File Explorer process always runs with minimal (non-elevated) privileges in Windows. Even if you click the C:\Windows\explorer.exe executable file and try to start it in the ‘Run as administrator’ mode, it will not elevate privileges. In this article, we will look at a simple trick to run File Explorer on Windows with elevated privileges (as administrator).
Running the File Explorer Process on Windows as an Administrator
To run the Windows Explorer process with elevated privileges, you will first need to kill the unprivileged explorer.exe process.
- Open the Windows Task Manager (
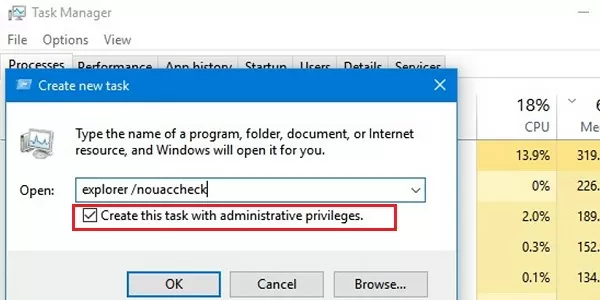
taskmgr.exe), go to the Details tab, find a kill theexplorer.exeprocess (End task); - Then in Task Manager select -> File -> Run New Task -> run the command:
explorer.exe /nouaccheck(make sure that the Create this task with administrative privileges option is enabled); - This will start the File Explorer process with administrator privileges. How can you be sure of this?
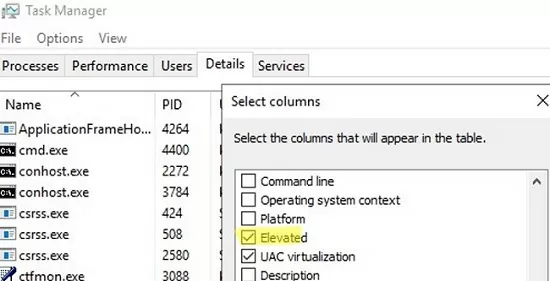
- On the Details tab, right-click the title of the process list and choose Select Columns;
- Check the Elevated option;
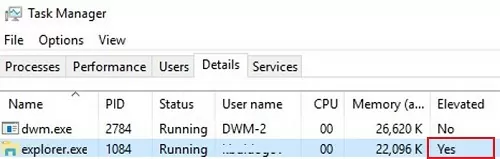
- Now you can see that the explorer.exe process is running in privileged mode (
Elevated=Yes).
You can also run the elevated explorer.exe process from the PowerShell console (be sure to run powershell.exe as an administrator):
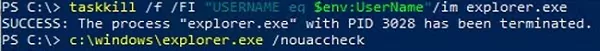
- Kill the running low-privileged explorer.exe process:
taskkill /f /FI "USERNAME eq $env:UserName"/im explorer.exe - Run the privileged explorer.exe:
c:\windows\explorer.exe /nouaccheck - The new explorer process will inherit the elevated access token that is used to run the powershell.exe console.
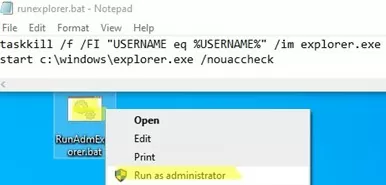
You can create the following BAT file on your desktop to quickly run File Explorer with administrator privileges:
taskkill /f /FI "USERNAME eq %USERNAME%" /im explorer.exe
start c:\windows\explorer.exe /nouaccheck
In order to disable this behavior, you must modify the AutoRestartShell parameter in the registry:
$path = 'HKLM:SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon'
New-ItemProperty -Path $path -Name AutoRestartShell -Type Dword -Value 0 -Force | Out-Null
Windows will still kill the elevated process when you run the following command for the first time:
taskkill /f /FI "USERNAME eq $env:UserName" /im explorer.exe ; c:\windows\explorer.exe /nouaccheck
But if you start it again, the privileged explorer.exe will survive. 👌
When you have finished your task, remember to allow the Explorer shell to restart:
New-ItemProperty -Path $path -Name AutoRestartShell -Type Dword -Value 1 -Force | Out-Null
taskkill /f /FI "USERNAME eq $env:UserName" /im explorer.exe
Fix: You Don’t Have Permission to Access Folder
Let’s have a look at a common scenario where an Explorer process with administrator privileges can be particularly useful
In some cases, you may need to open the system or other users’ profile folders or edit protected system files by using Explorer running as an account that has been added to the local Administrators group (or even under the built-in Windows administrator). If you try to open such a directory or file in the current Explorer context, a User Account Control (UAC) warning window will appear, asking you to grant access and elevate privileges.
