivers (signed and unsigned) should only be installed by administrators.
However, there is a workaround that will allow non-admin users to install the printer drivers. To do this, you need to change your GPO.
- Go to the following GPO section Computer Configuration -> Windows Settings -> Security Settings -> Local Policies -> Security Options. Disable the policy Devices: Prevent users from installing printer drivers;
- Now go to Computer Configuration -> Policies -> Administrative Templates -> System -> Driver Installation. Add printer device classes GUID in the Allow non-administrators to install drivers for these device setup classes parameter
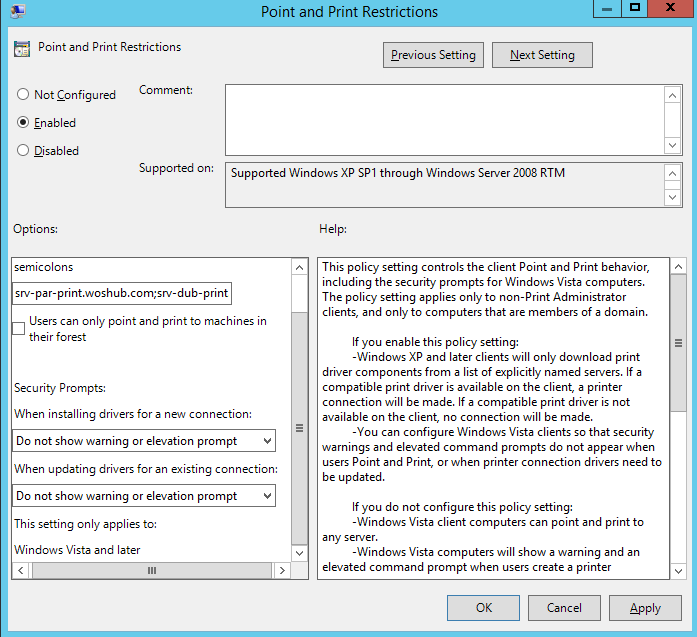
{4658ee7e-f050-11d1-b6bd-00c04fa372a7}and{4d36e979-e325-11ce-bfc1-08002be10318}. This will only allow the installation of print drivers; - Navigate to Computer Configuration -> Policy -> Administrative Templates -> Printers. Enable the policy Point and Print Restriction. Here you need to specify a list of your print servers (Users can only point and print to these servers) from which you are allowed to install print drivers. Select Don’t show warning or elevation prompt for the two remaining options;
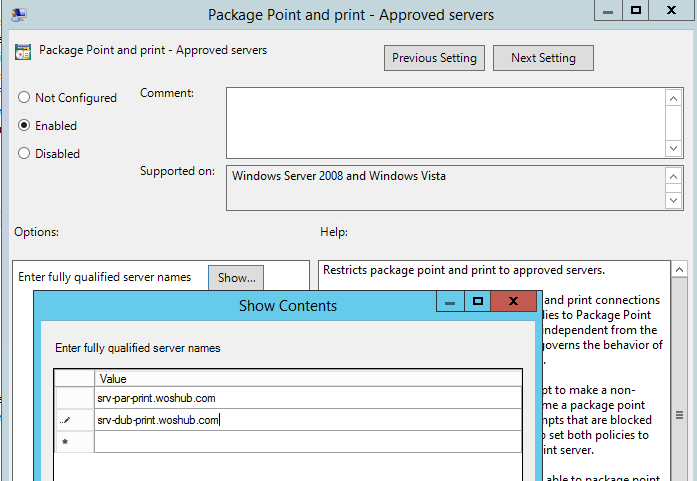
- Add a list of your trusted print servers to the parameter Package Point and print — Approved servers;
- (Now the most important point!!). To allow the installation of printer drivers without administrator privileges (for non-admin users), you need to temporarily change the value of the RestrictDriverInstallationToAdministrators registry parameter to 0.
On a standalone computer, you can change this registry parameter with the command:
reg add "HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows NT\Printers\PointAndPrint" /v RestrictDriverInstallationToAdministrators /t REG_DWORD /d 0 /f
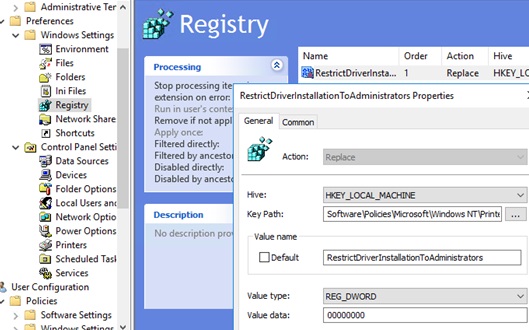
In order to change this registry parameter on a user’s computers via GPO, you need to create a new Group Policy Preferences rule under Computer Configuration -> Preferences -> Windows Settings -> Registry. Create a registry parameter with the following settings:
Action: Replace Hive: HKEY_LOCAL_MACHINE Key path: Software\Policies\Microsoft\Windows NT\Printers\PointAndPrint Value name: RestrictDriverInstallationToAdministrators Type: REG_DWORD Value: 0
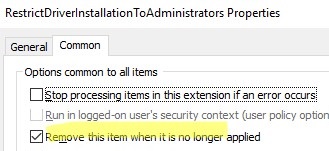
Go to the Common tab and enable the option Remove this item when it is no longer applied.
