In a previous article, we showed how to configure proxy settings in Windows via GPO. However, even non-admin users can manually change the proxy settings on their computers. In this article, we’ll look at how to prevent users from changing proxy server settings in Windows using Group Policy.
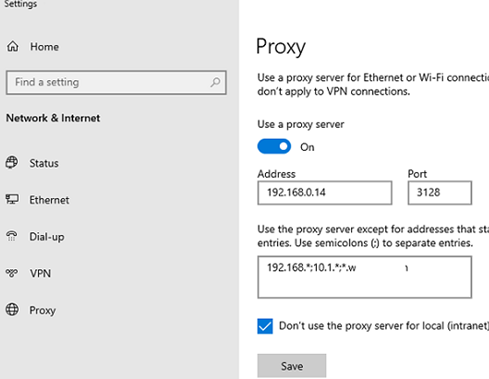
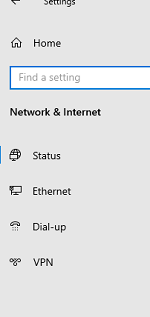
After an administrator has assigned the proxy server settings to users through the GPO, the user can change them at any time. In Windows 10 and 11, you can change proxy settings from the Settings -> Network and Internet -> Proxy (ms-settings:network-proxy).
Although the proxy settings will be overwritten every 90 minutes during a Group Policy refresh cycle, sometimes you need to completely prevent domain users from changing the proxy settings that are set using the GPO.
- Open the domain Group Policy Management Console (
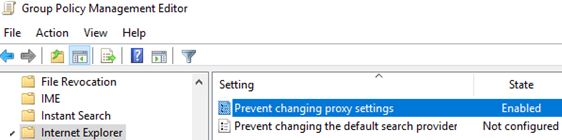
gpmc.msc) and edit your GPO with proxy settings; - Go to the following GPO section User Configuration -> Administrative Templates -> Windows Components -> Internet Explorer;
- Find the Prevent changing proxy settings and set it to Enabled;There is a similar policy in the Computer Configuration section. The GPO option in this section will allow you to prevent changing proxy settings for all users of the computer.
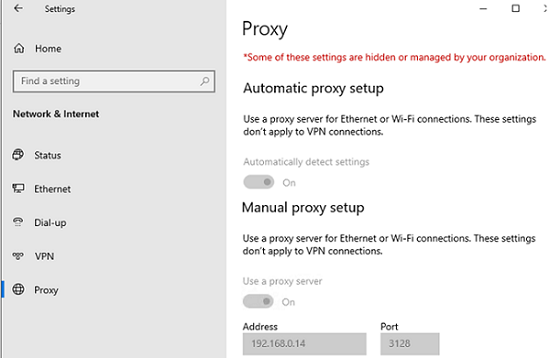
- After updating the policies on the client, the Windows proxy settings page will display the message “
Some of these settings are hidden or managed by your organization”. In this case, the text fields with proxy server options will become unavailable for editing (greyed out);
This policy applies to all browsers that use Windows proxy settings (Google Chrome, Microsoft Edge, Internet Explorer, and Mozilla Firefox with the Use system proxy settings mode) in both Windows 10 and Windows 11.
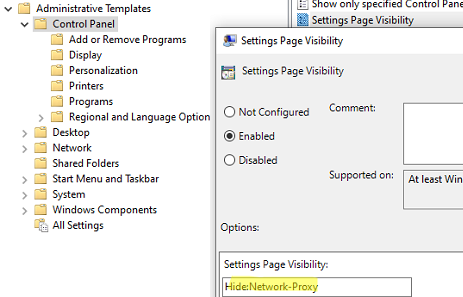
On Windows 10/11, you can hide the proxy settings options on the Settings panel. To do this, enable the Settings Page Visibility policy in the User (or Computer) section Configuration –> Administrative Templates –> Control Panel.
To hide the proxy settings page, you need to specify the following text in the policy settings:
Hide:Network-Proxy
The tab with proxy settings in the Settings app will be hidden after updating the local policy settings.