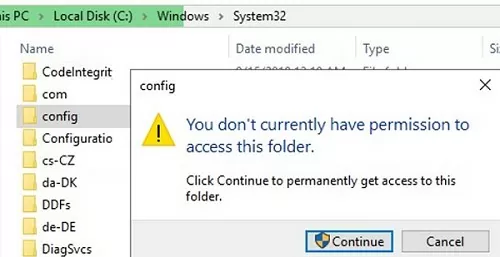
For example, try using Explorer to open the system directory C:\Windows\System32\Config. The UAC prompt should appear, informing you that you are not allowed to access the directory:
You don’t currently have permission to access this folder. Click Continue to permanently get access to this folder.
If your account has local administrator permissions, you can use UAC to elevate privileges by clicking Continue.
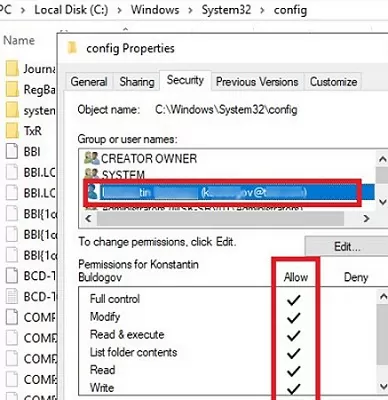
When you click Continue, UAC temporarily elevates the privileges of your explorer.exe process and grants your account Full Control NTFS permissions on the folder.
Known issues with this approach:
After performing such an operation, your account will be explicitly added to the NTFS folder permissions. Even though you only wanted to view the contents of the directory, not change its ACL! If this Windows Server host is managed by more than one administrator, then the folder ACL will be constantly increasing. This is because, when accessing the folder, any administrator will change the directory ACL.
\\mun-fs01\docs\) rather than locally. In this case, there is no need to elevate permissions when accessing the shared folder. Accordingly, NTFS ACLs won’t be modified.This pop-up UAC notification becomes annoying if you are actively managing system files or shared folders. To avoid completely disabling UAC in Windows, you can temporarily run File Explorer as an administrator.
Be sure to restart explorer.exe in Normal mode when you have finished working with protected or user folders.
This trick of running the Windows Explorer process with elevated privileges works in Windows Server 2016/2019/2022 as well as in all builds of Windows 10/11.
CreateExplorerShellUnelevatedTask scheduler task.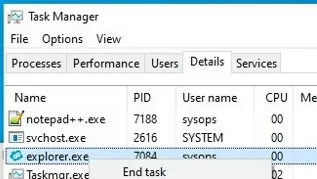
12 comments
I tried this from a Windows 10 LTSB 2015 machine and it didn’t work. I was excited to see the article because you are correct this is a pain. Do you have any suggestions?
This trick only works on Windovs Server 2012 R2
Ok, that makes sense then. Thanks.
Not working on Windows Server 2016. Always starts explorer.exe without Elevated privileges
Try this – start an elevated command prompt, open task manager, right-click explorer.exe in details pane, and ‘End task’. Then, switch to the command prompt and run explorer. Seems to prevent the auto-restart of explorer.exe when you try it the above way.
What you need to do on W10/WS2016 and newer is:
– open Task Manager
– kill Explorer.exe process
– click the File menu, select Start new task, type: explorer /nouaccheck, be sure to tick the ‘Create this task with administrative privileges’
– click OK, there’s your elevated Explorer again
worked beautifully thanks brskie
Reading the title i thought it would be a way, as being a simple user, launching explorer as an administrator…
So i tried the trick New-ItemProperty -Path “HKCU:\Software\Policies\Microsoft\Windows\CurrentVersion\Explorer” -Name ShowRunasDifferentuserinStart -Value 1 -PropertyType DWORD -Force but Explorer key doesn’t exist (win10 20H2) and i don’t have right to create it, and, after the modification of GPEDIT.msc, as the explorer is not available in the start menu to run it as another user this is not possible either (knowing that it would have to be able to mix the two techniques when you have to close the explore … so no solution)
This trick assumes that you are logon Windows with an account that is a member of the local Administrators group.
ExplorerShellUnelevated
\CreateExplorerShellUnelevatedTask
S-1-5-18
false
false
false
IgnoreNew
6
true
PT10M
PT1H
true
false
true
C:\Windows\explorer.exe
/NOUACCHECK (NO|UAC|CHECK)
These commands will terminate the explorer.exe process for
the current user and start a new one, which will inherit
the elevated access token that powershell.exe is run with.
CreateExplorerShellUnelevatedTask is a system task created by Windows to prevent users and apps from running Windows Explorer process elevated
Thank you, this is a great trick but unfortunately it seems it does not work anymore on Windows 11 PCs, any other way to run explorer.exe elevated working on Windows 11?