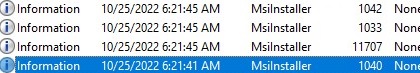
Now update the GPO settings on the clients (re-login or run the gpupdate /force command) and check that the drivers from the print servers are now installed automatically. MsiInstaller events should appear in the Application log:
EventID 1040 Beginning a Windows Installer transaction: C:\Windows\system32\spool\DRIVERS\x64\3\CIOUM64.MSI. Client Process Id: 7240.
Such a GPO will allow any non-admin user to install shared printers and drivers from specified print servers without prompting for elevation or any notifications.
You can run the logon script (only once) on the first logon for each user that sets the RestrictDriverInstallationToAdministrators = 1. The next time this script is run, it checks the value of RestrictDriverInstallationToAdministrators and, if it is 1, changes it to 0. This way, all printers assigned to the user via the GPO will be installed on the first login, and the RestrictDriverInstallationToAdministrators value will be automatically changed to a secure state.
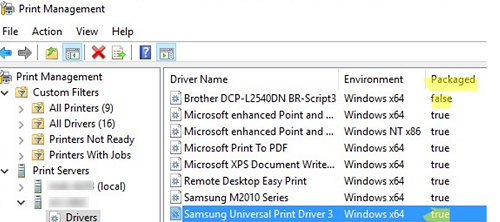
Note that only signed printer drivers (Package-aware v3 print drivers) can be installed this way (with the Packaged=True value in the Drivers section of the Print Management console – printmanagement.msc). See the article Unable to install non-package-aware print drivers.
If you try to install a printer with an unsigned driver via GPO, it won’t be deployed despite the RestrictDriverInstallationToAdministrators parameter:
The user 'HP2500' preference item in the 'prnt_AutoConnect {GUID}' Group Policy Object did not apply because it failed with error code '0x80070bcb The specified printer driver was not found on the system and needs to be downloaded.' This error was suppressed.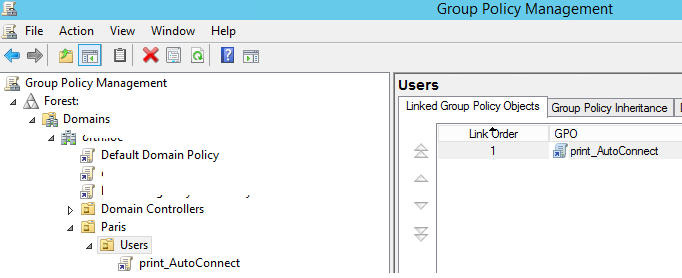
10 comments
Hi,
thank you for your manual.
One thing I would like to correct:
Under User Configuration -> Policy -> Administrative Templates -> Control Panel -> Printers -> exists no point Printer -> Point and Print Restriction
It exists only under Computer Configuration.
Computer Configuration -> Policy -> Administrative Templates -> Printers -> Point and Print Restriction This is correct path.
Fixed, thanks!
[…] Why can't you just use GPO?…. Deploying Printers to Domain Users and Computers with GPO | Windows OS Hub […]
It hasn’t worked, I keep getting the error “Group Policy Object did not apply because it failed with error code ‘0x800702e4′”
As always, great stuff. Thanks m8
Thanks! double check the unc printer name:
Group Policy Object did not apply because it failed with error code ‘0x80070709 The printer name is invalid.’ This error was suppressed
can someone explain why the first step is
Go to the following GPO section Computer Configuration -> Windows Settings -> Security Settings -> Local Policies -> Security Options. Enable the option Devices: Prevent users from installing printer drivers;
wouldn’t this immediately not allow domain users from installing drivers?
This I will like to know, and also, for me it only works if local admin logs onto pc first. After that logon every domain user is pulling printers from gpo.
1) Of course, the policy “Devices: Prevent users from installing printer drivers” should be Disabled. The guide fixed.
2) This can be caused by the PrintNightmare patch, which only allows drivers to be installed by users with local administrator permissions. The workaround is to temporarily set the registry option RestrictDriverInstallationToAdministrators to 0 before deploying a new printer to a computer.