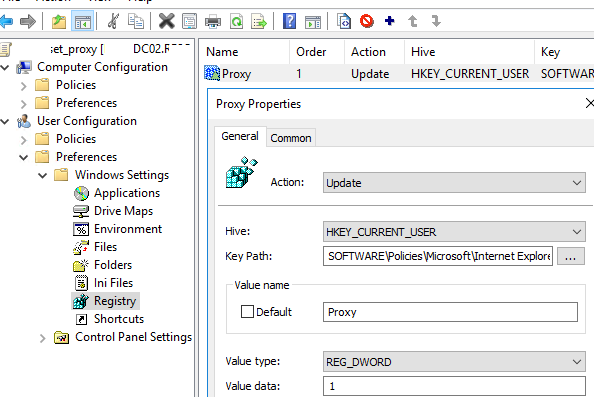
You can prevent changing proxy settings using the GPO option discussed above or through the registry. You can make changes to the registry via Group Policy Preferences (User Configuration -> Preferences -> Windows Settings -> Registry). Create a new registry value under the specified GPO with the following settings:
- Hive:
HKEY_CURRENT_USER - Key Path:
SOFTWARE\Policies\Microsoft\Internet Explorer\Control Panel - Value name:
Proxy - Value type:
REG_DWORD - Value data:
1
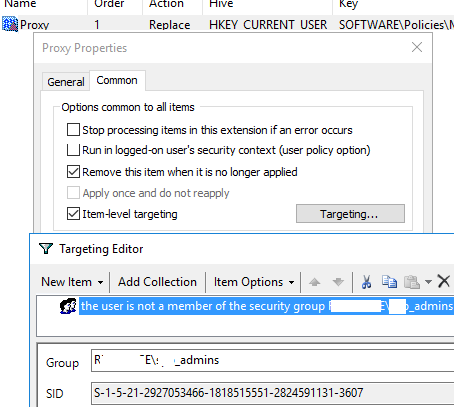
In order to prevent the proxy settings lock policy from being applied to local computer administrators, you need to configure Item-Level Targeting.
To do this, go to the Common tab in the registry parameter options, enable the Remove this item when it is no longer applied option. Then enable the Item-Level Targeting option and click the Targeting button. Create a new rule: New Item -> Security Group -> Item option -> Is not and specify the name of the group for which this policy should not be applied. In our example, this is the mun_admins group, which was added on computers to the local administrators’ group through the GPO.
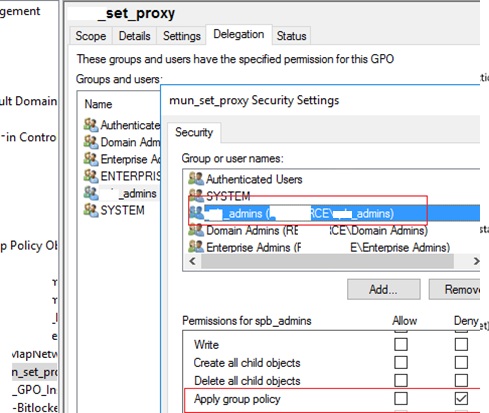
You can also prevent this policy from being applied to a specific group by using GPO security filtering. Add the groups to which the GPO should not apply on the Delegation tab in the Group Policy Management Console (for example, mun_admin) and set the Deny for these groups in the Apply Group Policy permissions.
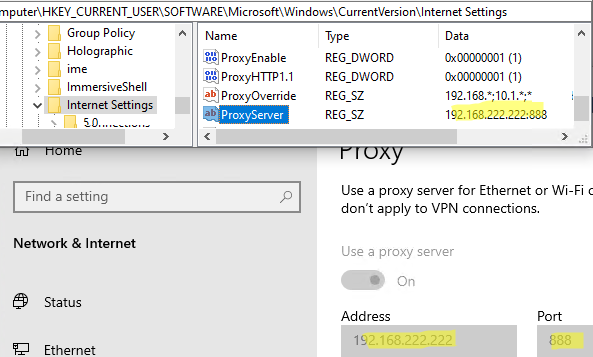
Please note that a user with local admin permissions can still edit the proxy server settings directly in their registry key HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings.
To change the proxy server address, just edit the value of the ProxyServer registry entry. Proxy settings made in this registry key are applied in Windows immediately.
2 comments
hi, does this cover IE in Windows 10 1709?
In Windows 1803 and 1809, these IE 11 policy settings are applied normally.