The password policy, which is enabled by default in Active Directory, sets a maximum age for a user’s password. If the password age exceeds this value, it is considered expired, and the user must change it at the next login.
The administrator can extend the password expiration date when a domain user cannot change their expired password (for example, when a user connects to a corporate network via VPN or RDS) without enabling the Password never expires option for the account.
Use PowerShell to check the expiration date of the user’s password in AD:
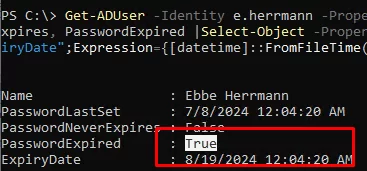
Get-ADUser -Identity e.herrmann -Properties msDS-UserPasswordExpiryTimeComputed, PasswordLastSet, PasswordNeverExpires, PasswordExpired |Select-Object -Property Name,PasswordLastSet, PasswordNeverExpires, PasswordExpired,@{Name="ExpiryDate";Expression={[datetime]::FromFileTime($_."msDS-UserPasswordExpiryTimeComputed")}}
In this case, the user’s password has expired( PasswordExpired=True ). The password expiration date is stored in a computed attribute named msDS-UserPasswordExpiryTimeComputed. This attribute’s value is calculated based on the value of the pwdLastSet parameter and the resulting password policy that applies to the user.
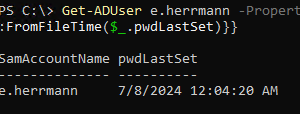
Get-ADUser e.herrmann -Properties pwdLastSet | select SamAccountName,@{Name="pwdLastSet";Expression={[datetime]::FromFileTime($_.pwdLastSet)}}
The pwdLastSet attribute contains the date in millisecond format (Windows NT time). However, it can take one of the following special values:
- 0 – reset the
pwdlastsetvalue (means the password was never set) - -1 – reset the user password change date to the current time
To change the value of the user attribute, use the Set-ADUser PowerShell cmdlet. First, you have to set 0 and then -1.
Set-ADUser e.herrmann -Replace @{pwdLastSet='0'}
Set-ADUser e.herrmann -Replace @{pwdLastSet='-1'}
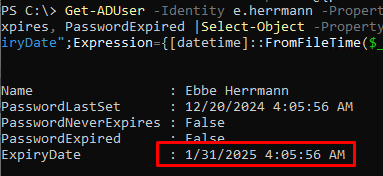
Now let’s check the user’s password change and expiration dates. The password change date has been changed to the current date, and the user’s password expiration date has been extended.
This method of extending user passwords can also be used if you plan to enable a domain password expiration policy after user passwords have been set to never expire or the PasswordNeverExpires option has been enabled. Enabling this policy will force all users to change their passwords simultaneously, potentially disrupting work processes Before applying this policy, extend the password expiration date for all users as instructed.